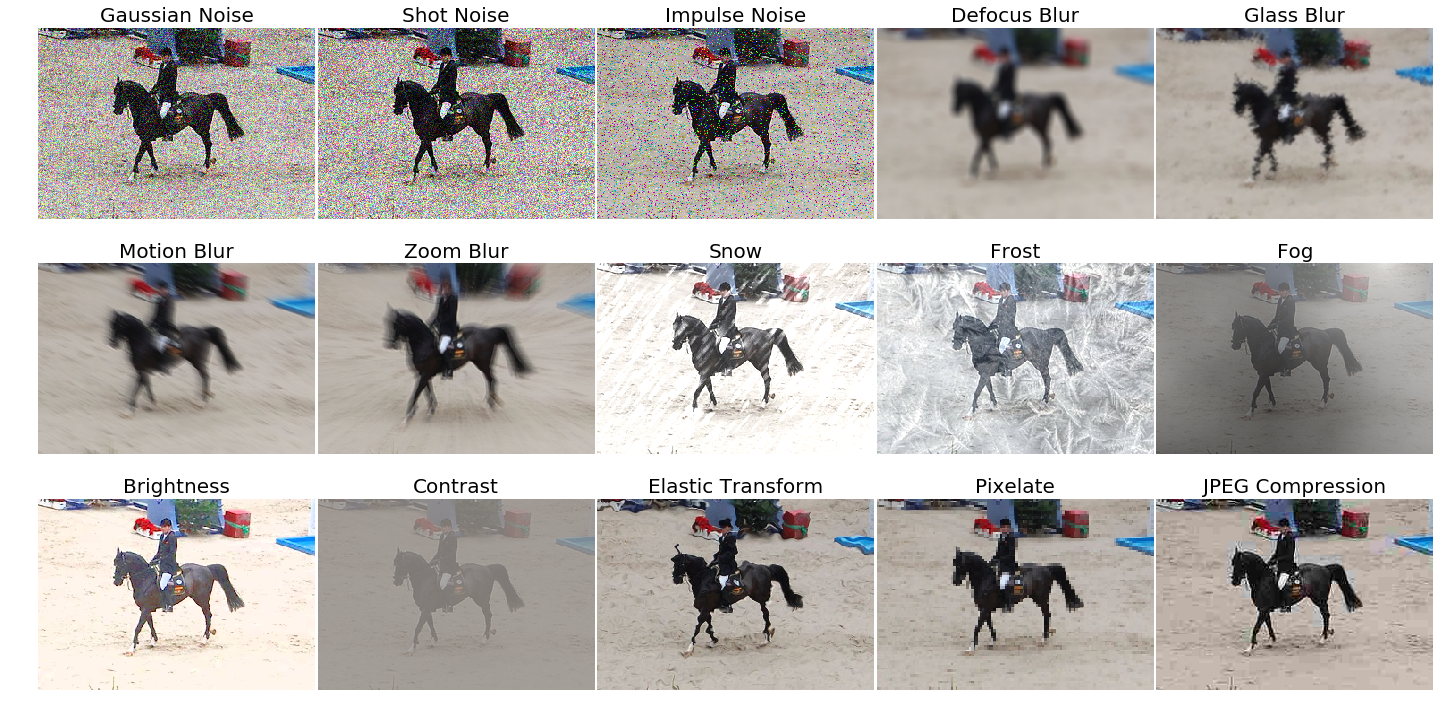
This package provides a set of image corruptions.
Project description
imagecorruptions
This package provides a set of corruptions that can be applied to images in order to benchmark the robustness of neural networks. These corruptions are not meant to be used as training data augmentation but rather to test the networks against unseen perturbations. For more information have a look at the paper on the original corruption package by Hendrycks and Dietterich: Benchmarking Neural Network Robustness to Common Corruptions and Surface Variations.
Installation and Usage
This package is pip installable via pip3 install imagecorruptions. An example of how to use the corruption function is given below:
from imagecorruptions import corrupt
...
corrupted_image = corrupt(image, corruption_name='gaussian_blur', severity=1)
...
Looping over all available corruptions can be done either by name or by index:
# via name
from imagecorruptions import get_corruption_names
for corruption in get_corruption_names():
for severity in range(5):
corrupted = corrupt(image, corruption_name=corruption, severity=severity+1)
...
# via number:
for i in range(15):
for severity in range(5):
corrupted = corrupt(image, corruption_number=i, severity=severity+1)
...
Note that the first 15 image corruptions are the common corruptions (the ones you get via get_corruption_names()). If you really wish to use these as data augmentation, there exist four additional validation corruptions which can be accessed via get_corruption_names('validation') which should then be used to test the corruption robustness of the trained model.
Citation
If you use our code or the imagecorruptions package, please consider citing:
@article{michaelis2019dragon,
title={Benchmarking Robustness in Object Detection:
Autonomous Driving when Winter is Coming},
author={Michaelis, Claudio and Mitzkus, Benjamin and
Geirhos, Robert and Rusak, Evgenia and
Bringmann, Oliver and Ecker, Alexander S. and
Bethge, Matthias and Brendel, Wieland},
journal={arXiv preprint arXiv:1907.07484},
year={2019}
}
Credit and Changelog
This package is an extension of the image corruption functions provided by Dan Hendrycks in the repository corruptions. The image corruptions implemented by Hendrycks are generalized to work on images with arbitrary image dimensions and aspect ratios aswell as on grayscale images. We furthermore removed the dependency to libmagickwand and the python api Wand and reimplemented the motion_blur in python.
Project details
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file imagecorruptions-1.1.2.tar.gz.
File metadata
- Download URL: imagecorruptions-1.1.2.tar.gz
- Upload date:
- Size: 2.1 MB
- Tags: Source
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/3.2.0 pkginfo/1.6.1 requests/2.25.0 setuptools/50.3.2 requests-toolbelt/0.9.1 tqdm/4.53.0 CPython/3.8.5
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
044e173f24d5934899bdbf3596bfbec917e8083e507eed583ab217abebbe084d
|
|
| MD5 |
f8b0c29ec4f791b8857f84f25a13019f
|
|
| BLAKE2b-256 |
22810e89d4524064b683cb3b0b5c5874e41307d730c473673051d3c68d52605f
|
File details
Details for the file imagecorruptions-1.1.2-py3-none-any.whl.
File metadata
- Download URL: imagecorruptions-1.1.2-py3-none-any.whl
- Upload date:
- Size: 2.1 MB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/3.2.0 pkginfo/1.6.1 requests/2.25.0 setuptools/50.3.2 requests-toolbelt/0.9.1 tqdm/4.53.0 CPython/3.8.5
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
d0e4bf529ba6fbb27d8aba1bde7c5db43bf2b969b2c767c11419e939e3e365b8
|
|
| MD5 |
9311416fb21be0bf95ef30207c3905d7
|
|
| BLAKE2b-256 |
3e40ff4a79ad7ab6463fe2fde7912b71084a6606e33676078a50b40a3377112b
|