Allow users to login through OpenID Connect Provider
Project description
This module allows users to login through an OpenID Connect provider using the authorization code flow or implicit flow.
Note the implicit flow is not recommended because it exposes access tokens to the browser and in http logs.
Table of contents
Installation
This module depends on the python-jose library, not to be confused with jose which is also available on PyPI.
Configuration
Setup for Microsoft Azure
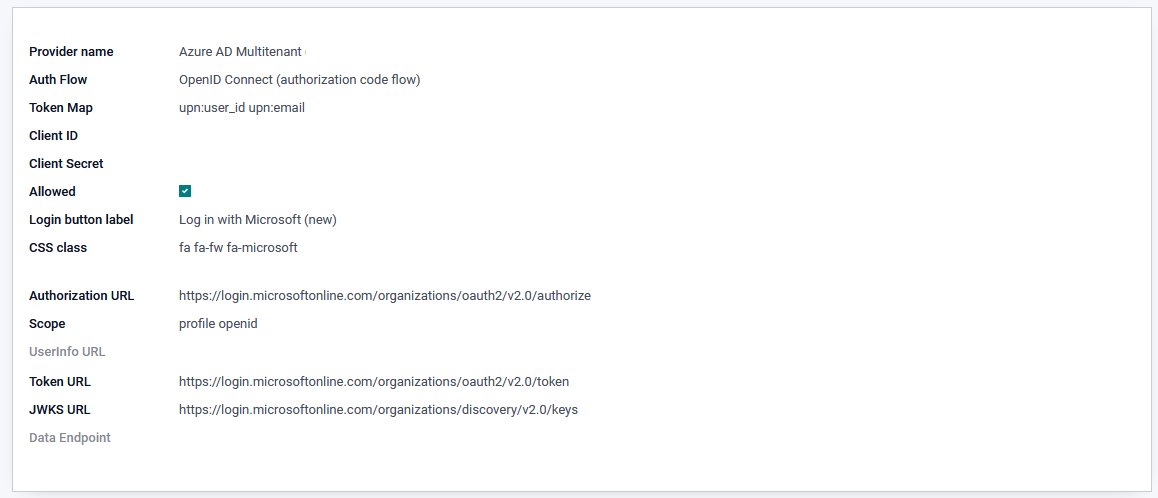
Example configuration with OpenID Connect authorization code flow.
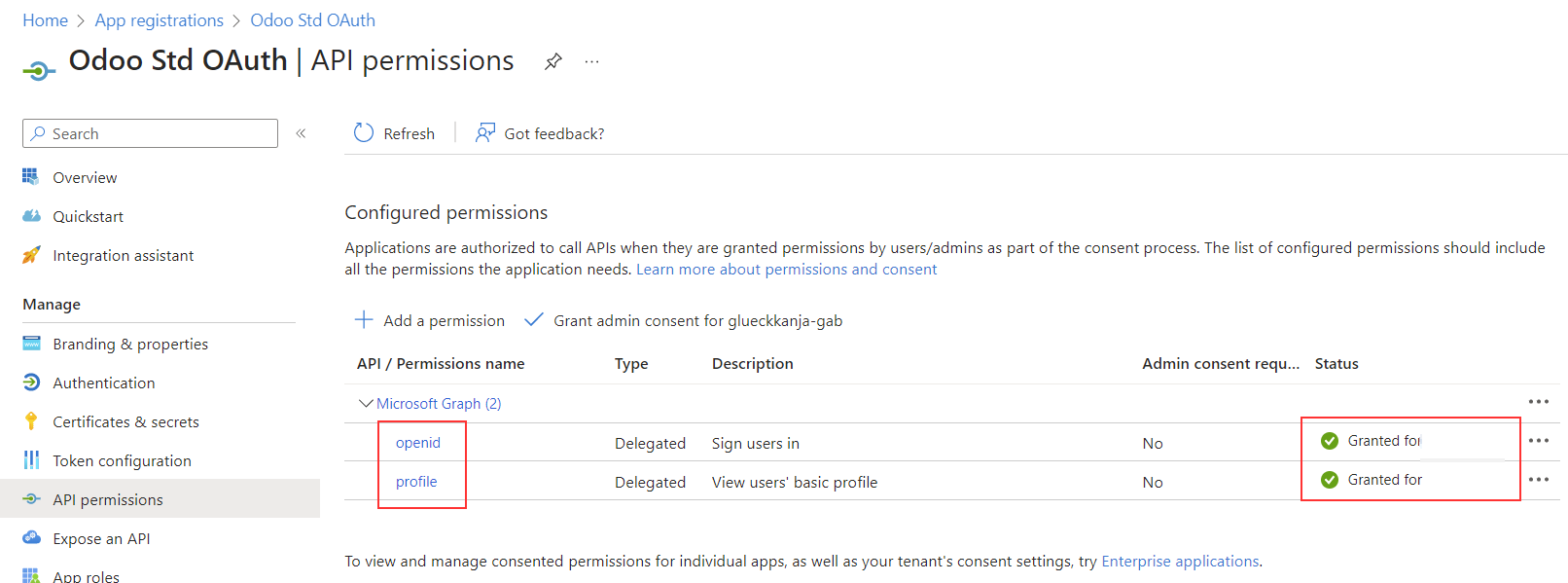
configure a new web application in Azure with OpenID and code flow (see the provider documentation))
in this application the redirect url must be be “<url of your server>/auth_oauth/signin” and of course this URL should be reachable from Azure
create a new authentication provider in Odoo with the following parameters (see the portal documentation for more information):
Single tenant provider limits the access to user of your tenant, while Multitenants allow access for all AzureAD users, so user of foreign companies can use their AzureAD login without an guest account.
Provider Name: Azure AD Single Tenant
Client ID: Application (client) id
Client Secret: Client secret
Allowed: yes
or
Provider Name: Azure AD Multitenant
Client ID: Application (client) id
Client Secret: Client secret
Allowed: yes
replace {tenant_id} in urls with your Azure tenant id
Auth Link Params: Add {‘prompt’:’select_account’} to the auth link to get the account selection screen
Setup for Keycloak
Example configuration with OpenID Connect authorization code flow.
In Keycloak:
configure a new Client
make sure Authorization Code Flow is Enabled.
configure the client Access Type as “confidential” and take note of the client secret in the Credentials tab
configure the redirect url to be “<url of your server>/auth_oauth/signin”
In Odoo, create a new Oauth Provider with the following parameters:
Provider name: Keycloak (or any name you like that identify your keycloak provider)
Auth Flow: OpenID Connect (authorization code flow)
Client ID: the same Client ID you entered when configuring the client in Keycloak
Client Secret: found in keycloak on the client Credentials tab
Allowed: yes
Body: the link text to appear on the login page, such as Login with Keycloak
Scope: openid email
Authentication URL: The “authorization_endpoint” URL found in the OpenID Endpoint Configuration of your Keycloak realm
Token URL: The “token_endpoint” URL found in the OpenID Endpoint Configuration of your Keycloak realm
JWKS URL: The “jwks_uri” URL found in the OpenID Endpoint Configuration of your Keycloak realm
Usage
On the login page, click on the authentication provider you configured.
Known issues / Roadmap
When going to the login screen, check for a existing token and do a direct login without the clicking on the SSO link
When doing a logout an extra option to also logout at the SSO provider.
Changelog
17.0.1.0.0 2024-03-20
Odoo 17 migration
16.0.1.1.0 2024-02-28
Forward port OpenID Connect fixes from 15.0 to 16.0
16.0.1.0.2 2023-11-16
Readme link updates
16.0.1.0.1 2023-10-09
Add AzureAD code flow provider
16.0.1.0.0 2023-01-27
Odoo 16 migration
15.0.1.0.0 2023-01-06
Odoo 15 migration
14.0.1.0.0 2021-12-10
Odoo 14 migration
13.0.1.0.0 2020-04-10
Odoo 13 migration, add authorization code flow.
10.0.1.0.0 2018-10-05
Initial implementation
Bug Tracker
Bugs are tracked on GitHub Issues. In case of trouble, please check there if your issue has already been reported. If you spotted it first, help us to smash it by providing a detailed and welcomed feedback.
Do not contact contributors directly about support or help with technical issues.
Credits
Contributors
Alexandre Fayolle <alexandre.fayolle@camptocamp.com>
Stéphane Bidoul <stephane.bidoul@acsone.eu>
David Jaen <david.jaen.revert@gmail.com>
Andreas Perhab <andreas.perhab@wt-io-it.at>
Maintainers
This module is maintained by the OCA.

OCA, or the Odoo Community Association, is a nonprofit organization whose mission is to support the collaborative development of Odoo features and promote its widespread use.
Current maintainer:
This module is part of the OCA/server-auth project on GitHub.
You are welcome to contribute. To learn how please visit https://odoo-community.org/page/Contribute.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distributions
Built Distribution
File details
Details for the file odoo_addon_auth_oidc-17.0.1.1.0.2-py3-none-any.whl.
File metadata
- Download URL: odoo_addon_auth_oidc-17.0.1.1.0.2-py3-none-any.whl
- Upload date:
- Size: 199.0 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/5.1.1 CPython/3.12.3
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | a8e6a2ec5232c3f9d11692c2ae70ece3ad8d6a109a4532848893fbc97ec95a62 |
|
| MD5 | a9a167ceca0053efd806b9492dec2f72 |
|
| BLAKE2b-256 | 913721d0c2ebbb7d36888fd020073fee49824b82ecd210d6b3cc258fa00cb283 |