WHite-box Adversarial Toolbox (WHAT) - Python Library for Deep Learning Security
Project description

WHite-box Adversarial Toolbox (WHAT)
A Python Library for Deep Learning Security that focuses on Real-time White-box Attacks.
Installation
pip install whitebox-adversarial-toolbox
Usage (CLI)
Usage: what [OPTIONS] COMMAND [ARGS]...
The CLI tool for WHitebox-box Adversarial Toolbox (what).
Options:
--help Show this message and exit.
Commands:
attack Manage Attacks
example Manage Examples
model Manage Deep Learning Models
Useful commands:
# List supported models
$ what model list
# List supported Attacks
$ what attack list
# List available examples
$ what example list
Available models:
[x] 1 : YOLOv3 ( Darknet ) Object Detection YOLOv3 pretrained on MS COCO dataset.
[x] 2 : YOLOv3 ( Mobilenet ) Object Detection YOLOv3 pretrained on MS COCO dataset.
[x] 3 : YOLOv3 Tiny ( Darknet ) Object Detection YOLOv3 Tiny pretrained on MS COCO dataset.
[x] 4 : YOLOv3 Tiny ( MobileNet ) Object Detection YOLOv3 Tiny pretrained on MS COCO dataset.
[x] 5 : YOLOv4 ( Darknet ) Object Detection YOLOv4 pretrained on MS COCO dataset.
[x] 6 : YOLOv4 Tiny ( Darknet ) Object Detection YOLOv4 Tiny pretrained on MS COCO dataset.
[x] 7 : SSD ( MobileNet v1 ) Object Detection SSD pretrained on VOC-2012 dataset.
[x] 8 : SSD ( MobileNet v2 ) Object Detection SSD pretrained on VOC-2012 dataset.
[x] 9 : FasterRCNN ( VGG16 ) Object Detection Faster-RCNN pretrained on VOC-2012 dataset.
[x] 10 : YOLOX X-Large Object Detection YOLOX-X pretrained on MS COCO dataset.
[x] 11 : YOLOX Large Object Detection YOLOX-L pretrained on MS COCO dataset.
[x] 12 : YOLOX Medium Object Detection YOLOX-M pretrained on MS COCO dataset.
[x] 13 : YOLOX Small Object Detection YOLOX-S pretrained on MS COCO dataset.
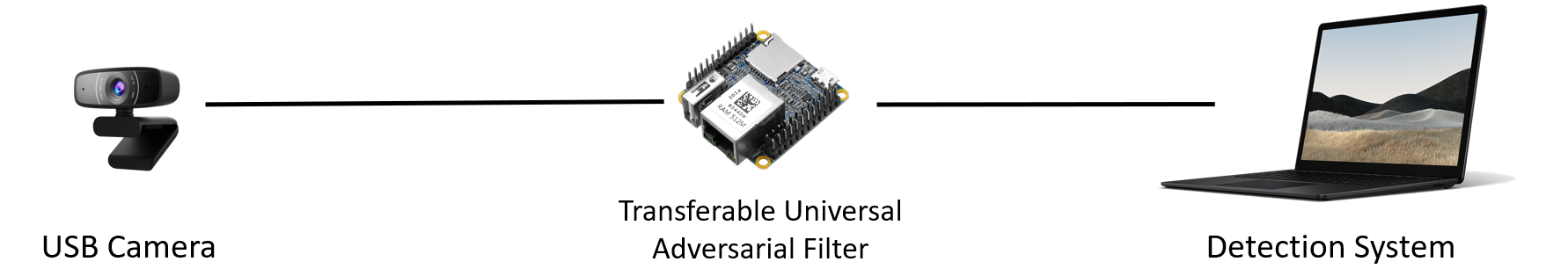
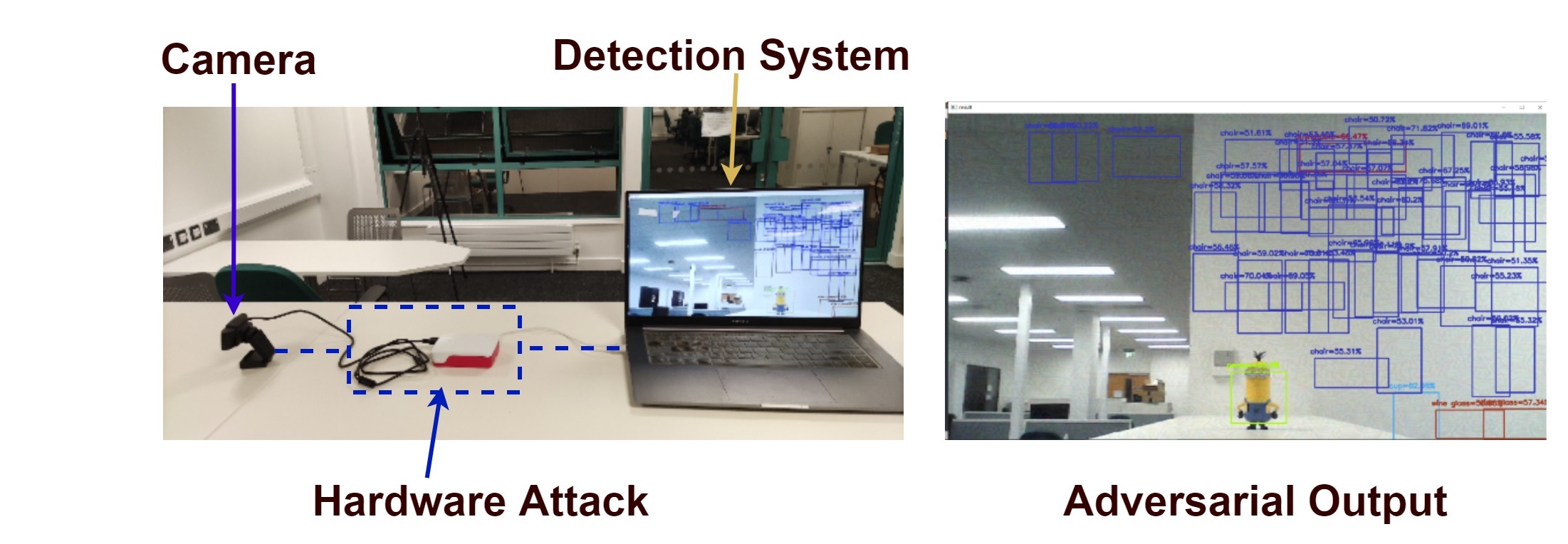
A Man-in-the-Middle Hardware Attack
The Universal Adversarial Perturbation (UAP) can be deployed using a Man-in-the-Middle Hardware Attack.
[ Talk ] [ Video ] [ Paper ] [ Code ]
The Man-in-the-Middle Attack consists of two steps:
- Step 1: Generating the perturbation.
- Step 2: Deploying the perturbation.
Project details
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
File details
Details for the file whitebox_adversarial_toolbox-0.2.1.tar.gz.
File metadata
- Download URL: whitebox_adversarial_toolbox-0.2.1.tar.gz
- Upload date:
- Size: 133.8 kB
- Tags: Source
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/5.1.0 CPython/3.8.0
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | 3989373ce21edc7fbf8bfe6d9b2f565389e7d46111d124dd14404591e814fc7d |
|
| MD5 | 25ab5d40fd1962b512f4b14d55b17a05 |
|
| BLAKE2b-256 | 351435cfc9017e82ea6cde341aeafc752aa2408f0913fce114ef62d7ced4b762 |
File details
Details for the file whitebox_adversarial_toolbox-0.2.1-py3-none-any.whl.
File metadata
- Download URL: whitebox_adversarial_toolbox-0.2.1-py3-none-any.whl
- Upload date:
- Size: 191.2 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/5.1.0 CPython/3.8.0
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | ebf30a4c4c2bd5b92c24229fe9e9a1903413fcfadee6764fd0222f5fdaf4fd7c |
|
| MD5 | cdb73a651608cabc422be49634300431 |
|
| BLAKE2b-256 | c43d5a9d7fc0b5b97fd11437214705bf45091aee46974b1420496cfd31afdf8c |