Scan the vulnerability of Docker images stored in ECR
Project description
ECRanner


This is that scan the vulnerability of Docker images stored in ECR.
Table of contents
Feature
- Pull Docker Image From ECR
- Support multi account
- Vulnerability Scan
- Trivy detects software (OS package and application library) vulnerabilities in Docker Image
- Slack Integration
-
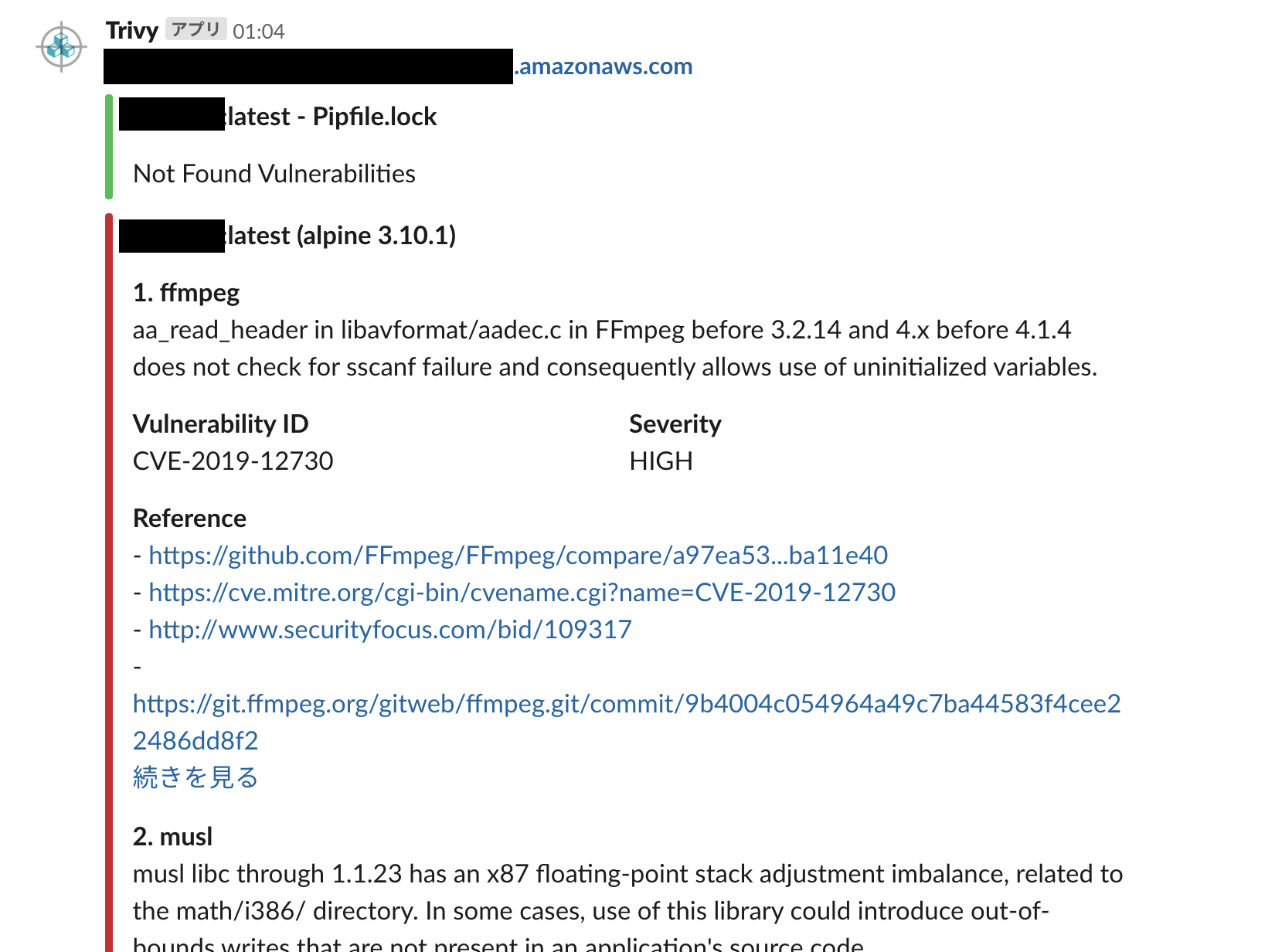
Push vulnerability information to Slack. Slack UI is as following:
-
Get Started
Install Prerequirements
- Trivy
- Git (Used with Trivy)
Install ECRanner
pip install ecranner
Write ecranner.yml
A ecranner.yml looks like this:
aws:
stg:
account_id: xxxxxxxxx
region: us-east-1
aws_access_key_id: xxxxxxxxx
aws_secret_access_key: xxxxxxxxx
images:
- image:latest
- image:1.0-dev
prod:
account_id: xxxxxxxxx
region: us-east-1
aws_access_key_id: xxxxxxxxx
aws_secret_access_key: xxxxxxxxx
images:
- image:1.4
- image:5.3
trivy:
path: ~/user/.local/bin/trivy
options: --severity CRITICAL -q
Execute
ecranner
You execute the above and then output the scan result to the console as follows:
[ { 'Target': 'image_name:latest'
'(alpine 3.10.1)',
'Vulnerabilities': [ { 'Description': 'aa_read_header in '
'libavformat/aadec.c in FFmpeg '
'before 3.2.14 and 4.x before 4.1.4 '
'does not check for sscanf failure '
'and consequently allows use of '
'uninitialized variables.',
'FixedVersion': '4.1.4-r0',
'InstalledVersion': '4.1.3-r1',
'PkgName': 'ffmpeg',
'References': [ 'https://git.ffmpeg.org/gitweb/ffmpeg.git/shortlog/n4.1.4',
'https://github.com/FFmpeg/FFmpeg/commit/ed188f6dcdf0935c939ed813cf8745d50742014b',
'https://github.com/FFmpeg/FFmpeg/compare/a97ea53...ba11e40',
'https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-12730',
'http://www.securityfocus.com/bid/109317',
'https://git.ffmpeg.org/gitweb/ffmpeg.git/commit/9b4004c054964a49c7ba44583f4cee22486dd8f2'],
'Severity': 'HIGH',
'Title': '',
'VulnerabilityID': 'CVE-2019-12730'}
Configuration Parameter
Specify to use parameter in ecranner.yml.
Command options
| option | required | default | description |
|---|---|---|---|
| -f, --file | false | ./ecranner.yml |
Filepath to configuration in YAML. Specify this option if you change configuration filename. |
| --env-file | false | ./.env |
Specify .env file path. Automatically load .env file if this file is found in current directory. |
| --slack | false | N/A | Send the scan result to Slack. If you use this option, set incoming webhooks url as system environment variable like this: export SLACK_WEBHOOK=https://xxxxxxxxxx |
| --rm | false | N/A | Remove images after scan with Trivy. |
| -q, --quiet | false | N/A | Suppress logging message. |
| --no-cache | false | N/A | Implement in the future, so you can not use this option Disable to store cache. This command does not use cache, but Trivy command use cache. |
| -h, --help | false | N/A | Show command option usage. |
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file ecranner-0.0.2.tar.gz.
File metadata
- Download URL: ecranner-0.0.2.tar.gz
- Upload date:
- Size: 15.6 kB
- Tags: Source
- Uploaded using Trusted Publishing? No
- Uploaded via: poetry/0.12.17 CPython/3.7.4 Darwin/18.7.0
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
20dfb0b38cfe7508c868964bbbd720f557ee22582f7afbd31d7f8bb1c6a5bb13
|
|
| MD5 |
3751daf207f22e869a5df07d96df9ef0
|
|
| BLAKE2b-256 |
28e5e1a633e3ab8a25e601d88aba315e5d8e59b271d84ddccf991ad1d6a796b1
|
File details
Details for the file ecranner-0.0.2-py3-none-any.whl.
File metadata
- Download URL: ecranner-0.0.2-py3-none-any.whl
- Upload date:
- Size: 17.9 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: poetry/0.12.17 CPython/3.7.4 Darwin/18.7.0
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
2bd0c1250c77c95815d39adeccc9031d5a152c521ee054f27e352bd87de9958a
|
|
| MD5 |
aab966f924ba075323c39065b8a53e00
|
|
| BLAKE2b-256 |
e2b3979ccf502aace24dc52a06572e8e83c22d948161495ce8d91ab1336a7487
|