Gives criticality score for an open source project
Project description
Open Source Project Criticality Score (Beta)
This project is maintained by members of the Securing Critical Projects WG.
Goals
-
Generate a criticality score for every open source project.
-
Create a list of critical projects that the open source community depends on.
-
Use this data to proactively improve the security posture of these critical projects.
Criticality Score
A project's criticality score defines the influence and importance of a project. It is a number between 0 (least-critical) and 1 (most-critical). It is based on the following algorithm by Rob Pike:
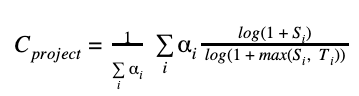
We use the following parameters to derive the criticality score for an open source project:
| Parameter (Si) | Weight (αi) | Max threshold (Ti) | Description |
|---|---|---|---|
| created_since | 1 | 120 | Time since the project was created (in months) |
| updated_since | -1 | 120 | Time since the project was last updated (in months) |
| contributor_count | 2 | 5000 | Count of project contributors (with commits) |
| org_count | 1 | 10 | Count of distinct organizations that contributors belong to |
| commit_frequency | 1 | 1000 | Average number of commits per week in the last year |
| recent_releases_count | 0.5 | 26 | Number of releases in the last year |
| closed_issues_count | 0.5 | 5000 | Number of issues closed in the last 90 days |
| updated_issues_count | 0.5 | 5000 | Number of issues updated in the last 90 days |
| comment_frequency | 1 | 15 | Average number of comments per issue in the last 90 days |
| dependents_count | 2 | 500000 | Number of project mentions in the commit messages |
Usage
The program only requires one argument to run, the name of the repo:
$ pip3 install criticality-score
$ criticality_score --repo github.com/kubernetes/kubernetes
name: kubernetes
url: https://github.com/kubernetes/kubernetes
language: Go
created_since: 79
updated_since: 0
contributor_count: 3664
org_count: 5
commit_frequency: 102.7
recent_releases_count: 76
closed_issues_count: 2906
updated_issues_count: 5136
comment_frequency: 5.7
dependents_count: 407254
criticality_score: 0.9862
You can add your own parameters to the criticality score calculation. For
example, you can add internal project usage data to re-adjust the project's
criticality score for your prioritization needs. This can be done by adding
the --params <param1_value>:<param1_weight>:<param1_max_threshold> ...
argument on the command line.
Authentication
Before running criticality score, you need to
create a GitHub access token
and set it in environment variable GITHUB_AUTH_TOKEN.
This helps to avoid the GitHub's
api rate limits
with unauthenticated requests.
# For posix platforms, e.g. linux, mac:
export GITHUB_AUTH_TOKEN=<your access token>
# For windows:
set GITHUB_AUTH_TOKEN=<your access token>
Formatting Results
There are three formats currently: default, json, and csv. Others may be added in the future.
These may be specified with the --format flag.
Public Data
If you're only interested in seeing a list of critical projects with their
criticality score, we publish them in csv format.
This data is available on Google Cloud Storage and can be downloaded via the
gsutil
command-line tool or the web browser
here.
NOTE: Currently, these lists are derived from projects hosted on GitHub ONLY. We do plan to expand them in near future to account for projects hosted on other source control systems.
$ gsutil ls gs://ossf-criticality-score/*.csv
gs://ossf-criticality-score/c_top_200.csv
gs://ossf-criticality-score/cplusplus_top_200.csv
gs://ossf-criticality-score/go_top_200.csv
gs://ossf-criticality-score/java_top_200.csv
gs://ossf-criticality-score/js_top_200.csv
gs://ossf-criticality-score/php_top_200.csv
gs://ossf-criticality-score/python_top_200.csv
gs://ossf-criticality-score/rust_top_200.csv
This data is generated using this generator script. For example, to generate a list of top 200 C language projects, run:
$ python3 -u -m criticality_score.generate \
--language c --count 200 --sample-size 5000
Contributing
If you want to get involved or have ideas you'd like to chat about, we discuss this project in the Securing Critical Projects WG meetings.
See the Community Calendar for the schedule and meeting invitations.
See the Contributing documentation for guidance on how to contribute.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Hashes for criticality_score-1.0.4-py3-none-any.whl
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | f0883a0dc05d9800847b01cc4e05a59f4edc3000db2d832d3b47ef0cb4764991 |
|
| MD5 | 9f8d97186cab98bb1d131334404a8d4a |
|
| BLAKE2b-256 | e03a7a63acc6949d4eb40d399e49505684a04fb23140a847093cdc70a44d4e00 |












