Panthera(P.)uncia - Official CLI utility for Osprey Vision, Subdomain Center & Exploit Observer
Project description
Panthera(P.)uncia
Official CLI utility for Osprey Vision, Subdomain Center & Exploit Observer




Puncia utilizes three of our intelligent APIs to gather the results -
- Subdomain Center - The World's Largest Subdomain & Shadow IT Intelligence Database
- Exploit Observer - The World's Largest Exploit & Vulnerability Intelligence Database
- Osprey Vision - The World's Most Bleeding Edge AI for Information Discovery
Please note that although these results can sometimes be pretty inaccurate & unreliable, they can greatly differ from time to time due to their self-improvement capabilities.
Aggressive rate-limits can be avoided with an API key: https://www.arpsyndicate.io/pricing.html
Practical Applications
- Mapping External Attack Surfaces
Identify and monitor exposed subdomains and infrastructure components across the internet. - Advanced Vulnerability Research & Monitoring
Discover and track known and emerging threats, including obscure or unlisted vulnerabilities. - Contextual Enrichment of CVE/GHSA Data
Add depth and actionable intelligence to known vulnerabilities for better prioritization. - LLM-Driven Summarization & Prompt Execution
Leverage AI to summarize web content or generate code and analysis based on natural language prompts. - Automated Vulnerability Advisory Creation
Instantly generate detailed, multilingual security advisories for discovered vulnerabilities. - Vulnerability Detection in Software Bill of Materials (SBOM)
Analyze software components for known exploits and security issues using structured SBOM data. - Seamless Integration with CI/CD & Threat Intel Workflows
Automate intelligence gathering and vulnerability checks within development or security pipelines. - Monitoring Nation-State Exploit Trends
Stay ahead of threats by tracking vulnerabilities flagged by foreign actors but not yet recognized by mainstream databases. - Replica Domain Detection & Brand Protection
Identify replica or lookalike domains that could be used in phishing or impersonation attacks. - Bulk Threat Intelligence Processing
Run batch queries (domains, vulnerabilities, etc.) for scalable analysis across large datasets or enterprise asset inventories. - Passive Reconnaissance for Red Teams
Conduct stealthy reconnaissance by using passive data sources (no direct interaction with targets). - Open Source Intelligence (OSINT) Collection
Combine subdomain, exploit, and content summarization features to enhance OSINT investigations. - Security Blog & Research Digest Automation
Automatically summarize technical blog posts and reports into actionable briefs. - Cross-Language Security Intelligence Delivery
Translate advisories or technical content into other languages for global teams and multilingual incident response. - Compliance & Risk Management Support
Enrich vulnerability data to support compliance audits (e.g., ISO 27001, SOC 2) with deeper context.
Installation
- From PyPi -
pip3 install puncia - From Source -
pip3 install .
Usage
-
(PAID) Store an API key (storekey) -
puncia storekey <api-key> -
(FREEMIUM) Interact with the LLM (chat) -
puncia chat "<prompt>" <output-file> -
(PAID) Summarize Webpages with the LLM (summarize) -
puncia summarize "<links>" <output-file> -
(FREEMIUM) Query Domains (subdomain) -
puncia subdomain <domain> <output-file> -
(FREEMIUM) Query Replica Domains (replica) -
puncia replica <domain> <output-file> -
Query Exploit & Vulnerability Identifiers (exploit)
- (FREE) Vulnerability & Exploit Identifers Watchlist (^WATCHLIST_IDES) -
puncia exploit ^WATCHLIST_IDES <output-file> - (FREE) Vulnerability & Exploit Identifers Watchlist with Descriptions (^WATCHLIST_INFO) -
puncia exploit ^WATCHLIST_INFO <output-file> - (FREE) Vulnerable Technologies Watchlist (^WATCHLIST_TECH) -
puncia exploit ^WATCHLIST_TECH <output-file> - (FREEMIUM) Supported Vulnerability Identifiers -
puncia exploit <eoidentifier> <output-file>
- (FREE) Vulnerability & Exploit Identifers Watchlist (^WATCHLIST_IDES) -
-
(PAID) Generate Vulnerability Advisory with the LLM (advisory) -
puncia advisory "<eoidentifier>|<language>" <output-file> -
(FREEMIUM) Enrich CVE/GHSA Identifiers (enrich) -
puncia enrich <cve-id/ghsa-id> <output-file> -
Multiple Queries (bulk/sbom)
- (FREEMIUM) Bulk Input JSON File Format -
puncia bulk <json-file> <output-directory>{ "subdomain": [ "domainA.com", "domainB.com" ], "replica": [ "domainA.com", "domainB.com" ], "exploit": [ "eoidentifierA", "eoidentifierB" ], "enrich": [ "eoidentifierA", "eoidentifierB" ], "advisory": [ "eoidentifierA", "eoidentifierB|GERMAN" ] }
- (FREEMIUM) SBOM Input JSON File Format -
puncia sbom <json-file> <output-directory>
- (FREEMIUM) Bulk Input JSON File Format -
-
(FREEMIUM) External Import
import puncia
import asyncio
async def main():
# Without API Key
print(await puncia.query_api("exploit", "CVE-2021-3450"))
print(await puncia.query_api("subdomain", "arpsyndicate.io"))
print(await puncia.query_api("chat", "write a xss fuzzer in python"))
# With API Key
await puncia.store_key("ARPS-xxxxxxxxxx")
api_key = await puncia.read_key()
print(await puncia.query_api("subdomain", "arpsyndicate.io", apikey=api_key))
print(await puncia.query_api("exploit", "CVE-2021-3450", apikey=api_key))
print(await puncia.query_api("chat", "write a xss fuzzer in python", apikey=api_key))
print(await puncia.query_api("summarize", "https://www.osintteam.com/combating-the-darkest-depths-of-cyber-intelligence-the-pall-mall-process/", apikey=api_key))
print(await puncia.query_api("advisory", "CVE-2025-31324", apikey=api_key))
print(await puncia.query_api("advisory", "CVE-2025-31324|FRENCH", apikey=api_key))
# Run the main async function
asyncio.run(main())
CVE Enrichment
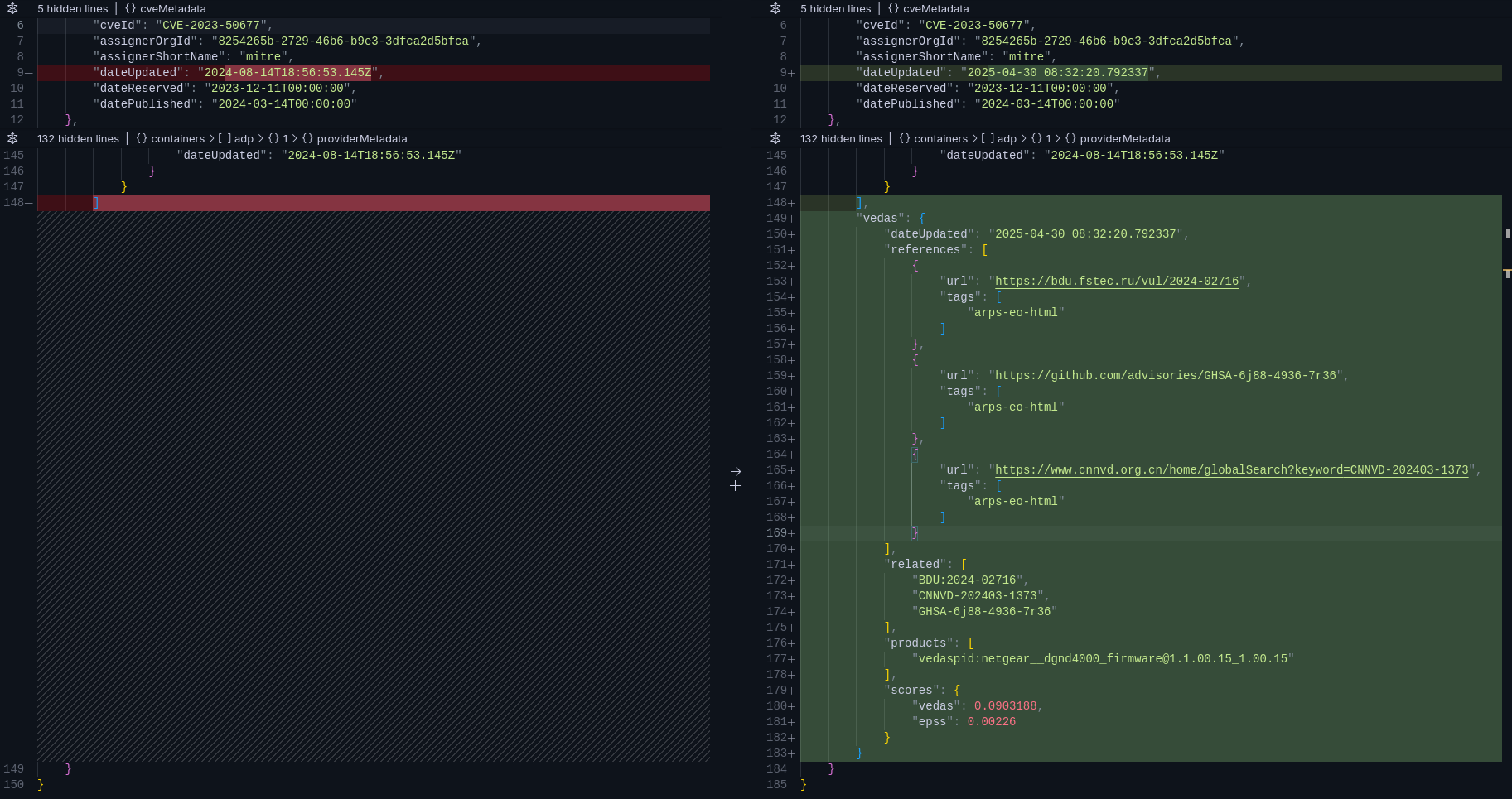
GHSA Enrichment
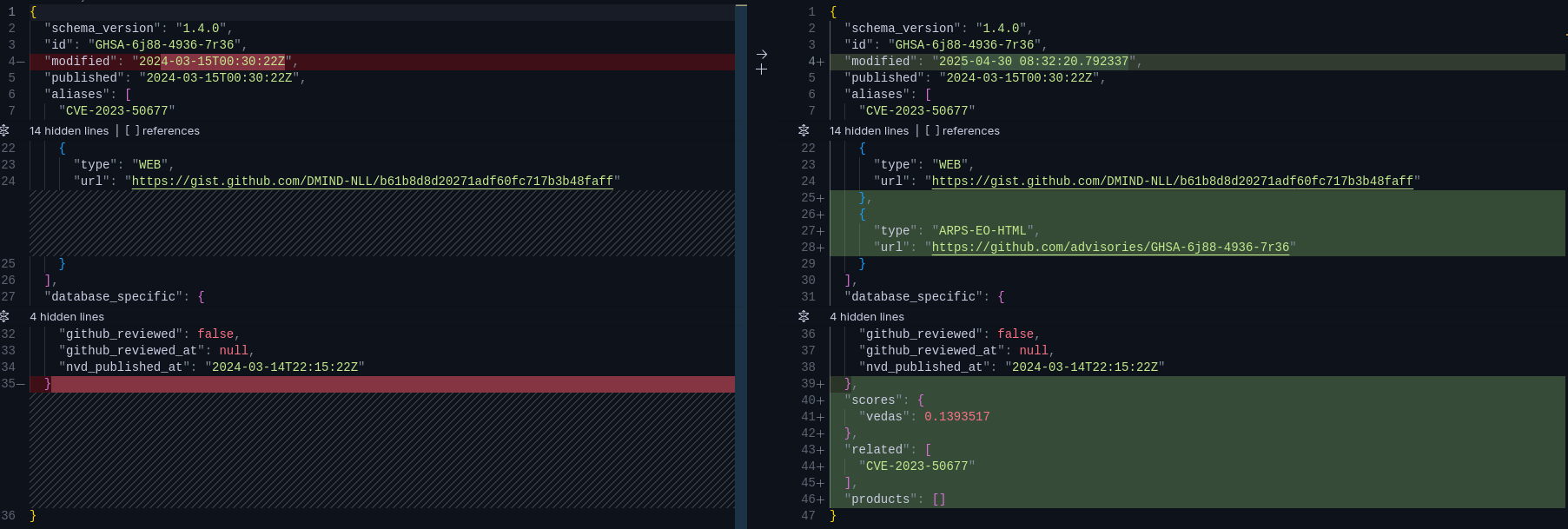
Noteworthy Mentions
- Passive Subdomain Enumeration: Uncovering More Subdomains than Subfinder & Amass
- Around 1000 exploitable cybersecurity vulnerabilities that MITRE & NIST ‘might’ have missed but China or Russia didn’t.
- Utilizing GitHub Actions for gathering Subdomain & Exploit Intelligence
- Introducing Exploit Observer — More than Shodan Exploits, Less than Vulners
- PUNCIA — The Panthera(P.)uncia of Cybersecurity
- Subdomain Enumeration Tool Face-off - 2023 Edition
More from A.R.P. Syndicate
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file puncia-0.34.tar.gz.
File metadata
- Download URL: puncia-0.34.tar.gz
- Upload date:
- Size: 8.2 kB
- Tags: Source
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/5.1.1 CPython/3.10.12
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
5b9a1bade9603da3e6a3f459c4081a63c2d08e454d1ba3a155b1e4a0d667b0a1
|
|
| MD5 |
83cda946ee0428fd3283d8a6ba2a1dcb
|
|
| BLAKE2b-256 |
e12d25761c5230b10a4ff74cbf2ed853c3afc647e7a5bc2ea043614a9bfcba4a
|
File details
Details for the file puncia-0.34-py3-none-any.whl.
File metadata
- Download URL: puncia-0.34-py3-none-any.whl
- Upload date:
- Size: 9.1 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/5.1.1 CPython/3.10.12
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
69fce073e3a88fd2db2ede4fa1405228e77736265672325a6b7992e510da1e51
|
|
| MD5 |
0b15c8946c3843c4bbbe6bca17186042
|
|
| BLAKE2b-256 |
f1b805a5a752abf4c2343ddbd6cbd105ac803d6c441fea5d3580582618e267dd
|











