Wrapper to XGen/XGen8/ComNav/Hills/Interlogix NX-595E/UltraSync ZeroWire
Project description
UltraSync Python Tool
This tool is designed to allow 'API' access through a CLI wrapper to several types of alarm system IP modules that utilise the UltraSync+ mobile app. These modules are generally found in or can be added to systems produced by the below vendors:
- Hills Ltd (Business defunct in 2023, now operating as Aritech (a division of Kidde Global Solutions))
- United Technologies Corporation (Alarm division defunct in 2021)
The tool can be leveraged by other scripts/integrations such as HA UltraSync for integration into Home Automation systems.
Compatibility
The tool is written to be compatible with the Hills/Aritech NX-595E ComNav, Interlogix xGen/xGen8 (such as NXG-8-Z-BO), and ZeroWire UltraSync-based alarm solutions. It is possible that more systems are supported that utilise the UltraSync+ app and share similar code structure, however any not explicitly listed here are untested by the code author/contributors.
Note: ComNav modules runinng firmware version P004000-12 and above disable access to programming menus for cybersecurity reasons. To enable programming menus permanently, turn on Feature Location 19 Option 6. With programming menus disabled, users will only be allowed access through remote/online login (over the internet). Compatibility for remote login cannot be added to this tool due to there being no public API available, and no official vendor support for this method outside of the UltraSync+ mobile app. Later model Aritech Reliance XR series alarm systems include a built-in IP module that allows local network access as it is not affected by the same vulnerabilities.
ComNav Product Security Advisory
As the original manufacturer(s) are mostly defunct, new software development is generally not expected at the vendor level. Newer Aritech ATS alarm systems utilise the Advisor Advanced Pro mobile app instead of UltraSync+ and are unlikely to be supported by this tool.
UltraSync Hub
How Does It Work?
-
First you need to install it; this part is easy:
# Install ultrasync onto your system pip install ultrasync
-
Create a configuration file that identifies:
- The hostname or IP address of the alarm system on your local network.
- Your alarm system login User ID (case-sensitive)
- Your alarm system login pin.
Note: You can generally only be logged into the alarm system with the same user once; a subsequent login with the same user logs out the other. Since this tool actively polls and maintains a login session to your system, it can prevent you from being able to log into at the same time elsewhere (via it's website). It is strongly recommended that you create a second user account on your system dedicated to just this service.
# An example of what would be found in your configuration file: # Use hashtags/pound symbols (#) to optionally add comments # Syntax is simply <key>: <value> # # For local network login you must specify an ip/hostname, user, and pin # host: 192.168.0.30 user: My Username (case-sensitive) pin: 1234
-
Use the --scene (-s) to set your security system's alarm scene. The possible options are:
disarm,away,stay,fire,medical, andpanic. The latter 3 are only available for NX-595E currently.# By default if no --config= (-c) is specified, one will be automatically # loaded from the following location (if present): # ~/.ultrasync # ~/.config/ultrasync # Windows users can store their default configuration files here: # %APPDATA%/UltraSync/config # %LOCALAPPDATA%/UltraSync/config # Disarm your security system ultrasync --scene disarm # Arm your security system and activate all of your sensors when setting the # away mode macro ultrasync --scene away # Arm your security system and only activate your perimeter sensors: ultrasync --scene stay # Trigger the fire alarm (ComNav Only): ultrasync --scene fire # Trigger the medical alarm (ComNav Only): ultrasync --scene medical # Trigger the panic alarm (ComNav Only): ultrasync --scene panic
What Else Can It Do?
-
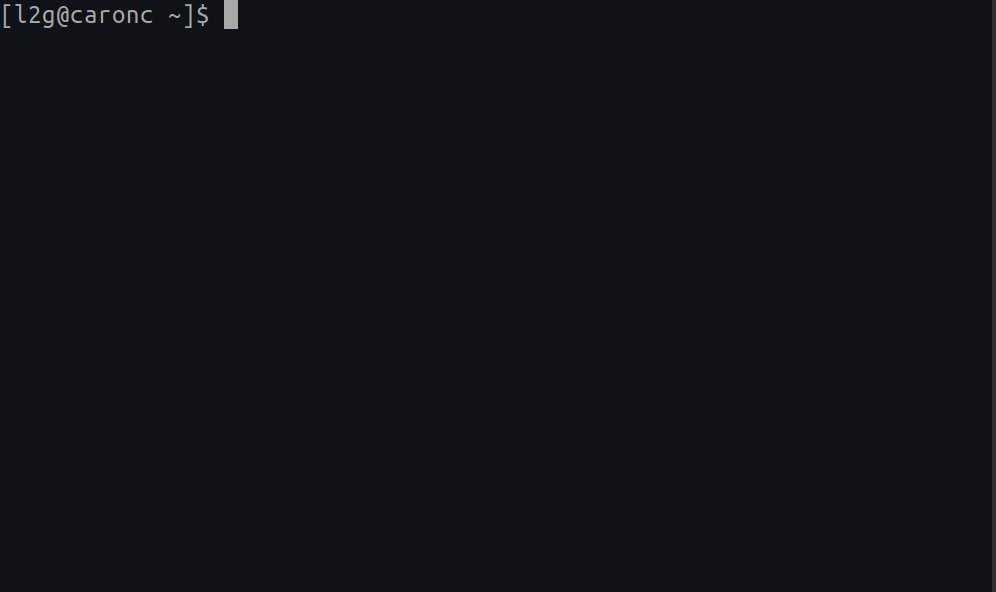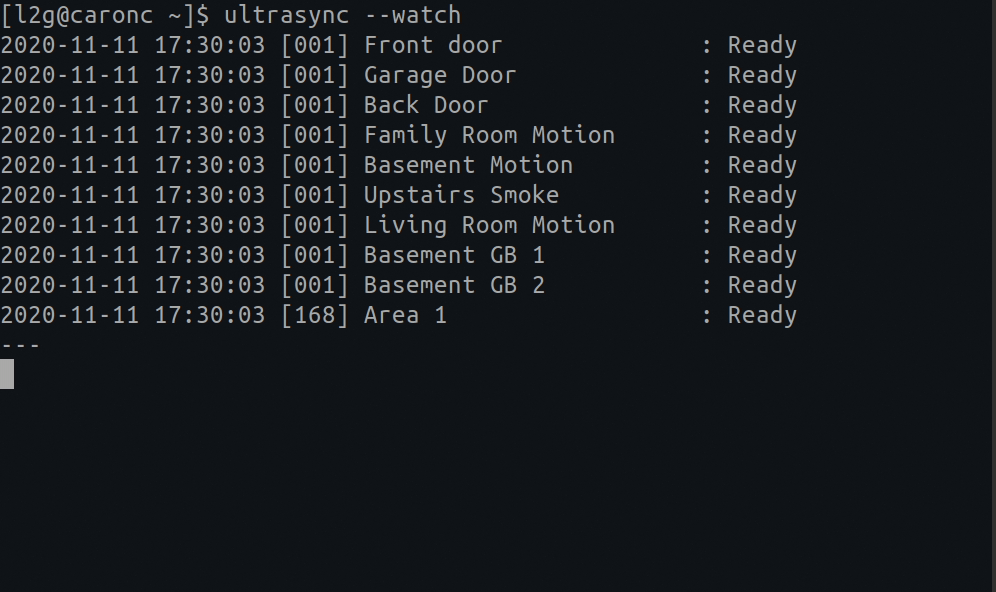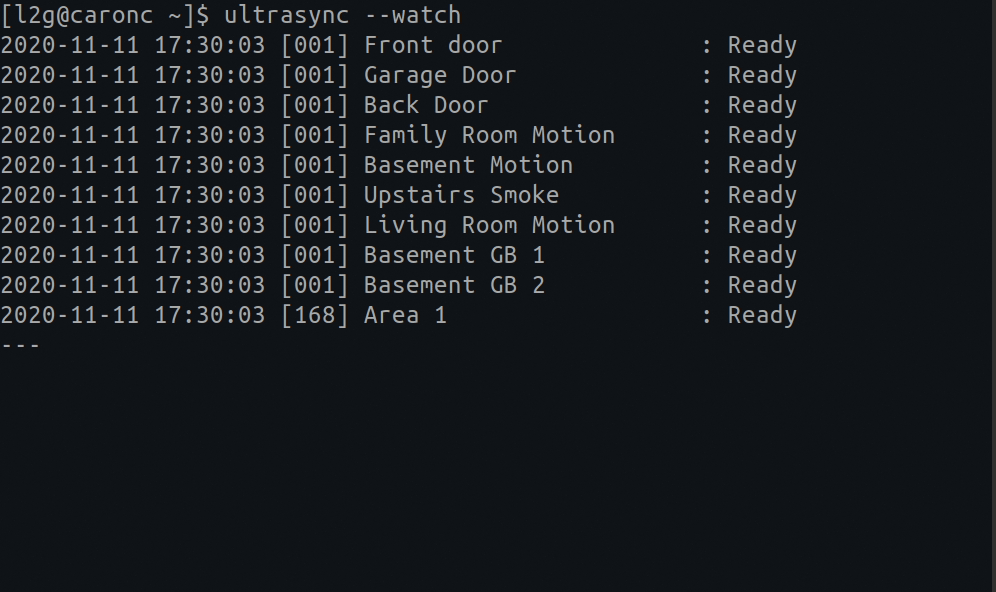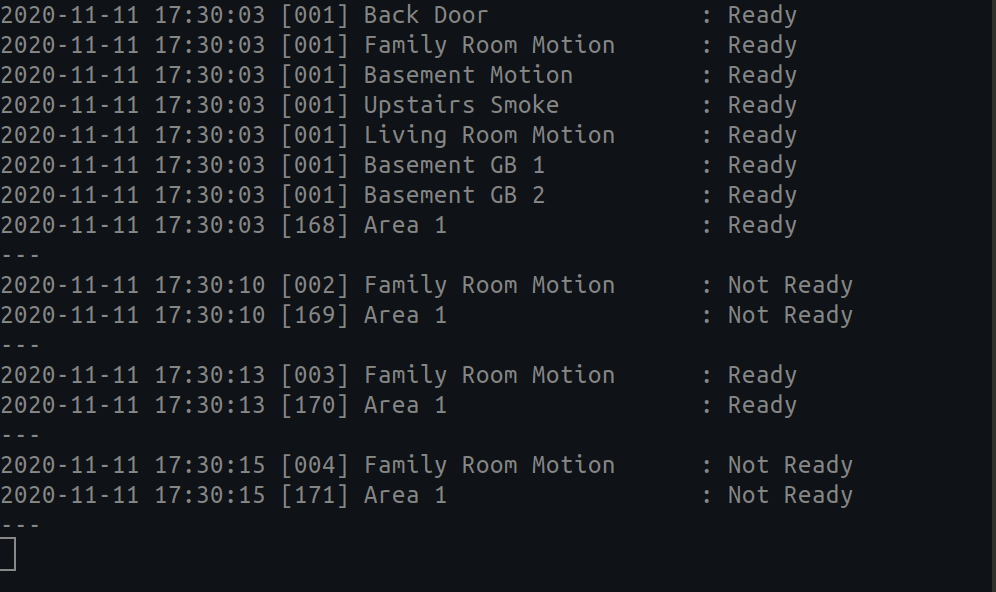
You can put up a live monitor of your device by typing the following:
# A live monitoring of your home security system: ultrasync --watch
-
You can generate a snapshot (in JSON format) that greatly details everything taking place through your security home setup. It provides MUCH greater detail than the
--watchwhich allows it to also be integrated with Home Assistant.# Print a JSON formatted snapshot of all home security details ultrasync --details
-
You can perform a dump of all of the web based files (that I've found to be useful so far) to disk. This makes troubleshooting much easier.
# Extracts information from your system that can be # incredibly useful in debugging and/or adding enhancements # later on: ultrasync --debug-dump
The debug content gets written to a zip file (residing in the same folder you ran this command from) in the form of:
YYYYmmddHHMMSS.ultrasync-dump.zip.
Reverse Proxy
If you've exposed your panel to the internet, you can access it by setting your host to the full URL to it (instead of just the hosthame/ip). For example:
# A sample UltraSync configuration that requires you to pass through
# a proxy in order to get to your destination:
host: https://your.security.panel/
user: My Username
pin: 1234
If you've also protected your panel behind an additional user/pass combo using Basic Auth at the reverse proxy level, you can pass through it like so:
# A sample ultrasync configuration that requires you to pass through
# a proxy expecting authentication in order to get to your destination:
host: https://user:pass@your.security.panel/
user: My Username
pin: 1234
# You can also optionally turn off the secure hostname verification
# by using the verify switch. But default this is set to yes if not
# specified:
verify: no
Global Variables
You can also (optionally) set the following global variables to provide the equivalent of what the configuration file could have. If a configuration file is also loaded, it's settings will always prevail. If an entry is missing, then the environment variable is used instead (if it's defined):
| Global Variable | Description |
|---|---|
| ULTRASYNC_PIN | Provides the pin variable to the library |
| ULTRASYNC_USER | Provides the user variable to the library |
| ULTRASYNC_HOST | Provides the host variable to the library |
| ULTRASYNC_SSL_VERIFY | Provides the verify variable to the library (optional, defaults to yes if not set) |
Disclaimer
This tool was created through reverse engineering and has been expanded through crowdsourced data. All of this code was generated through trial and error since there is no official documentation available that explains the registers. If you can help out by filling in some of the blanks throughout the code base, I would be greatly appreciative of it! Alternatively buying me a coffee greatly inspires me to continue improving the application.
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file ultrasync-1.0.3.tar.gz.
File metadata
- Download URL: ultrasync-1.0.3.tar.gz
- Upload date:
- Size: 86.0 kB
- Tags: Source
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/6.1.0 CPython/3.13.7
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
d32ddc798fda99a1db569a903a1f378f4efcd770af4488d4784841871f6eaf26
|
|
| MD5 |
1aebf3b9a07813a375fd50d1a415d89f
|
|
| BLAKE2b-256 |
9a536d217aab4ab68ab7c63bee97cc9a7fcb32625dc669731d79ce2ce13dcd79
|
File details
Details for the file ultrasync-1.0.3-py3-none-any.whl.
File metadata
- Download URL: ultrasync-1.0.3-py3-none-any.whl
- Upload date:
- Size: 31.7 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/6.1.0 CPython/3.13.7
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
23e7825b74ad4b0036c26bf3d55b89e0a4c8bed78683a59205a80a0de7b1a6f4
|
|
| MD5 |
033f218687246918d6d57ee9783917b9
|
|
| BLAKE2b-256 |
3363af8a89d0748f8fd78ca3a62f7506a20abeef51f846d7a33bf179b593d624
|