Shamiko ga waruindayo
Project description
shamiko
shamiko is a library for inspecting running Python processes.
It can
- inspect Python processes
- obtain information about current frames and threads of the running process
- inject arbitrary code into specified frame and thread of the process
- attach the running process with pdb
Install
pip install shamiko
CLI
shamiko provides the command-line interface.
shamiko --help
Usage: shamiko [OPTIONS] PID COMMAND [ARGS]...
Arguments:
PID (int): PID of target Python process
Options:
-e, --executable (str): executable path of given PID
-c, --context (str): context directory of given PID
--help show help message
Commands:
inspect inspect the running process
attach attach a debugger to the running process
run-file inject a python script file into the running process
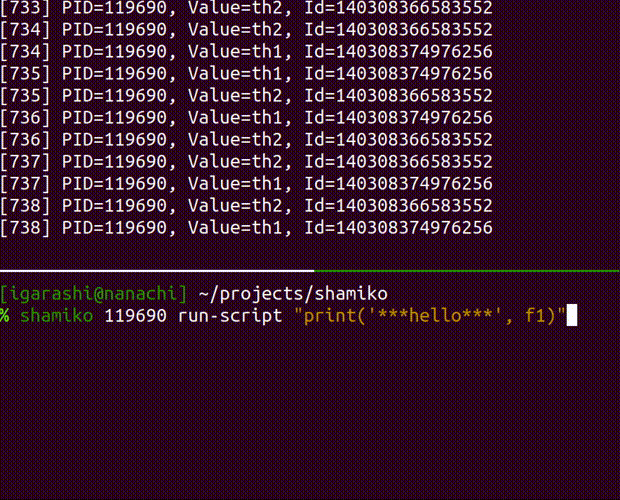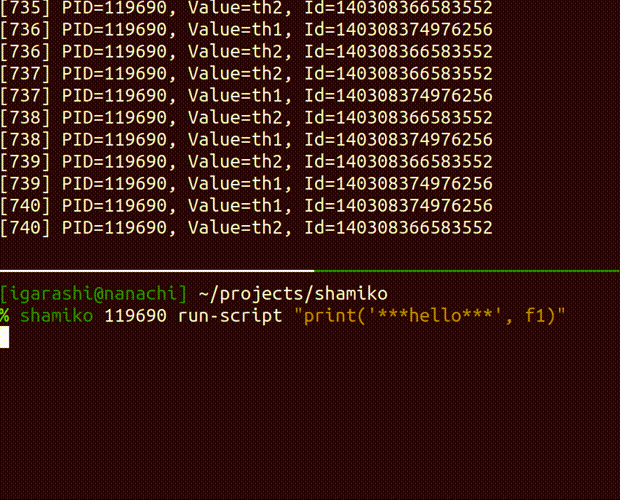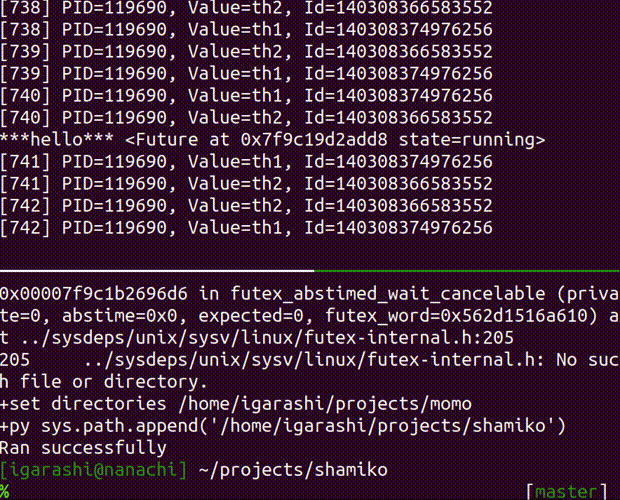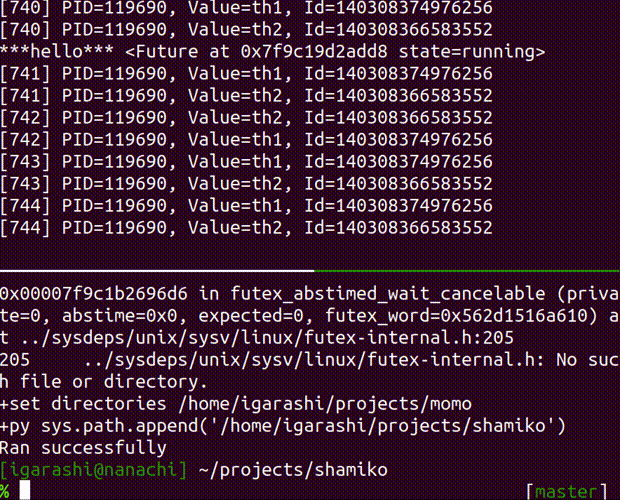
run-script inject a python code into the running process
shell launch an interactive shell
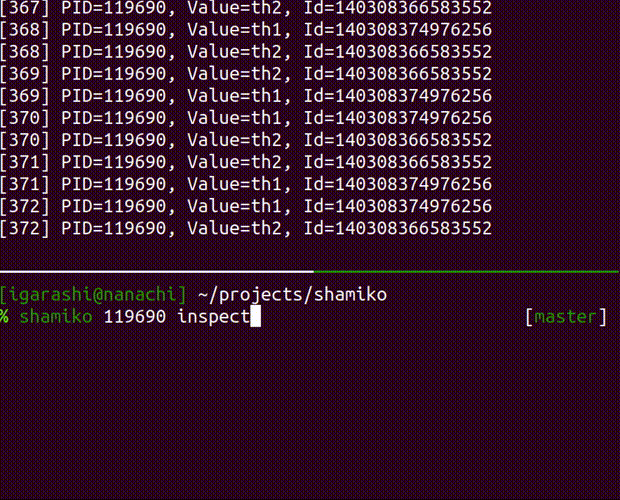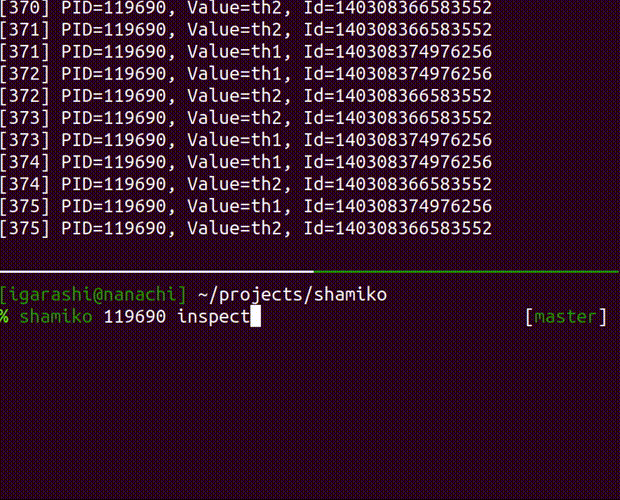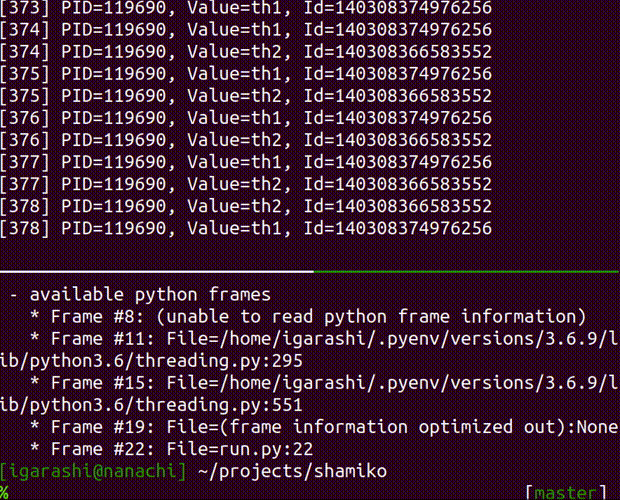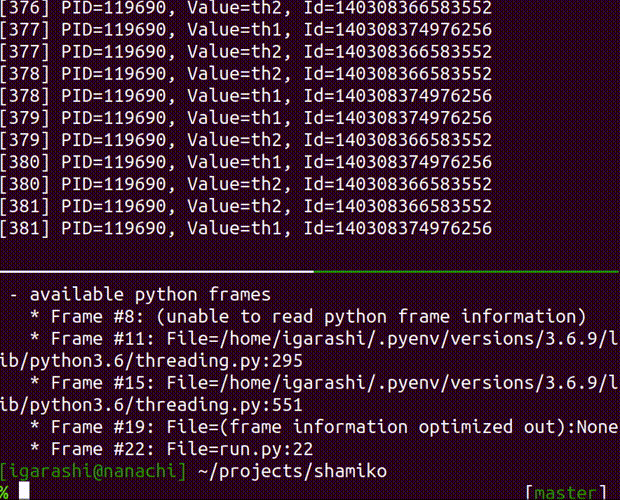
inspect
inspect the running process
Usage: shamiko PID inspect
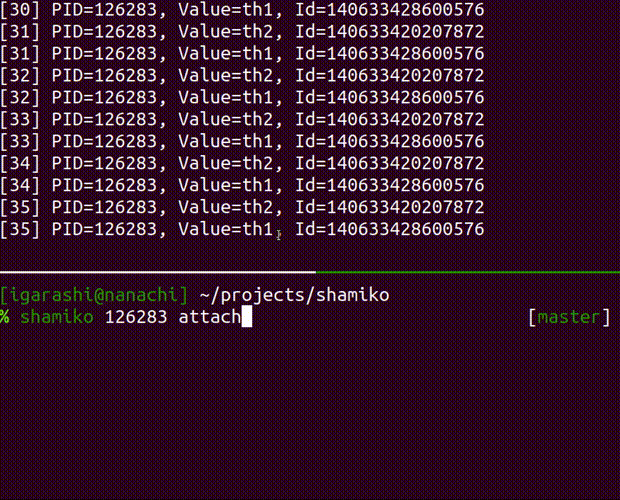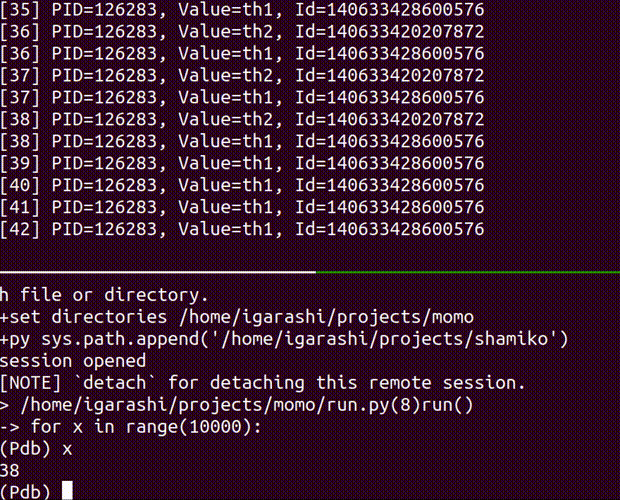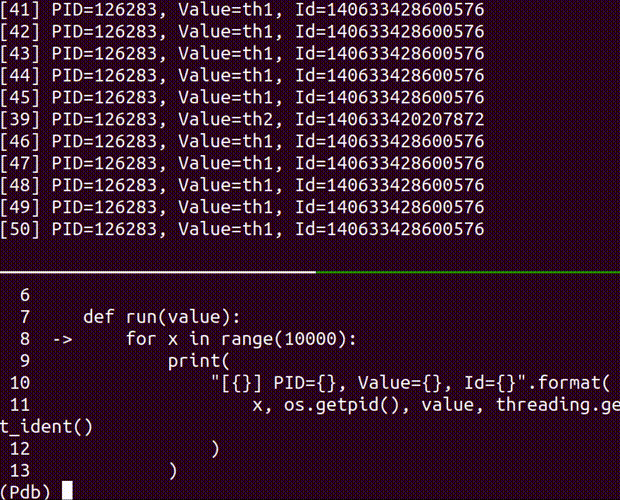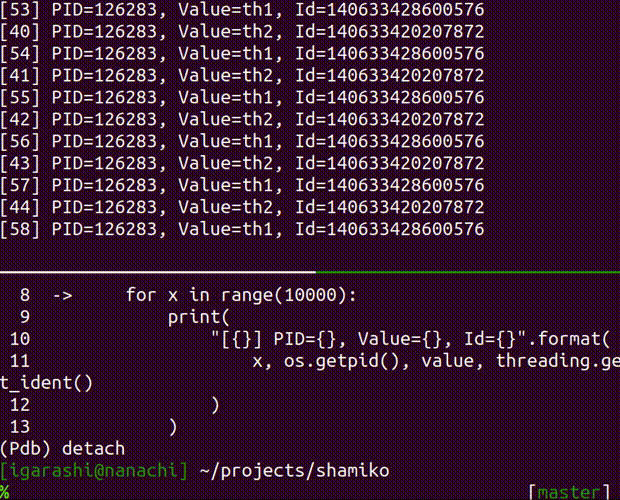
attach
attach a debugger to the running process
Usage: shamiko PID attach [OPTIONS]
Options:
--thread (int): thread id where you can obtain by `inspect` command
--frame (int): frame id where you can obtain by `inspect` command
--debugger (str): debugger type. available debuggers: [pdb]
run-file
inject a python script file into the running process
Usage: shamiko PID run-file [OPTIONS] FILE_PATH
Arguments:
FILE_PATH (str): a path of the python script that you want to inject into given PID
Options:
--thread (int): thread id where you can obtain by `inspect` command
--frame (int): frame id where you can obtain by `inspect` command
run-script
inject a python code into the running process
Usage: shamiko PID run-script [OPTIONS] SCRIPT
Arguments:
SCRIPT (str): a python code that you want to inject into given PID
Options:
--thread (int): thread id where you can obtain by `inspect` command
--frame (int): frame id where you can obtain by `inspect` command
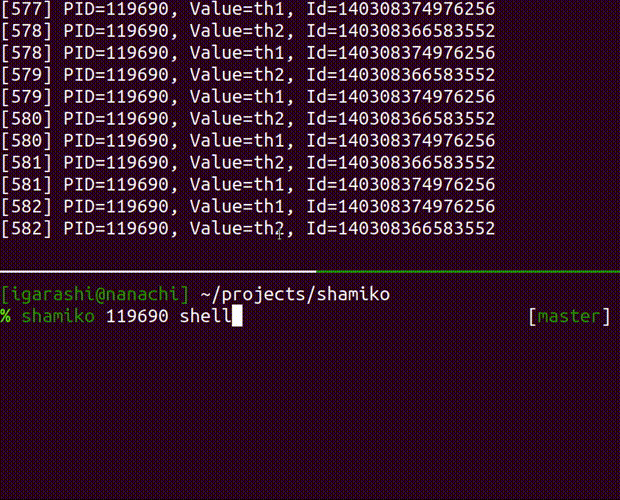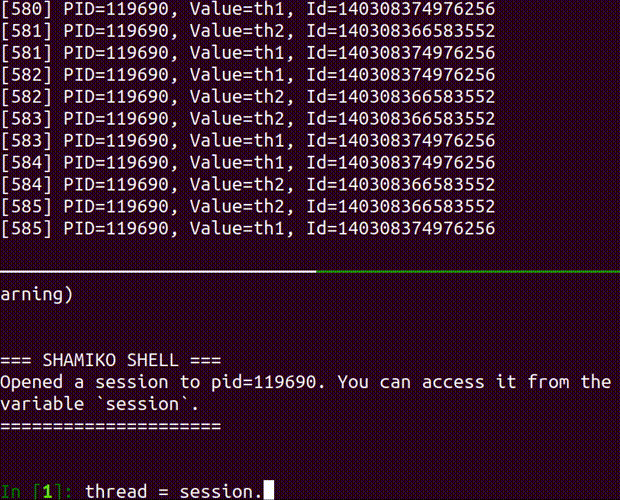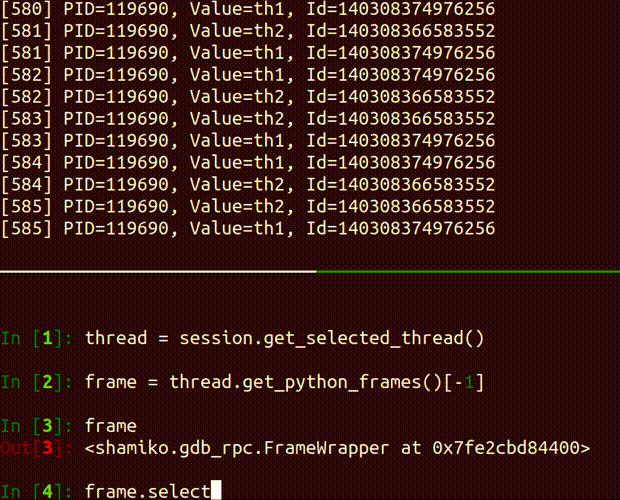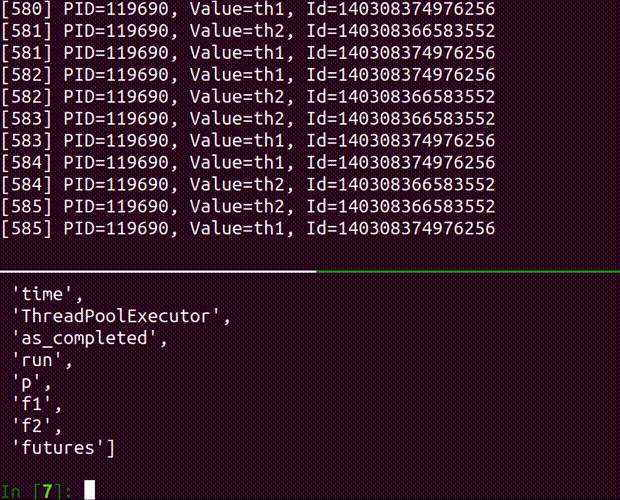
shell
launch an interactive shell
Usage: shamiko PID shell
FAQ
ptrace: Operation not permitted
Could not attach to process. If your uid matches the uid of the target
process, check the setting of /proc/sys/kernel/yama/ptrace_scope, or try
again as the root user. For more details, see /etc/sysctl.d/10-ptrace.conf
ptrace: Operation not permitted.
In most distributions, executing ptrace of non-child processes by a non-super user is disallowed. You can disable this temporarily by
echo 0 > /proc/sys/kernel/yama/ptrace_scope
auto-loading has been declined by your `auto-load safe-path' set to "$debugdir:$datadir/auto-load"
warning: File "/home/user/.pyenv/versions/3.6.9/bin/python3.6-gdb.py" auto-loading has been declined by your `auto-load safe
-path' set to "$debugdir:$datadir/auto-load".
shamiko uses the gdb Python extension script python-gdb.py.
To allow auto loading of this file, execute
echo "add-auto-load-safe-path [path to python-gdb.py]" >> ~/.gdbinit
To simply allow auto loading of all pathes, execute
echo "add-auto-load-safe-path /" >> ~/.gdbinit
Examples
- To allow Python 3.6 that you installed by pyenv
echo "add-auto-load-safe-path ~/.pyenv/shims/python3.6-gdb.py" >> ~/.gdbinit
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distributions
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file shamiko-0.1.0-py3-none-any.whl.
File metadata
- Download URL: shamiko-0.1.0-py3-none-any.whl
- Upload date:
- Size: 19.9 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/3.1.1 pkginfo/1.5.0.1 requests/2.22.0 setuptools/42.0.1 requests-toolbelt/0.9.1 tqdm/4.40.1 CPython/3.6.9
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
d7c4603f482bafa71a498a093cfdd6895714526447991e28832b094ac60d1c3c
|
|
| MD5 |
4afc425241998e5ee8498c4ab83e2acd
|
|
| BLAKE2b-256 |
98695701f249eed7b760980adcf6f29161daf0236a9cecf969b8087880196134
|