Nautobot plugin to model firewall objects.
Project description
Nautobot Firewall Models Plugin
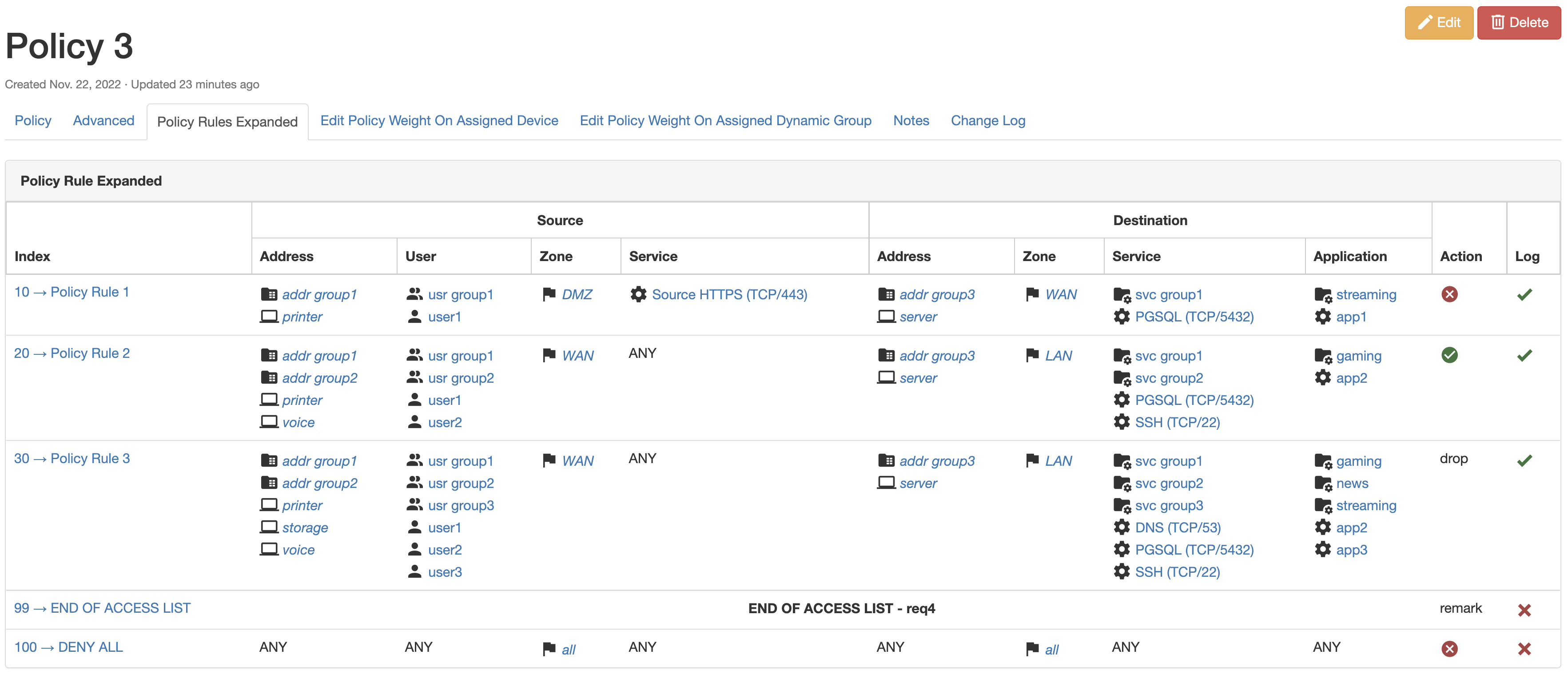
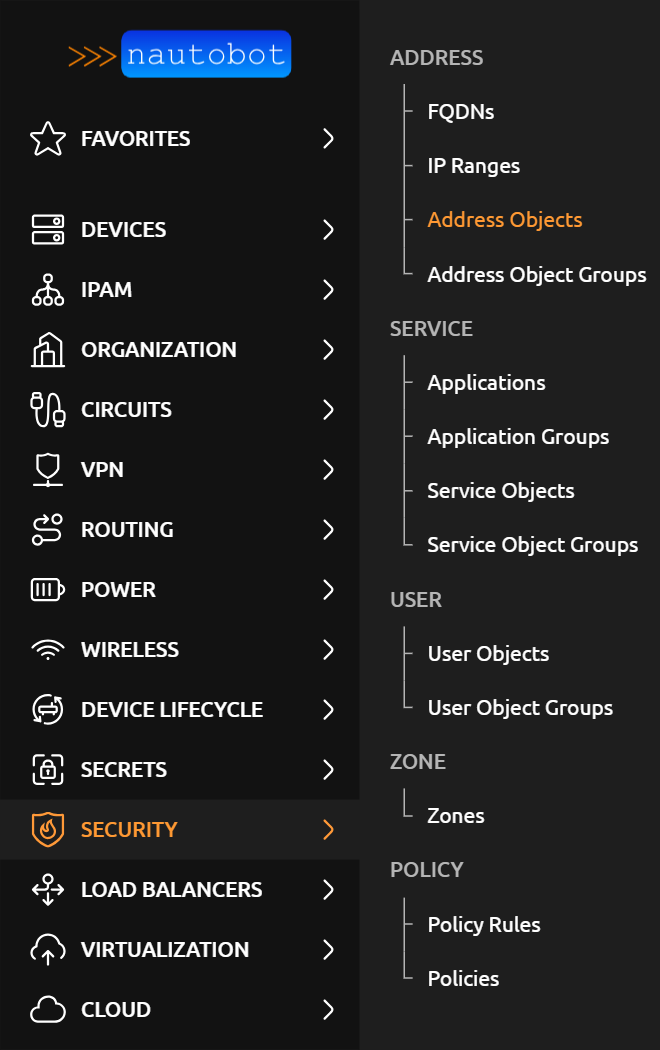
A plugin for Nautobot that is meant to model layer 4 firewall policies and/or extended access control lists.
Future development will include the ability to onboard an existing access list from a device and the ability to generate device configuration.
Installation
The plugin is available as a Python package in PyPI and can be installed with pip:
pip install nautobot-firewall-models
The plugin is compatible with Nautobot 1.4.0 and higher
To ensure Nautobot Firewall Models Plugin is automatically re-installed during future upgrades, create a file named local_requirements.txt (if not already existing) in the Nautobot root directory (alongside requirements.txt) and list the nautobot-firewall-models package:
# echo nautobot-firewall-models >> local_requirements.txt
Once installed, the plugin needs to be enabled in your nautobot_config.py
# In your nautobot_config.py
PLUGINS = ["nautobot_firewall_models"]
Optional Settings
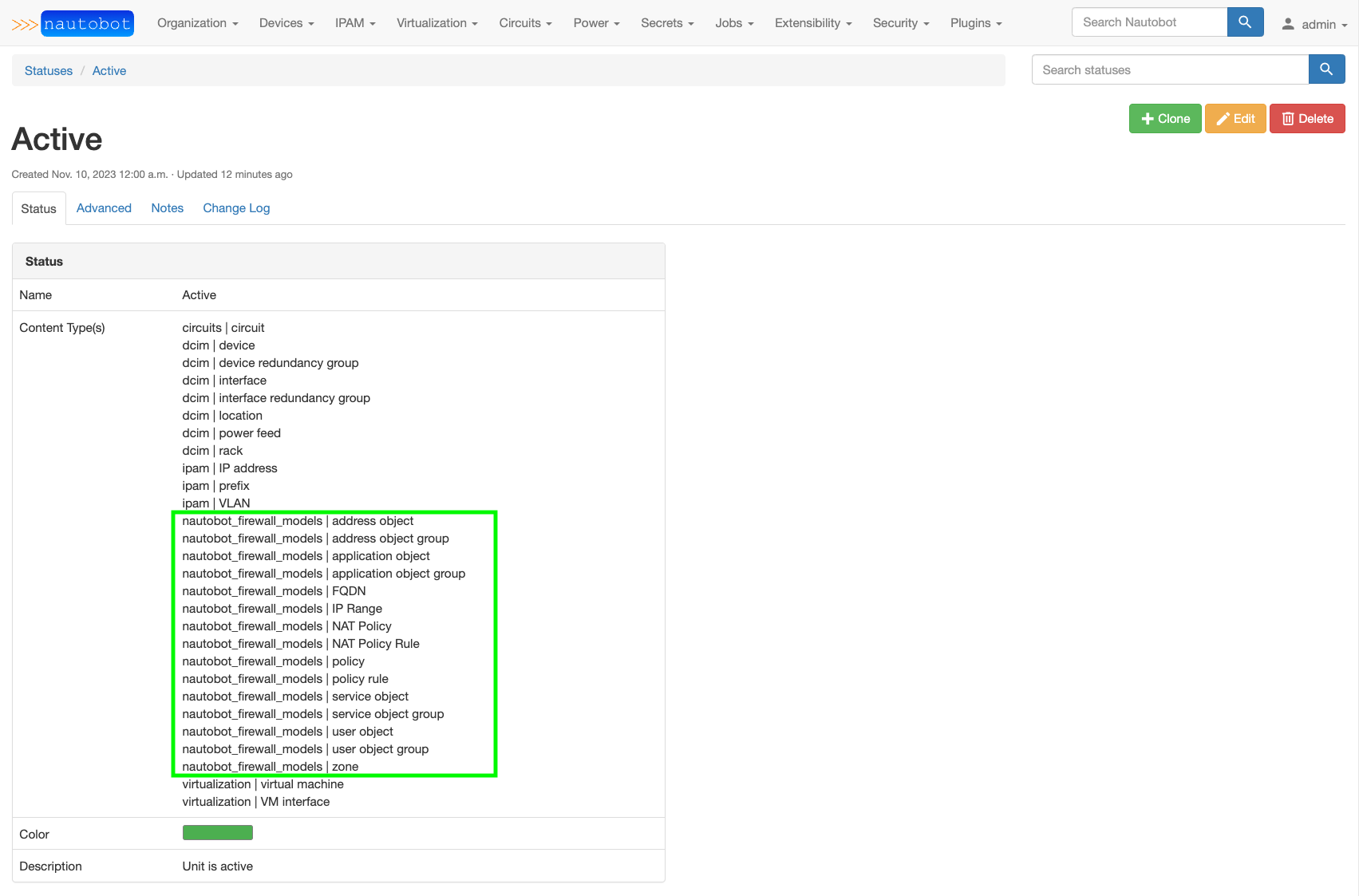
Models provided by this plugin have a status attribute and the default status is set to use active. This corresponds to the pre-built Nautobot Active Status object.
Use the default_status plugin configuration setting to change the default value for the status attribute.
PLUGINS_CONFIG = {
"nautobot_firewall_models": {
"default_status": "active"
"allowed_status": ["active"], # default shown, `[]` allows all
"capirca_remark_pass": True,
"capirca_os_map": {
"cisco_ios": "cisco",
"arista_eos": "arista",
},
# "custom_capirca": "my.custom.func", # provides ability to overide capirca logic
}
}
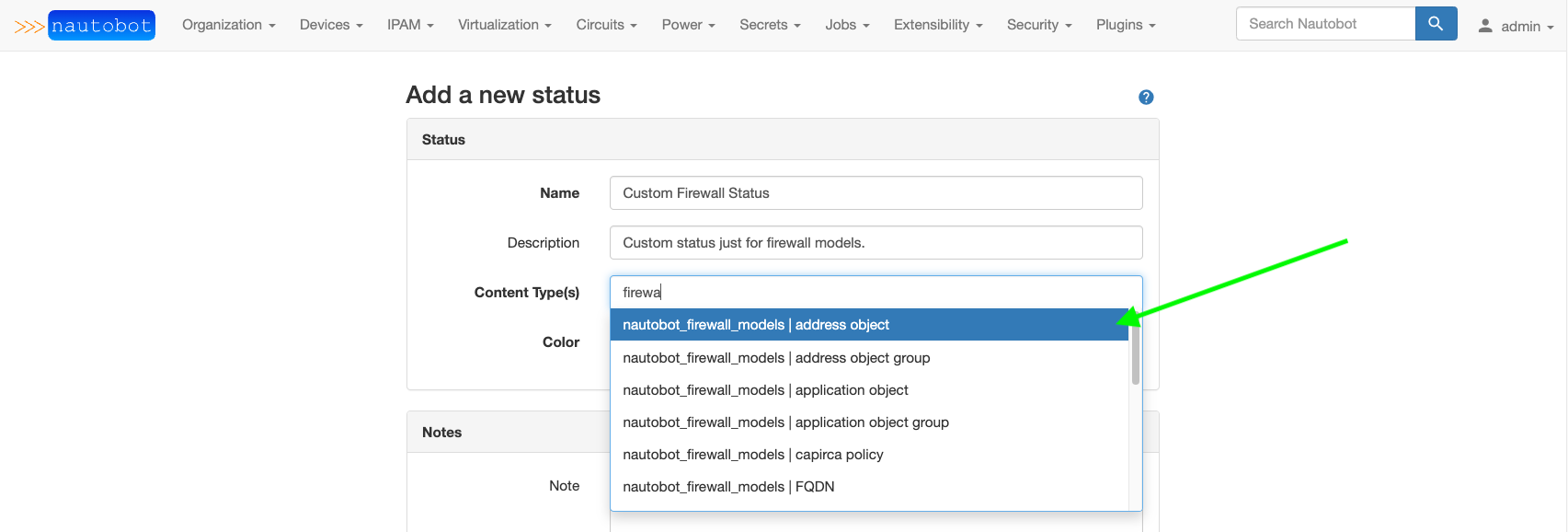
The value assigned to default_status must match the slug of an existing Nautobot Status object. That Status object must have all of the Firewall Models listed in the Content Type associations. See examples below on selecting the Content Type(s) when creating/editing a Status object and the pre-built Active Status with firewall content types added.
Screenshots
Documentation
Documentation is hosted on ReadTheDocs at Nautobot Firewall Models Plugin.
Contributing
Pull requests are welcomed and automatically built and tested against multiple version of Python and multiple version of Nautobot through TravisCI.
The project is packaged with a light development environment based on docker-compose to help with the local development of the project and to run the tests within TravisCI.
The project is following Network to Code software development guideline and is leveraging:
- Black, Pylint, Bandit and pydocstyle for Python linting and formatting.
- Django unit test to ensure the plugin is working properly.
Questions
For any questions or comments, please check the FAQ first and feel free to swing by the Network to Code slack channel (channel #networktocode). Sign up here
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Hashes for nautobot_firewall_models-1.2.0a1.tar.gz
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | d2bbe5f4e504ea1b0f929b28e9f41e7a863a186641c42e371ad75a2602d6ec59 |
|
| MD5 | 823a2a085beefd34f965cce8aec5884a |
|
| BLAKE2b-256 | bac196546b6b34bacef5eb47578066dc78f3fec9d8555341692491f244f0deb9 |
Hashes for nautobot_firewall_models-1.2.0a1-py3-none-any.whl
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | 8722e3a56c71c0d61f785698d12d6e958e937aa5e1a7149903510cad3b236caf |
|
| MD5 | c3956f403764c82a294deb5f903801b2 |
|
| BLAKE2b-256 | 997097ca10bc3e5e8a96278f5084d8fd5ba5d88cca657ff9cc2b5d5d48fdd66d |