PCI-compliant authentication application for Django 1.4+. Uses "best of" existing libraries then fills in the gaps.
Project description
django-pci-auth
Django 1.4+ with SSL only
This library integrates the current Django “best of” PCI auth libraries into a single application then fills in the gaps. Filling in the gaps involves making decisions for you e.g.:
https://docs.djangoproject.com/en/1.4/topics/auth/#using-bcrypt-with-django
https://docs.djangoproject.com/en/1.4/topics/auth/#increasing-the-work-factor
https://docs.djangoproject.com/en/1.4/topics/http/sessions/#session-cookie-age
And adding additional functionality e.g.:
Database models to persist event data e.g. lockouts (See: docs/MODELS.rst).
Additional recently_used validator for django-passwords.
Features
Stronger password hashing that allows for selection of hashing algorithm scrypt, bcrypt, PBKDF2, etc. via settings.py. [1]
Checking for strong passwords with a default length setting overrideable in settings.py. [2]
Integrate strong passwords into Django Admin.
Lock out account for n minutes after x failed log-in attempts. [3]
Set inactivity timeouts.
Generate event/email when lock-out occurs.
Set flags disallowing certain accounts to be locked out.
Log every log-on and explicit log-out (not necessary to log timed out log-ins).
Track last four passwords and do not allow re-use. [4]
Force password reset after X amount of time.
Provide JavaScript to check for strong passwords inline. [5]
Installation
Before you use this library in your applications you may wish to demo its functionality. To do so, follow these steps:
$ virtualenv . $ bin/pip install django-pci-auth $ bin/django-admin.py syncdb --settings=django_pci_auth.settings $ bin/django-admin.py runserver --settings=django_pci_auth.settings
Libraries
A list of libraries included:
Articles
A list of relevant articles:
http://kencochrane.net/blog/2012/01/developers-guide-to-pci-compliant-web-applications/
http://stackoverflow.com/questions/2693837/django-staff-decorator
http://stackoverflow.com/questions/3566174/django-increase-inactivity-timeout
http://stackoverflow.com/questions/5179635/django-account-lockout
http://stackoverflow.com/questions/13055722/enforcing-password-strength-requirements-in-django
http://www.egrappler.com/jquery-strong-password-plugin-power-pwchecker/
http://www.elementps.com/merchants/pci-dss/compliance-level/
Settings
Stronger password hashing
This is a built-in feature in Django 1.4+. Documented here for convenience:
PASSWORD_HASHERS = (
# From https://docs.djangoproject.com/en/1.4/topics/auth/:
# "[redacted] This means that Django will use the first hash in the list
# to store all passwords, but will support checking passwords stored with
# the rest of the hashes in the list. If you remove a hash from the list
# it will no longer be supported.
'django.contrib.auth.hashers.PBKDF2PasswordHasher',
'django.contrib.auth.hashers.PBKDF2SHA1PasswordHasher',
'django.contrib.auth.hashers.BCryptPasswordHasher',
'django.contrib.auth.hashers.SHA1PasswordHasher',
'django.contrib.auth.hashers.MD5PasswordHasher',
'django.contrib.auth.hashers.CryptPasswordHasher',
)
Password Reuse
How many old passwords will you store? This feature will prevent users from using the same passwords over and over again; it will keep the last OLD_PASSWORD_STORAGE_NUM number of passwords around and remove anything older. E.g.:
OLD_PASSWORD_STORAGE_NUM = 4
Screenshots
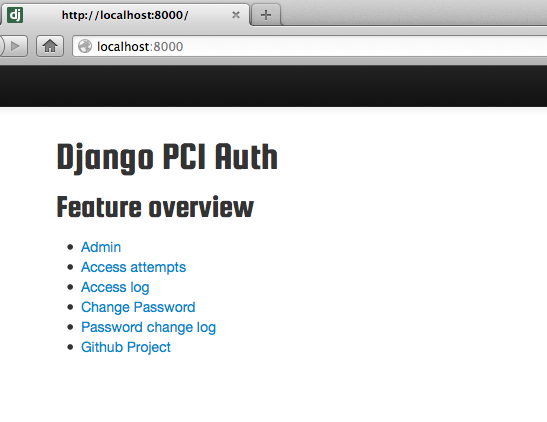
Feature overview (via index view)
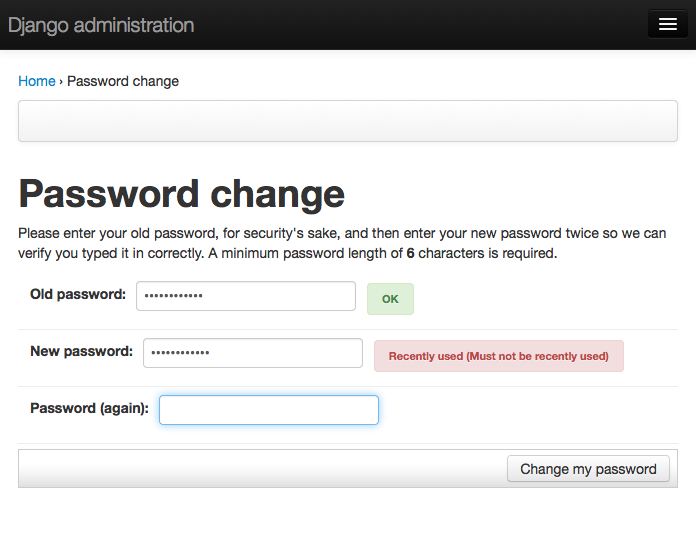
Password length enforcement (with AJAX validation)
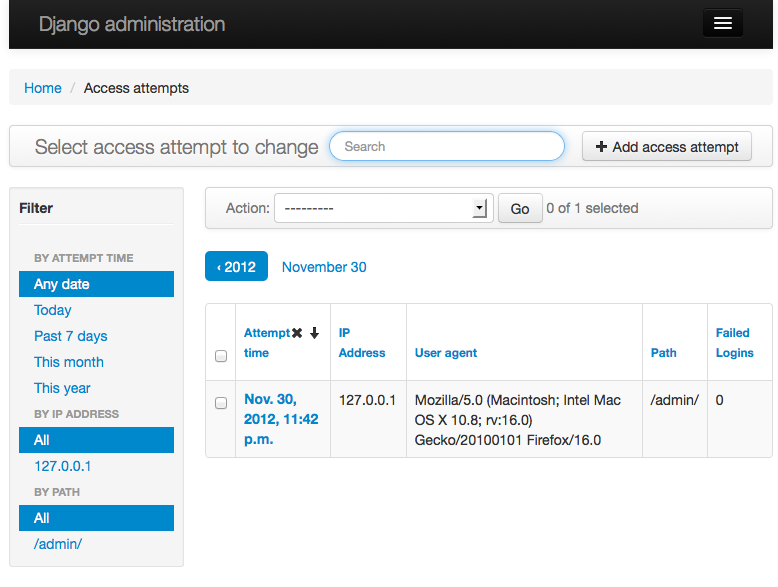
Failed login attempts log
Recently used password log

License
This software is licensed under the same BSD license that Django itself is licensed under. See: LICENSE.
Notes
Changes
0.0.6 (2012-12-05)
Add a note re: SSL [aclark]
0.0.5 (2012-12-04)
Feature complete [aclark]
0.0.4 (2012-11-28)
Pre-release, includes most features promised. [aclark]
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.











