Find authentication (authn) and authorization (authz) security bugs in web application routes.
Project description
route-detect
Find authentication (authn) and authorization (authz) security bugs in web application routes:
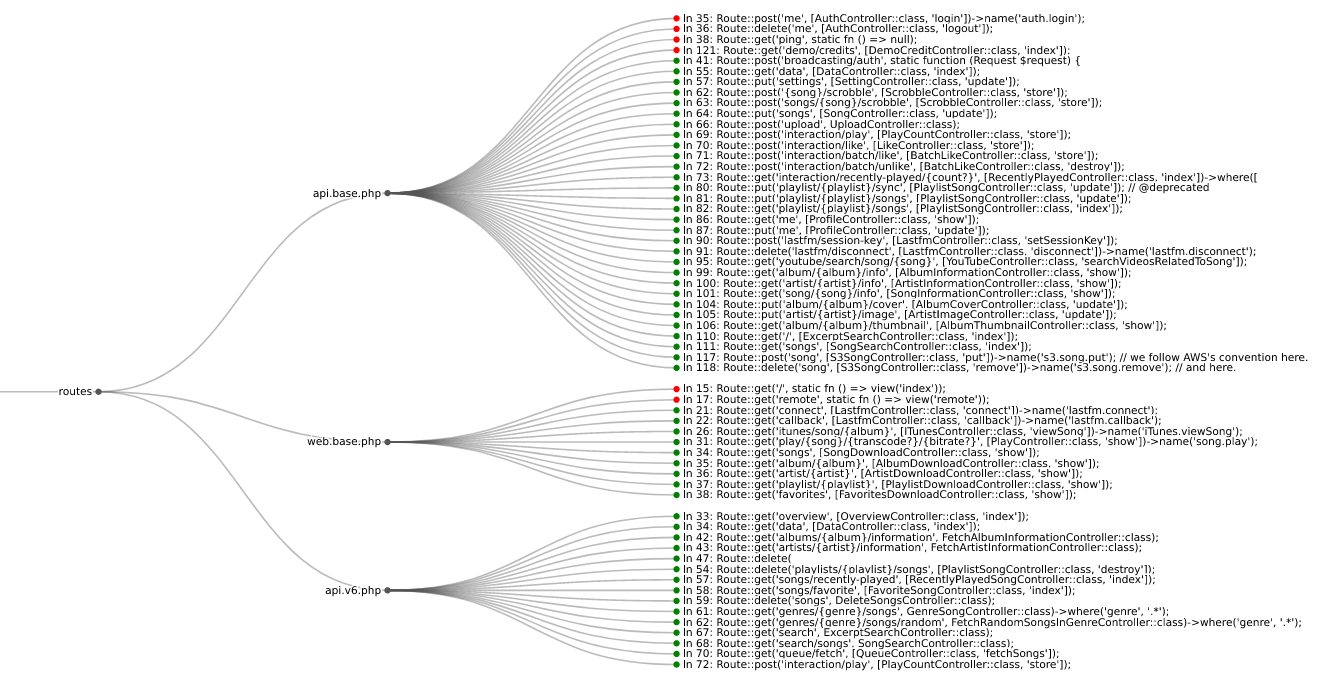
Routes from koel streaming server
Web application HTTP route authn and authz bugs are some of the most common security issues found today. These industry standard resources highlight the severity of the issue:
- 2021 OWASP Top 10 #1 - Broken Access Control
- 2021 OWASP Top 10 #7 - Identification and Authentication Failures (formerly Broken Authentication)
- 2023 OWASP API Top 10 #1 - Broken Object Level Authorization
- 2023 OWASP API Top 10 #2 - Broken Authentication
- 2023 OWASP API Top 10 #5 - Broken Function Level Authorization
- 2023 CWE Top 25 #11 - CWE-862: Missing Authorization
- 2023 CWE Top 25 #13 - CWE-287: Improper Authentication
- 2023 CWE Top 25 #20 - CWE-306: Missing Authentication for Critical Function
- 2023 CWE Top 25 #24 - CWE-863: Incorrect Authorization
Supported web frameworks (route-detect IDs in parentheses):
- Python: Django (
django,django-rest-framework), Flask (flask), Sanic (sanic), FastAPI (fastapi) - PHP: Laravel (
laravel), Symfony (symfony), CakePHP (cakephp) - Ruby: Rails* (
rails), Grape (grape) - Java: JAX-RS (
jax-rs), Spring (spring) - Go: Gorilla (
gorilla), Gin (gin), Chi (chi) - JavaScript/TypeScript: Express (
express), React (react), Angular (angular)
*Rails support is limited. Please see this issue for more information.
Installing
Use pip to install route-detect:
$ python -m pip install --upgrade route-detect
You can check that route-detect is installed correctly with the following command:
$ echo 'print(1 == 1)' | semgrep --config $(routes which test-route-detect) -
Scanning 1 file.
Findings:
/tmp/stdin
routes.rules.test-route-detect
Found '1 == 1', your route-detect installation is working correctly
1┆ print(1 == 1)
Ran 1 rule on 1 file: 1 finding.
Using
route-detect provides the routes CLI command and uses semgrep to search for routes.
Use the which subcommand to point semgrep at the correct web application rules:
$ semgrep --config $(routes which django) path/to/django/code
Use the viz subcommand to visualize route information in your browser:
$ semgrep --json --config $(routes which django) --output routes.json path/to/django/code
$ routes viz --browser routes.json
If you're not sure which framework to look for, you can use the special all ID to check everything:
$ semgrep --json --config $(routes which all) --output routes.json path/to/code
If you have custom authn or authz logic, you can copy route-detect's rules:
$ cp $(routes which django) my-django.yml
Then you can modify the rule as necessary and run it like above:
$ semgrep --json --config my-django.yml --output routes.json path/to/django/code
$ routes viz --browser routes.json
Contributing
route-detect uses poetry for dependency and configuration management.
Before proceeding, install project dependencies with the following command:
$ poetry install --with dev
Linting
Lint all project files with the following command:
$ poetry run pre-commit run --all-files
Testing
Run Python tests with the following command:
$ poetry run pytest --cov
Run Semgrep rule tests with the following command:
$ poetry run semgrep --test --config routes/rules/ tests/test_rules/
Project details
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file route_detect-0.8.0.tar.gz.
File metadata
- Download URL: route_detect-0.8.0.tar.gz
- Upload date:
- Size: 22.7 kB
- Tags: Source
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/5.1.0 CPython/3.11.2
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
22ecd0c82358f6fecda0c5b38bb6fef53c924bb139682f892fb209e5e727f49e
|
|
| MD5 |
0fecf33b7707c796e2fbb947d5268034
|
|
| BLAKE2b-256 |
a349028a4437a39992bd09b0b096f164227e1b446f2900fc53ef9ed1d27c8b87
|
File details
Details for the file route_detect-0.8.0-py3-none-any.whl.
File metadata
- Download URL: route_detect-0.8.0-py3-none-any.whl
- Upload date:
- Size: 29.9 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/5.1.0 CPython/3.11.2
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
848ad1b9783c475b7e7875c07e43402a7d40079745c7abc02b36a2cd4d724b79
|
|
| MD5 |
dd0f142f717b13e58a6f4054676273b5
|
|
| BLAKE2b-256 |
9f0d45e4f08be2b58d2078c299d15a171a8a232a172f5c97b28a3d3187edeeb2
|