Tool to create and update Munki manifests for devices managed in Intune
Project description
Munki Manifest Generator
This is a tool to generate Munki manifests for devices managed by Intune. Instead of manually managing manifests for each device, this tool uses the groups the user and/or device is a member of to determine which included manifests and catalogs the device should be a memmber of.
To do this, you create a JSON file and pass that when executing like this munki-manifest-generator -j path_to_json. The JSON needs to be spcified like below,
[
{
"id": "id_of_aad_group", // id of the group in Azure AD
"name": "name_of_manifest", // name of manifest in Munki
"catalog": "catalog_name", // name of catalog in Munki or null
"type": "type_of_group" // valid values are "user" or "device"
}
]
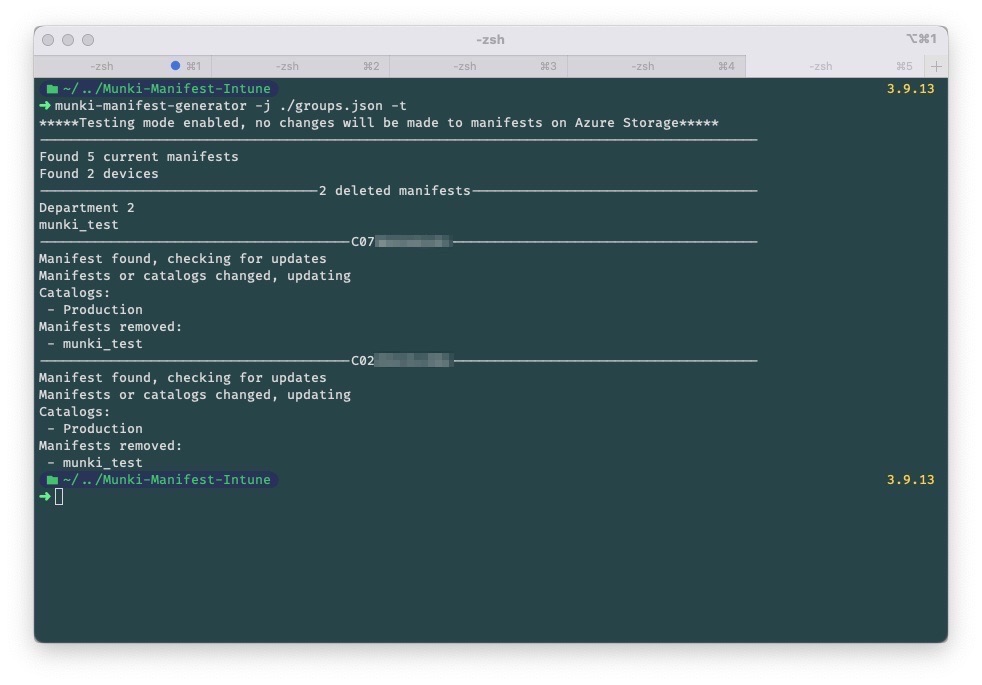
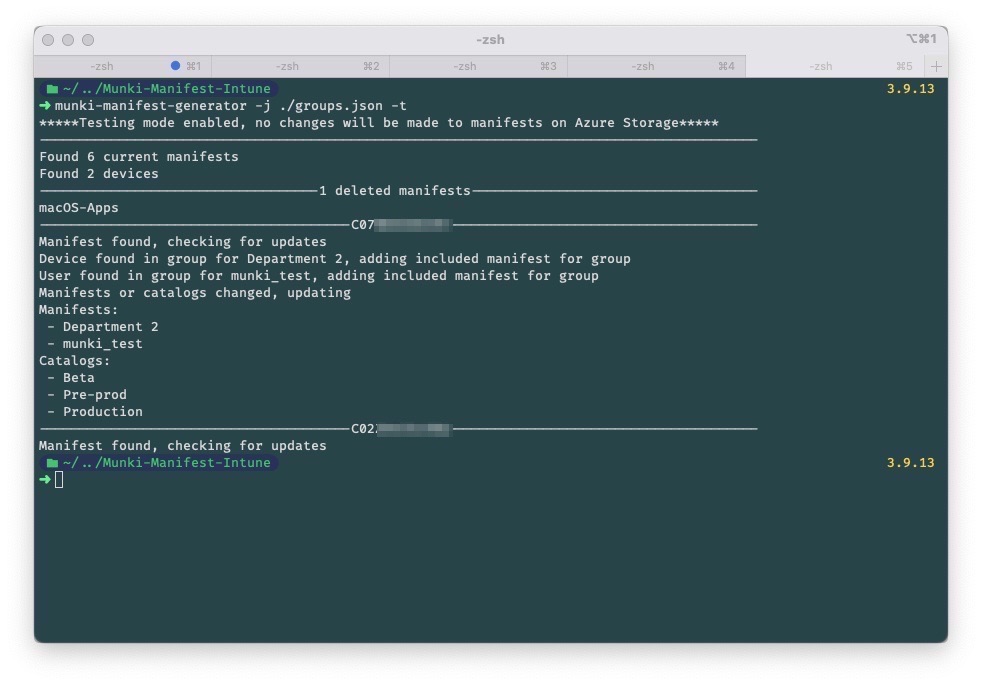
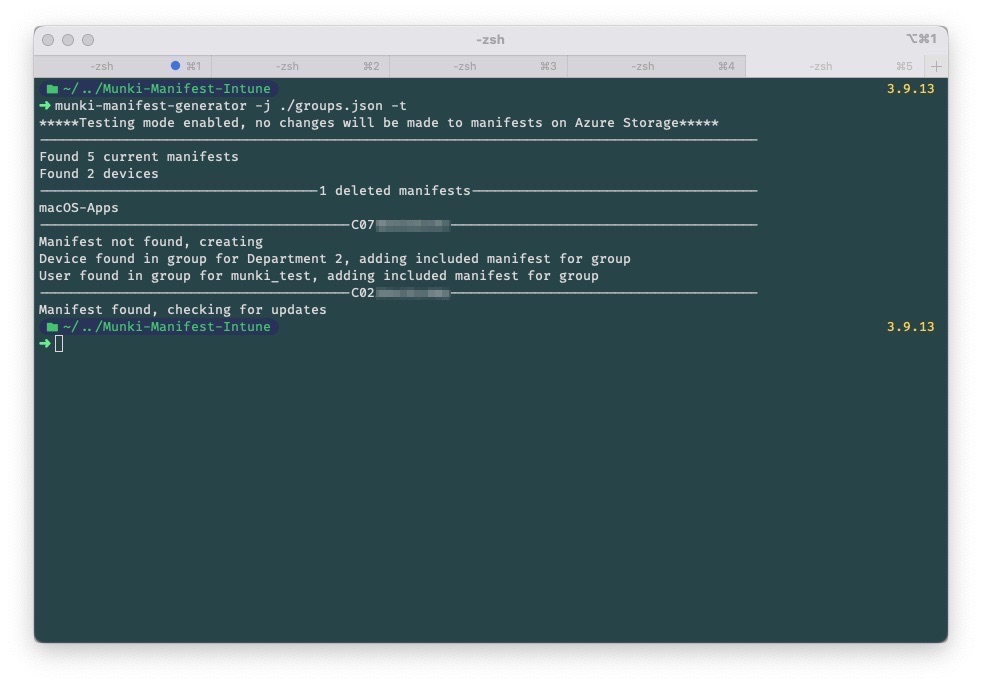
Let's say you have manifests and catalogs for testing, Beta and Pre-Production, you can specify the Azure AD groups the user or device needs to be part of in order to be included. If you then set this up to run on a schedule, the device's membership will update in Munki if the user or device is made a member or removed from a group.
[
{
"id": "111-111-111-111",
"name": "internal-testing",
"catalog": "testing",
"type": "device"
},
{
"id": "222-222-222-222",
"name": "Beta-users",
"catalog": "Beta",
"type": "user"
},
{
"id": "333-333-333-333",
"name": "pre-production",
"catalog": "preprod",
"type": "device"
}
]
If running this tool from an agent where it can be hazzle to pass a file, you can instead parse a list of dicts in script. The below example is running in an Azure Runbook where variables have been configured on the automation account, sensitive information like client secret and connection strings have been saved as encrypted variables. It's also prepared to be executed from a webhook targeting a specific device,
#!/usr/bin/env python3
import os
import sys
import json
import automationassets
from automationassets import AutomationAssetNotFound
from munki_manifest_generator import main as mmg
webhook = False
# If executed from webhook, load json data and set webhook to True
if len(sys.argv) > 1 :
data = sys.argv[1].split(",")
w_data = data[1].replace("RequestBody:","")
webhook_data = json.loads(w_data)
webhook = True
serial = webhook_data['serial']
# get variables
os.environ['CLIENT_ID'] = automationassets.get_automation_variable("CLIENT_ID")
os.environ['CLIENT_SECRET'] = automationassets.get_automation_variable("CLIENT_SECRET")
os.environ['CONTAINER_NAME'] = automationassets.get_automation_variable("CONTAINER_NAME")
os.environ['AZURE_STORAGE_CONNECTION_STRING'] = automationassets.get_automation_variable("AZURE_STORAGE_CONNECTION_STRING")
os.environ['TENANT_NAME'] = automationassets.get_automation_variable("TENANT_NAME")
groups = [
{
"id": "id_of_aad_group_1",
"name": "name_of_manifest_1",
"catalog": "catalog_name_1",
"type": "type_of_group_1"
},
{
"id": "id_of_aad_group_2",
"name": "name_of_manifest_2",
"catalog": "catalog_name_2",
"type": "type_of_group_2"
}
]
if webhook is True:
mmg.main(group_list=groups, serial_number=serial)
else:
mmg.main(group_list=groups)
Testing mode
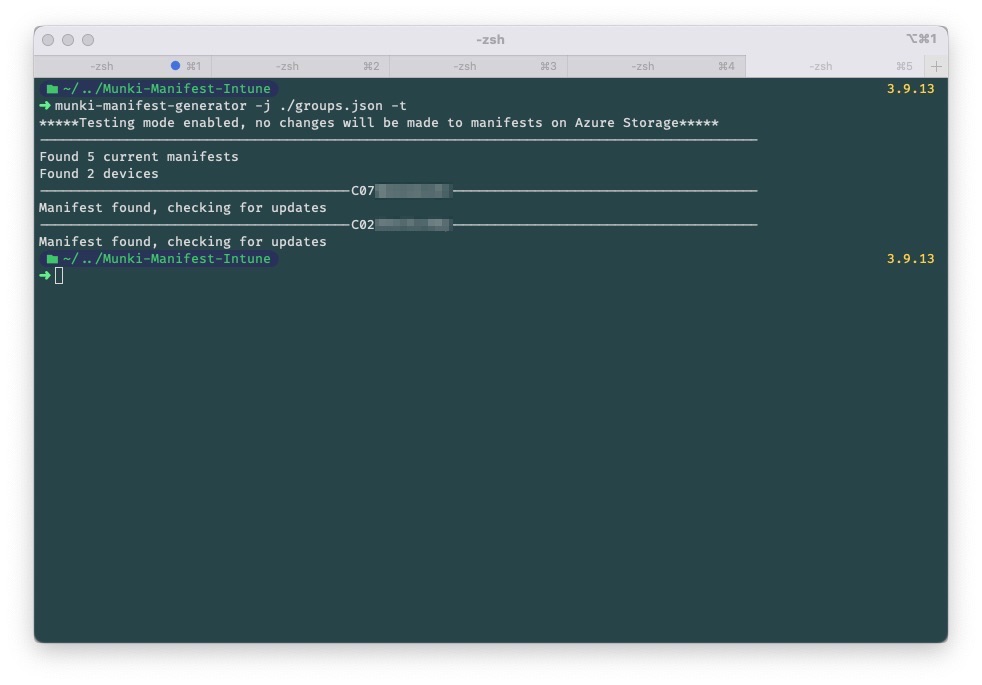
To run this tool without making any changes to the manifests on Azure Storage, which can be useful to test the groups in a json file or validate nothing unwanted will happen in your environment. The only thing you'll have to do is add the -t parameter.
Running from command line:
munki-manifest-generator -j path_to_json -t
Running from a script:
mmg.main(group_list=groups, test=True)
Environment variables
To use the tool, you must set a couple of environment variables that will be used to authenticate to Azure Storage and Microsoft Graph,
- CLIENT_ID - Azure AD App Registration client id
- CLIENT_SECRET - Azure AD App Registration client secret
- TENANT_NAME - Name of your Azure tenant, i.e. example@onmicrosoft.com
- CONTAINER_NAME - Name of your Azure Storage Container
- AZURE_STORAGE_CONNECTION_STRING - Connection string to your Azure Storage account
Azure AD app registration permissions
- DeviceManagementManagedDevices.Read.All
- Directory.Read.All
- GroupMember.Read.All
- Group.Read.All
Generated manifest exmaple
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>catalogs</key>
<array>
<string>testing</string>
<string>Production</string>
</array>
<key>display_name</key>
<string>tobias’s Mac</string>
<key>included_manifests</key>
<array>
<string>site_default</string>
<string>internal-testing</string>
</array>
<key>managed_installs</key>
<array/>
<key>optional_installs</key>
<array/>
<key>serialnumber</key>
<string>C07XXXXXXXXX</string>
<key>user</key>
<string>user@example.onmicrosoft.com</string>
</dict>
</plist>
Example output
Project details
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Hashes for Munki-Manifest-Generator-0.0.1.tar.gz
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | ca7a16ddf0abc73f736a3862d1af2fe057bdcdb5b1d6863eee6393bf97203d23 |
|
| MD5 | 92b82b6146bcc39d81fe5b54040882a0 |
|
| BLAKE2b-256 | 2a0e44caee62a0fa176f7143dc93ec96ba0b6b8b1b9b6f5cafc0666af37e0ef2 |
Hashes for Munki_Manifest_Generator-0.0.1-py3-none-any.whl
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | 55fec98d111286b5477f31e8667018c2b4119c3840c484460bd179b697280400 |
|
| MD5 | a3486583a37051df2c4ec4aae1e7beaa |
|
| BLAKE2b-256 | 3b414f54510d1eec04ecd0cc9c9d01529f1b5fb0e231fe9abf26543db1bf2cd1 |