Cloudfront,ALB and API Gateway with Automated WAF
Project description
AWS WAF Solution
This CDK Construct modify and rebuild from Cloudfront with Automated WAF.
The solution use CDK construct to automatically deploy a set of AWS WAF rules design to filter common web-based attacks.Users can select from preconfigured protective features that define the rules included in an AWS WAF web access control list (web ACL). After the solution deploys, AWS WAF begins inspecting web requests to the user’s existing Amazon CloudFront distributions、Application Load Balancers、API Gateway, and blocks them when applicable.
What is difference
- The project is CDK Construct which is handy to integrate into your existing CDK project.
- Support count mode for testing WAF rule, see API.md.
- Support Application Load Balancers and API Gateway (The origin repository doesn't support ALB any more in next release, see issue )
- AWS Shield Advance is optional (The origin repository enforce to enable it)
Construct Props
Ref API Reference
CloudFront Usage
# Example automatically generated from non-compiling source. May contain errors.
env_uSEast1 = {
"region": "us-east-1",
"account": process.env.CDK_DEFAULT_ACCOUNT
}
stack_test1 = cdk.Stack(app, "TestStackAutomatedWafForCloudFront", env=env_uSEast1)
AutomatedWaf(stack_test1, "AutomatedWaf",
waf2_scope=Waf2ScopeOption.CLOUDFRONT,
resource_naming_prefix="CloudFront_ApiGW",
error_threshold=55,
request_threshold=300,
block_period=60,
log_level=LogLevel.DEBUG
)
Notice the WAF region must be us-east-1 for CloudFront.
After deploying, it need to do two things on AWS Management Console.
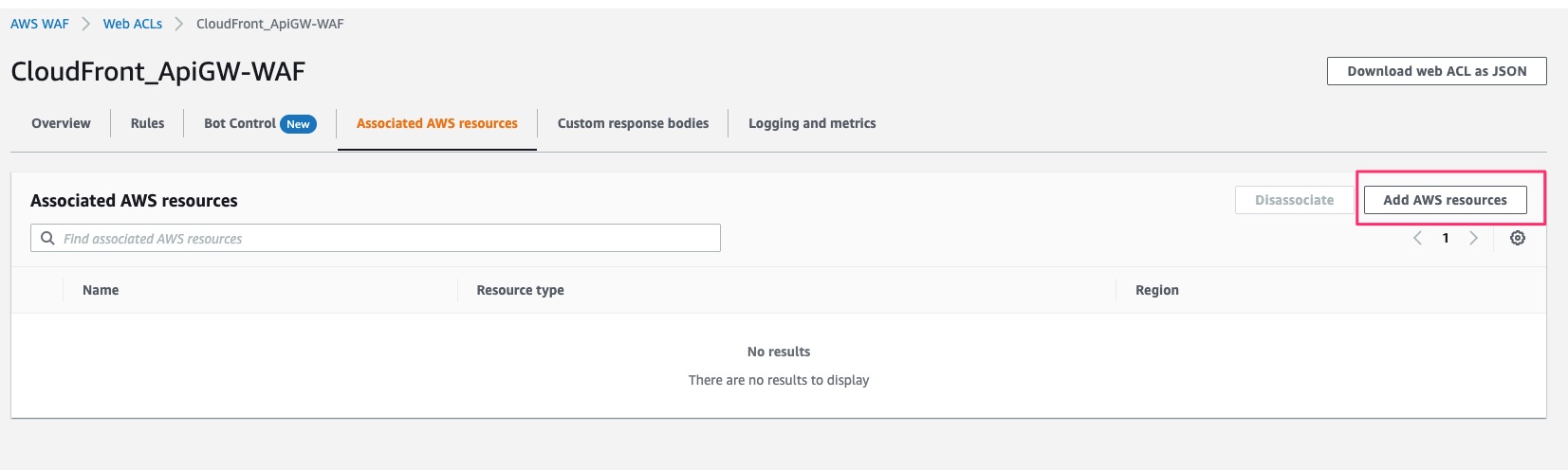
1. Attach Cloudfront to WAF.
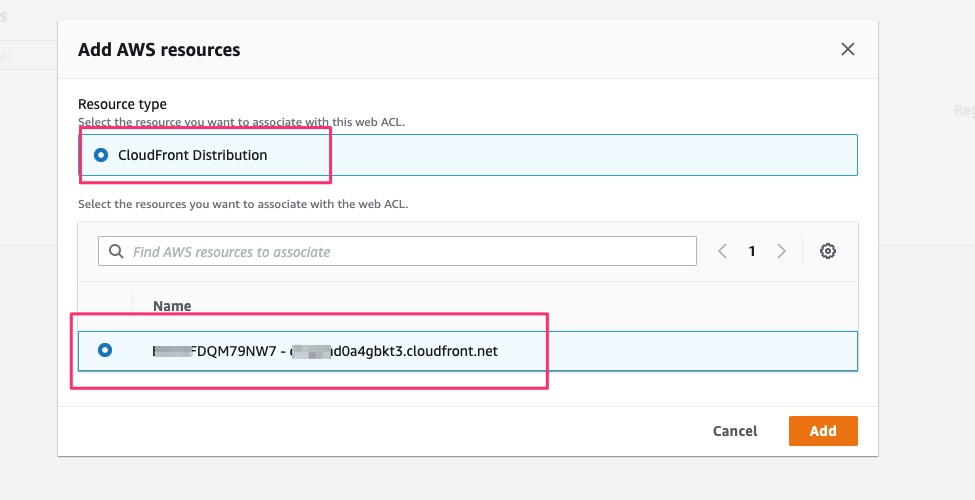
Click add AWS Resources
Select existing CloudFront Distribution.
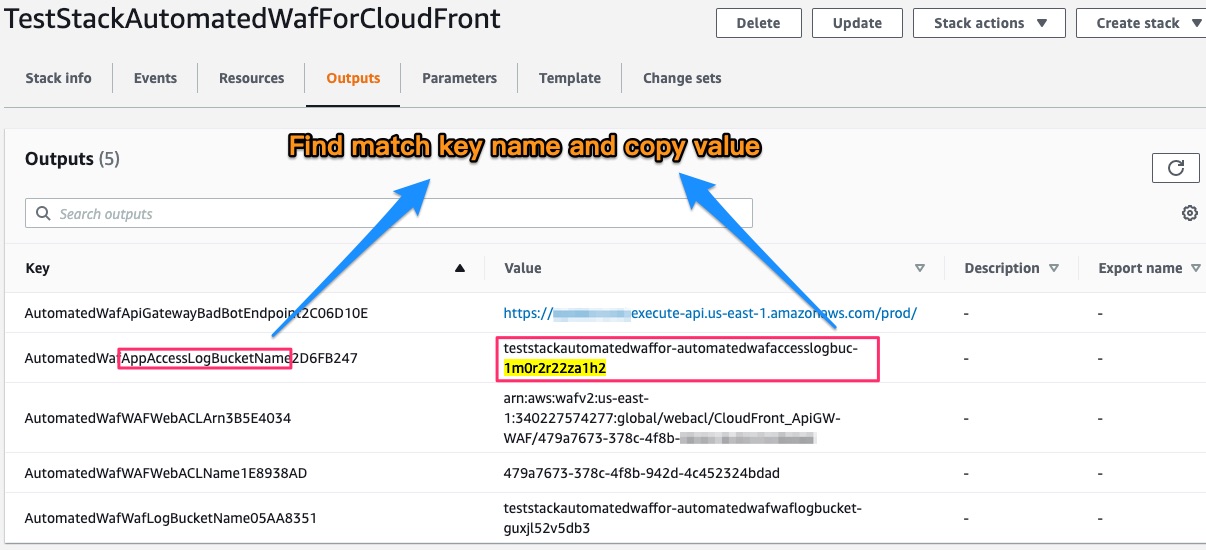
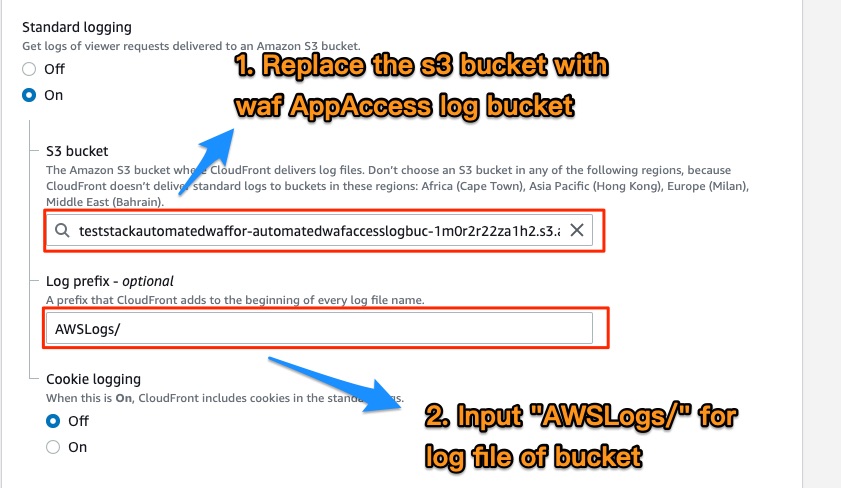
2. Set S3 bucket on CloudFront standand logging
Find S3 bucket name on CloudFormation output
Set CloudFront standard logging on CloudFront Settings
:warning: Log Prefix must be AWSLogs/
Application Load Balancers Usage
# Example automatically generated from non-compiling source. May contain errors.
env = {
"region": process.env.CDK_DEFAULT_REGION,
"account": process.env.CDK_DEFAULT_ACCOUNT
}
stack_test2 = cdk.Stack(app, "TestStackAutomatedWafForALB", env=env)
alb_arn = f"arn:aws:elasticloadbalancing:{cdk.Aws.REGION}:{cdk.Aws.ACCOUNT_ID}:loadbalancer/app/ApiNe-Alb16-2VIC9075YQEZ/db92cdc88d2e7c9d"
AutomatedWaf(stack_test2, "AutomatedWaf",
waf2_scope=Waf2ScopeOption.REGIONAL,
associated_resource_arn=alb_arn,
resource_naming_prefix="Alb_Api",
error_threshold=50,
request_threshold=300,
block_period=60,
log_level=LogLevel.DEBUG
)
After deploying, follow these steps on AWS Management Console. See below:
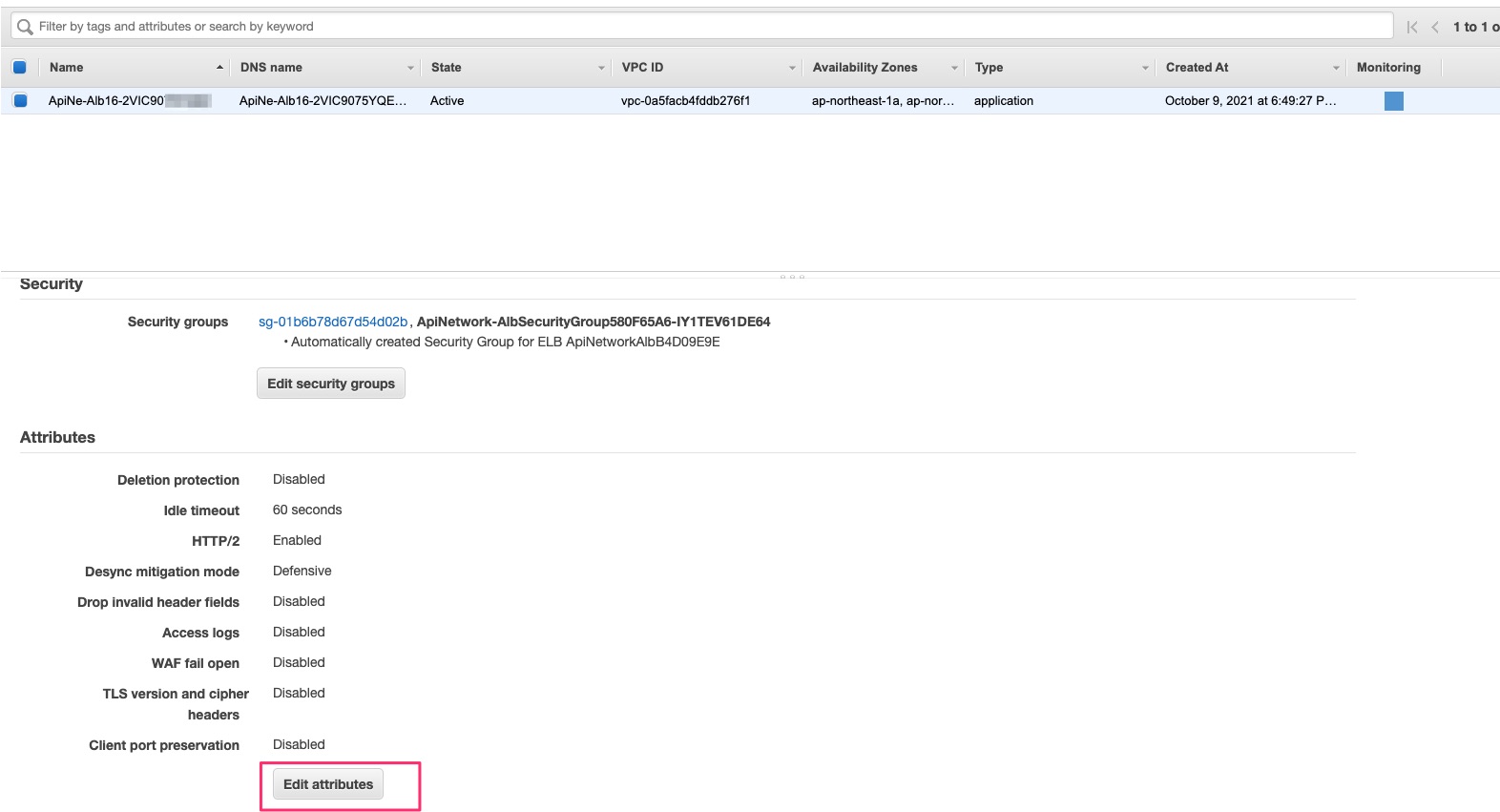
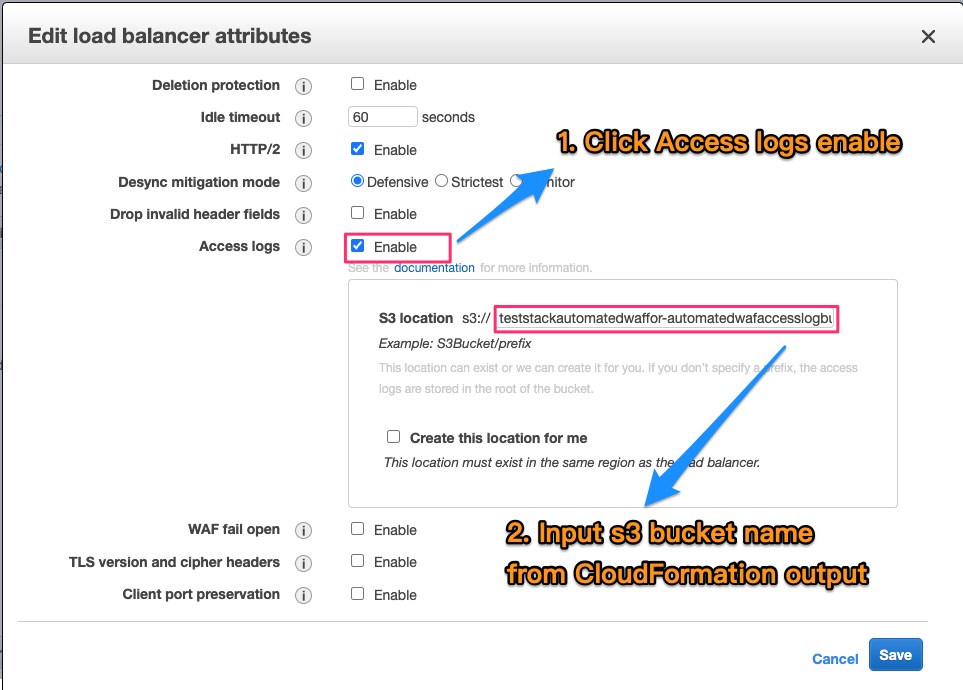
Find S3 bucket name on CloudFormation output
Click Edit Attributes on Basic Configuration of Load Balancers
Enable Access logs and input S3 bucket
API Gateway Usage
# Example automatically generated from non-compiling source. May contain errors.
env = {
"region": process.env.CDK_DEFAULT_REGION,
"account": process.env.CDK_DEFAULT_ACCOUNT
}
stack_test3 = cdk.Stack(app, "TestStackAutomatedWafForApiGW", env=env)
#
# Ref Stage arn in https://docs.aws.amazon.com/apigateway/latest/developerguide/arn-format-reference.html
#
rest_api_arn = f"arn:aws:apigateway:{cdk.Aws.REGION}::/restapis/0j90w09yf9/stages/prod"
AutomatedWaf(stack_test3, "AutomatedWaf",
waf2_scope=Waf2ScopeOption.REGIONAL,
associated_resource_arn=rest_api_arn,
resource_naming_prefix="ApiGW",
error_threshold=50,
request_threshold=300,
block_period=60,
log_level=LogLevel.DEBUG
)
Troubleshooting
If deployment error, the cloudFormation Error event like this
Received response status [FAILED] from custom resource. Message returned: 'HttpFloodLambdaLogParser' (RequestId: b4e08ea2-fe0a-46f8-98aa-6f96d4558579)
If any custom resource deploy error like above, delete the stack and redeploy it that will pass.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Hashes for ikala-cloud.aws-waf-solution-1.0.25.tar.gz
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | 26a5b537e229b58028eeb08cc8f37f1245df4a55c42653c25e0aa62cecf76b0b |
|
| MD5 | 9595161fb9c26f0ad4da3835f5a1065b |
|
| BLAKE2b-256 | 4588b9a82c3118aed02d596d13470a3505c2fbdc57641c427bcef6ffd300e8da |
Hashes for ikala_cloud.aws_waf_solution-1.0.25-py3-none-any.whl
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | 06c5cf53483c809277a3e45dec191b49a9063a518936fe53a62e6a09338bc818 |
|
| MD5 | a7c30e53bab501ced53cd2b4739f956d |
|
| BLAKE2b-256 | f1889c9091e155d4d0e56972511da75d33a389497fb7417faad0d5c22517baa2 |