Parse, Audit, Query, Build, and Modify Cisco IOS-style and JunOS-style configs
Project description
ciscoconfparse
Introduction: What is ciscoconfparse?
Short answer: ciscoconfparse is a Python library that helps you quickly answer questions like these about your Cisco configurations:
- What interfaces are shutdown?
- Which interfaces are in trunk mode?
- What address and subnet mask is assigned to each interface?
- Which interfaces are missing a critical command?
- Is this configuration missing a standard config line?
It can help you:
- Audit existing router / switch / firewall / wlc configurations
- Modify existing configurations
- Build new configurations
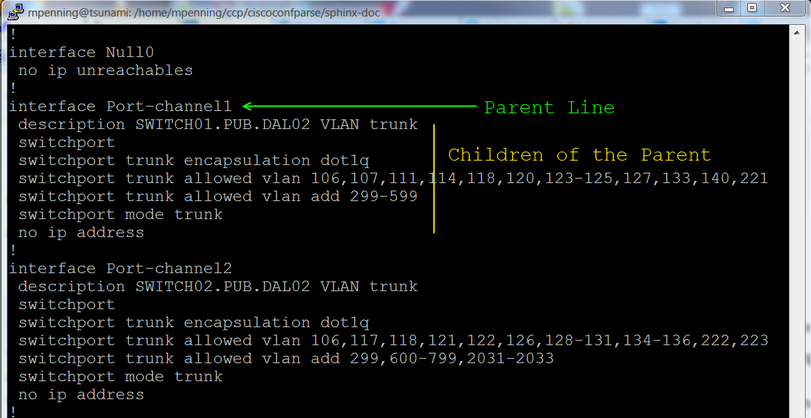
Speaking generally, the library examines an IOS-style config and breaks it into a set of linked parent / child relationships. You can perform complex queries about these relationships.
Generic Usage
The following code will parse a configuration stored in
exampleswitch.conf and select interfaces that are shutdown.
In this case, the parent is a line containing interface and
the child is a line containing the word shutdown.
from ciscoconfparse2 import CiscoConfParse
parse = CiscoConfParse('exampleswitch.conf', syntax='ios')
for intf_obj in parse.find_parent_objects('^interface', '^\s+shutdown'):
print("Shutdown: " + intf_obj.text)
The next example will find the IP address assigned to interfaces.
from ciscoconfparse2 import CiscoConfParse
parse = CiscoConfParse('exampleswitch.conf', syntax='ios')
for ccp_obj in parse.find_objects('^interface'):
intf_name = ccp_obj.re_match_typed('^interface\s+(\S.+?)$')
# Search children of all interfaces for a regex match and return
# the value matched in regex match group 1. If there is no match,
# return a default value: ''
intf_ip_addr = ccp_obj.re_match_iter_typed(
r'ip\saddress\s(\d+\.\d+\.\d+\.\d+)\s', result_type=str,
group=1, default='')
print(f"{intf_name}: {intf_ip_addr}")
Cisco IOS Factory Usage
CiscoConfParse has a special feature that abstracts common IOS / NXOS / ASA / IOSXR fields; at this time, it is only supported on those configuration types. You will see factory parsing in CiscoConfParse code as parsing the configuration with factory=True.
Are you releasing licensing besides GPLv3?
I will not. however, if it's truly a problem for your company, there are commercial solutions available (to include purchasing the project, or hiring me).
What if we don't use Cisco IOS?
Don't let that stop you.
As of original CiscoConfParse 1.2.4, you can parse brace-delimited configurations into a Cisco IOS style (see Github Issue #17), which means that CiscoConfParse can parse these configurations:
- Juniper Networks Junos
- Palo Alto Networks Firewall configurations
- F5 Networks configurations
CiscoConfParse also handles anything that has a Cisco IOS style of configuration, which includes:
- Cisco IOS, Cisco Nexus, Cisco IOS-XR, Cisco IOS-XE, Aironet OS, Cisco ASA, Cisco CatOS
- Arista EOS
- Brocade
- HP Switches
- Force 10 Switches
- Dell PowerConnect Switches
- Extreme Networks
- Enterasys
- Screenos
Docs
- The latest copy of the docs are archived on the web
Installation and Downloads
-
Use
poetryfor Python3.x... :python -m pip install ciscoconfparse2
What is the pythonic way of handling script credentials?
- Never hard-code credentials
- Use python-dotenv
Is this a tool, or is it artwork?
That depends on who you ask. Many companies use CiscoConfParse as part of their network engineering toolbox; others regard it as a form of artwork.
Pre-requisites
The ciscoconfparse2 python package requires Python versions 3.7+ (note: Python version 3.7.0 has a bug - ref Github issue #117, but version 3.7.1 works); the OS should not matter.
Other Resources
- Dive into Python3 is a good way to learn Python
- Team CYMRU has a Secure IOS Template, which is especially useful for external-facing routers / switches
- Cisco's Guide to hardening IOS devices
- Center for Internet Security Benchmarks (An email address, cookies, and javascript are required)
Bug Tracker and Support
- Please report any suggestions, bug reports, or annoyances with a github bug report.
- If you're having problems with general python issues, consider searching for a solution on Stack Overflow. If you can't find a solution for your problem or need more help, you can ask on Stack Overflow or reddit/r/Python.
- If you're having problems with your Cisco devices, you can contact:
Dependencies
Unit-Tests and Development
- We are manually disabling some SonarCloud alerts with:
#pragma warning disable S1313#pragma warning restore S1313- Where
S1313is a False-positive that SonarCloud flags - Those
#pragma warninglines should be carefully-fenced to ensure that we don't disable a SonarCloud alert that is useful.
Semantic Versioning and Conventional Commits
- At this point, ciscoconfparse2 does NOT adhere to Semantic Versioning
- Although we added commitizen as a dev dependency, we are NOT enforcing commit rules (such as Conventional Commits) yet.
Execute Unit tests
The project's test workflow checks ciscoconfparse2 on Python versions 3.7 and higher, as well as a pypy JIT executable.
If you already git cloned the repo and want to manually run tests either run with make test from the base directory, or manually run with pytest in a unix-like system...
$ cd tests
$ pytest ./test*py
...
Execute Test Coverage Line-Miss Report
If you already have have pytest and pytest-cov installed, run a test line miss report as shown below.
$ # Install the latest ciscoconfparse2
$ # (assuming the latest code is on pypi)
$ pip install -U ciscoconfparse2
$ pip install -U pytest-cov
$ cd tests
$ pytest --cov-report=term-missing --cov=ciscoconfparse2 ./
...
Editing the Package
This uses the example of editing the package on a git branch called develop...
git clone https://github.com/mpenning/ciscoconfparse2cd ciscoconfparse2git branch developgit checkout develop- Add / modify / delete on the
developbranch make test- If tests run clean,
git commitall the pending changes on thedevelopbranch - If you plan to publish this as an official version rev, edit the version number in pyproject.toml. In the future, we want to integrate
commitizento manage versioning. git checkout maingit merge developmake testgit push origin mainmake pypi
Sphinx Documentation
Building the ciscoconfparse2 documentation tarball comes down to this one wierd trick:
cd sphinx-doc/pip install -r ./requirements.txt; # install Sphinx dependenciespip install -r ../requirements.txt; # install ccp dependenciesmake html
License and Copyright
ciscoconfparse2 is licensed GPLv3
- Copyright (C) 2023 David Michael Pennington
The word "Cisco" is a registered trademark of Cisco Systems.
Author
ciscoconfparse2 was written by David Michael Pennington (mike [~at~] pennington [.dot.] net).
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file ciscoconfparse2-0.2.0.tar.gz.
File metadata
- Download URL: ciscoconfparse2-0.2.0.tar.gz
- Upload date:
- Size: 403.9 kB
- Tags: Source
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/4.0.2 CPython/3.11.2
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
c01b0d92b3a481a957f73747bc5dab4cdb66f0a6cba14de6a8a33bb4dd94169a
|
|
| MD5 |
f3af40cb29d0b9afcc574a6845442683
|
|
| BLAKE2b-256 |
fc529cb4ae14c795ab5c01ab08c5dc387638b0ac9c7b73d4e117e7ef257e90d1
|
File details
Details for the file ciscoconfparse2-0.2.0-py3-none-any.whl.
File metadata
- Download URL: ciscoconfparse2-0.2.0-py3-none-any.whl
- Upload date:
- Size: 256.3 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? No
- Uploaded via: twine/4.0.2 CPython/3.11.2
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
d4a4c8b61096c1f8adc83b6f0757807099b3692ec215540c2f9909674e01cae1
|
|
| MD5 |
f040285a106d277dd28bf736037d9180
|
|
| BLAKE2b-256 |
873746f2d9d48f6e182a1a9732239d7f3b46e91a829abefc88d7c70580abfead
|