flask-cookie-decode 0.4.3
pip install flask-cookie-decode
Released:
Tools for debugging and working with the built-in Flask session cookie
Navigation
Verified details
These details have been verified by PyPIProject links
GitHub Statistics
Maintainers
 wgwz
wgwz
Unverified details
These details have not been verified by PyPIMeta
- License: MIT License (MIT license)
- Author: Kyle Lawlor
- Tags flask_cookie_decode
-
Provides-Extra:
test
Classifiers
- Development Status
- Intended Audience
- License
- Natural Language
- Programming Language
Project description
1 flask-cookie-decode

|

|
1.1 Purpose
Adds a cookie command to the built-in Flask CLI which will provide various tools for debugging the secure session cookie that Flask uses by default.
1.1.1 Current available commands
flask cookie decode: decodes and verifies the signature of the session cookie
1.2 Background
By default the Flask session uses a signed cookie to store its data. The Flask application signs the cookie using its SECRET_KEY. This provides the Flask application a way to detect any tampering to the session data. If the application is indeed using a secret key and secure hashing algorithm, the session signature will be unique to application.
For more on the topic of the Flask session see these references:
1.2.1 Disclaimer: Keep your SECRET_KEY, secret!
If you expose this key your application becomes vulnerable to session replay attacks. Here is an example where an application exposed the SECRET_KEY during 404 errors. The example also illustrates how session replay works.
By default Flask does not expose the SECRET_KEY anywhere. It is up to you the developer to keep it that way!
1.3 Usage
1.3.1 Installation
$ pip install flask-cookie-decode1.3.2 Extracting the cookie using browser tools
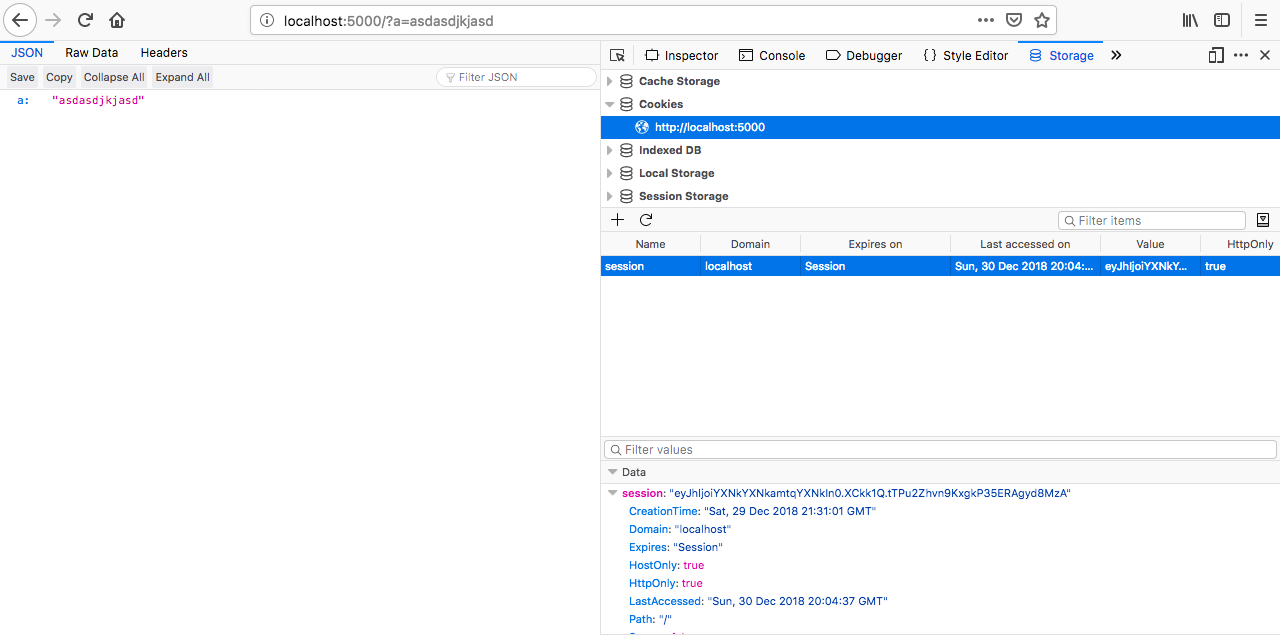
1.3.3 Example Flask app
See examples/app.py:
from flask import Flask, jsonify, session, request
from flask_cookie_decode import CookieDecode
app = Flask(__name__)
app.config.update({'SECRET_KEY': 'jlghasdghasdhgahsdg'})
cookie = CookieDecode()
cookie.init_app(app)
@app.route('/')
def index():
a = request.args.get('a')
session['a'] = a
return jsonify(dict(session))1.3.4 Examples using the CLI:
This extension will ship two CLI interfaces for dealing with decoding cookies. One requires a Flask application instance for the application you are wanting to debug. This method has the added benefit that the signature of the cookie can be verified, as your application instance has the SECRET_KEY used to sign the cookie. This method returns decoded cookie objects which can be seen in the examples below. This method can return a few different types of cookie objects depending on the state of the cookie. Please keep in mind that this extension provides only a thin-wrapper around the logic Flask uses to deal with cookies.
The second CLI interface is a tool for decoding cookies without the app secret. It cannot validate the signatures on the cookies or check the expirations and does not require the application instance like the other CLI. Intended for debugging purposes only.
1.3.4.1 CLI attached to application instance
A cookie with a valid signature:
$ export FLASK_APP=app.py
$ flask cookie decode eyJhIjoiYXNkYXNkamtqYXNkIn0.XCkk1Q.tTPu2Zhvn9KxgkP35ERAgyd8MzA
TrustedCookie(contents={'a': 'asdasdjkjasd'}, expiration='2019-01-30T20:04:37')A cookie with an invalid signature:
$ export FLASK_APP=app.py
$ flask cookie decode eyJhIjoiYXNkYXNkamtqYXNkIn0.XCkk1Q.tTPu2Zhvn9KxgkP35ERAgyd8MzA
UntrustedCookie(contents={'a': 'asdasdjkjasd'}, expiration='2019-01-30T20:04:37')An expired cookie:
$ export FLASK_APP=app.py
$ flask cookie decode eyJhIjoiYXNkYXNkamtqYXNkIn0.XCkk1Q.tTPu2Zhvn9KxgkP35ERAgyd8MzA
ExpiredCookie(contents={'a': 'asdasdjkjasd'}, expiration='2019-01-30T20:04:37')1.3.4.2 CLI that ships with package which only decodes
$ fcd decode eyJhIjoiYXNkYXNkamtqYXNkIn0
{
"a": "asdasdjkjasd"
}1.4 Documentation
1.5 License
MIT.
2 History
2.1 Flask_Cookie_Decode 0.4.3 (2025-03-09)
Chores
Re-releasing v0.4.2 as v0.4.3 (release)
2.2 Flask_Cookie_Decode 0.4.2 (2025-03-09)
Chores
Fix: DeprecationWarning: datetime.datetime.utcfromtimestamp() is deprecated Thanks to @miguelgrinberg for the blog post: https://blog.miguelgrinberg.com/post/it-s-time-for-a-change-datetime-utcnow-is-now-deprecated (#17)
2.3 Flask_Cookie_Decode 0.4.1 (2024-03-17)
Chores
Added a github action that runs a test suite with variety of Python and Flask versions. The github action also builds and deploys the package to Pypi. (actions)
2.4 Flask_Cookie_Decode 0.4.0 (2023-06-23)
Bugfixes
remove dependency on flask.helpers.total_seconds (#13)
2.5 Flask_Cookie_Decode 0.3.2 (2019-11-29)
Bugfixes
The fcd client now handles compressed cookies. (#10)
2.6 Flask_Cookie_Decode 0.3.1 (2019-11-29)
Features
Add the fcd CLI for reading cookies without a flask app. (#8)
2.7 Flask_Cookie_Decode 0.3.0 (2019-01-05)
2.7.1 Bugfixes
In all previous releases the CLI with the --timestamp CLI flag was actually returning the timestamp when the cookie was signed. Not the timestamp when the cookie expires, as it should have been doing.
In all previous releases there was no error handling for expired cookies. This release now returns a ExpiredCookie when it is detected. (#1)
2.7.2 Improved Documentation
Updates the documentation to include some more details about the way the Flask session works, and things you should be looking out for from a security perspective. The documentation also reflects the latest in terms of the way the CLI works. (#1)
2.8 0.1.0 (2018-12-29)
First release on PyPI.
Project details
Verified details
These details have been verified by PyPIProject links
GitHub Statistics
Maintainers
 wgwz
wgwz
Unverified details
These details have not been verified by PyPIMeta
- License: MIT License (MIT license)
- Author: Kyle Lawlor
- Tags flask_cookie_decode
-
Provides-Extra:
test
Classifiers
- Development Status
- Intended Audience
- License
- Natural Language
- Programming Language
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file flask_cookie_decode-0.4.3.tar.gz.
File metadata
- Download URL: flask_cookie_decode-0.4.3.tar.gz
- Upload date:
- Size: 114.0 kB
- Tags: Source
- Uploaded using Trusted Publishing? Yes
- Uploaded via: twine/6.1.0 CPython/3.12.9
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
a6ec13aa67b4320e3bd9fb8ebe0b7ba6bdb07cb5fbf2e2372027bf0bcd684377
|
|
| MD5 |
54d202077accae2c639aa6e74465eba6
|
|
| BLAKE2b-256 |
4488c05a83937b68b420dd55dc16c3e84a94649fe10573f7ffb87af1fad3786b
|
Provenance
The following attestation bundles were made for flask_cookie_decode-0.4.3.tar.gz:
Publisher:
action.yml on wgwz/flask-cookie-decode
-
Statement:
-
Statement type:
https://in-toto.io/Statement/v1 -
Predicate type:
https://docs.pypi.org/attestations/publish/v1 -
Subject name:
flask_cookie_decode-0.4.3.tar.gz -
Subject digest:
a6ec13aa67b4320e3bd9fb8ebe0b7ba6bdb07cb5fbf2e2372027bf0bcd684377 - Sigstore transparency entry: 179477346
- Sigstore integration time:
-
Permalink:
wgwz/flask-cookie-decode@642434ad6fcd0c04beca8ed8fb28031a113f3a1a -
Branch / Tag:
refs/tags/v0.4.3 - Owner: https://github.com/wgwz
-
Access:
public
-
Token Issuer:
https://token.actions.githubusercontent.com -
Runner Environment:
github-hosted -
Publication workflow:
action.yml@642434ad6fcd0c04beca8ed8fb28031a113f3a1a -
Trigger Event:
push
-
Statement type:
File details
Details for the file flask_cookie_decode-0.4.3-py2.py3-none-any.whl.
File metadata
- Download URL: flask_cookie_decode-0.4.3-py2.py3-none-any.whl
- Upload date:
- Size: 8.2 kB
- Tags: Python 2, Python 3
- Uploaded using Trusted Publishing? Yes
- Uploaded via: twine/6.1.0 CPython/3.12.9
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
892d61cd6fe9e05edb800bd7feb032a737cc0e79fb16f3c0efb5f95e14b2f754
|
|
| MD5 |
aa6963cf324ef8695c054c04f53960be
|
|
| BLAKE2b-256 |
08935a83154ed12fe0e2f7d2f56b61ed9e6b41ce6c7178c58c0411a9731694a7
|
Provenance
The following attestation bundles were made for flask_cookie_decode-0.4.3-py2.py3-none-any.whl:
Publisher:
action.yml on wgwz/flask-cookie-decode
-
Statement:
-
Statement type:
https://in-toto.io/Statement/v1 -
Predicate type:
https://docs.pypi.org/attestations/publish/v1 -
Subject name:
flask_cookie_decode-0.4.3-py2.py3-none-any.whl -
Subject digest:
892d61cd6fe9e05edb800bd7feb032a737cc0e79fb16f3c0efb5f95e14b2f754 - Sigstore transparency entry: 179477349
- Sigstore integration time:
-
Permalink:
wgwz/flask-cookie-decode@642434ad6fcd0c04beca8ed8fb28031a113f3a1a -
Branch / Tag:
refs/tags/v0.4.3 - Owner: https://github.com/wgwz
-
Access:
public
-
Token Issuer:
https://token.actions.githubusercontent.com -
Runner Environment:
github-hosted -
Publication workflow:
action.yml@642434ad6fcd0c04beca8ed8fb28031a113f3a1a -
Trigger Event:
push
-
Statement type:










