Fast elliptic curve digital signatures
Project description

About
This is a python package for doing fast elliptic curve cryptography, specifically digital signatures.
Supported Primitives
Curves
P192 (
fastecdsa.curve.P192)P224 (
fastecdsa.curve.P224)P256 (
fastecdsa.curve.P256)P384 (
fastecdsa.curve.P384)P521 (
fastecdsa.curve.P521)secp256k1 (bitcoin curve) (
fastecdsa.curve.secp256k1)
Hash Functions
SHA1 (
hashlib.sha1)SHA224 (
hashlib.sha224)SHA256 (SHA2) (
hashlib.sha256)SHA384 (
hashlib.sha384)SHA512 (
hashlib.sha512)
Performance
Currently it does basic point multiplication significantly faster than the ecdsa
package. You can see the times for 1,000 signature and verification operations below,
fast.py corresponding to this package and regular.py corresponding
to ecdsa package.
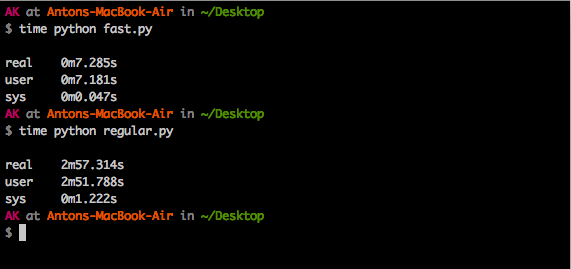
As you can see, this package in this case is ~25x faster.
Installing
You can use pip: $ pip install fastecdsa or clone the repo and use
$ python setup.py install. Note that you need to have a C compiler.
You also need to have GMP on your system as the underlying
C code in this package includes the gmp.h header (and links against gmp
via the -lgmp flag). On debian you can install all dependencies as follows:
$ sudo apt-get install python-dev libgmp3-devUsage
Generating Keys
You can use this package to generate keys if you like. Recall that private keys on elliptic curves are integers, and public keys are points i.e. integer pairs.
from fastecdsa import keys, curve
# generate a private key for curve P256
priv_key = keys.gen_private_key(curve.P256)
# get the public key corresponding to the private key we just generated
pub_key = keys.get_public_key(priv_key, curve.P256)
(Qx, Qy) = pub_key # recall that pub_key is simply an integer pairSigning and Verifying
Some basic usage is shown below:
from fastecdsa import curve, ecdsa, keys
from hashlib import sha384
m = "a message to sign via ECDSA" # some message
''' use default curve and hash function (P256 and SHA2) '''
private_key = keys.gen_private_key(curve.P256)
public_key = keys.get_public_key(private_key, curve.P256)
# standard signature, returns two integers
r, s = ecdsa.sign(m, private_key)
# should return True as the signature we just generated is valid.
valid = ecdsa.verify((r, s), m, public_key)
''' specify a different hash function to use with ECDSA '''
r, s = ecdsa.sign(m, private_key, hashfunc=sha384)
valid = ecdsa.verify((r, s), m, public_key, hashfunc=sha384)
''' specify a different curve to use with ECDSA '''
private_key = keys.gen_private_key(curve.P224)
public_key = keys.get_public_key(private_key, curve.P224)
r, s = ecdsa.sign(m, private_key, curve=curve.P224)
valid = ecdsa.verify((r, s), m, public_key, curve=curve.P224)Security
No known current issues. Timing side challenges are mitigated via Montgomery point multiplication. Nonces are generated per RFC6979.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
File details
Details for the file fastecdsa-1.1.3.tar.gz.
File metadata
- Download URL: fastecdsa-1.1.3.tar.gz
- Upload date:
- Size: 14.9 kB
- Tags: Source
- Uploaded using Trusted Publishing? No
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
affd7c5cb0b878972a97b8090e464a8b66eacf0c959f205dad7b23b9e007ba63
|
|
| MD5 |
035b3cef1ac9c87856aecea74774b310
|
|
| BLAKE2b-256 |
2c3315b8ec2d31b79c20a9f5e5739a7300abb121026f99990e169a8821b404f4
|











