vunnel ~= 'vulnerability data funnel'
Project description
vunnel
A tool for fetching, transforming, and storing vulnerability data from a variety of sources.
Supported data sources:
- Alpine (https://secdb.alpinelinux.org)
- Amazon (https://alas.aws.amazon.com/AL2/alas.rss & https://alas.aws.amazon.com/AL2022/alas.rss)
- Azure (https://github.com/microsoft/AzureLinuxVulnerabilityData)
- Debian (https://security-tracker.debian.org/tracker/data/json & https://salsa.debian.org/security-tracker-team/security-tracker/raw/master/data/DSA/list)
- Echo (https://advisory.echohq.com/data.json)
- GitHub Security Advisories (https://api.github.com/graphql)
- NVD (https://services.nvd.nist.gov/rest/json/cves/2.0)
- Oracle (https://linux.oracle.com/security/oval)
- RedHat (https://www.redhat.com/security/data/oval)
- SLES (https://ftp.suse.com/pub/projects/security/oval)
- Ubuntu (https://launchpad.net/ubuntu-cve-tracker)
- Wolfi (https://packages.wolfi.dev)
Prerequisites
The following system tools must be available on your PATH:
- git - Required by some providers that fetch data from git repositories
Installation
With pip:
pip install vunnel
With docker:
docker run \
--rm -it \
-v $(pwd)/data:/data \
-v $(pwd)/.vunnel.yaml:/.vunnel.yaml \
ghcr.io/anchore/vunnel:latest \
run nvd
Where:
- the
datavolume keeps the processed data on the host - the
.vunnel.yamluses the host application config (if present) - you can swap
latestfor a specific version (same as the git tags)
See the vunnel package for a full listing of available tags.
Getting Started
List the available vulnerability data providers:
$ vunnel list
alpine
amazon
chainguard
debian
echo
github
mariner
minimos
nvd
oracle
rhel
sles
ubuntu
wolfi
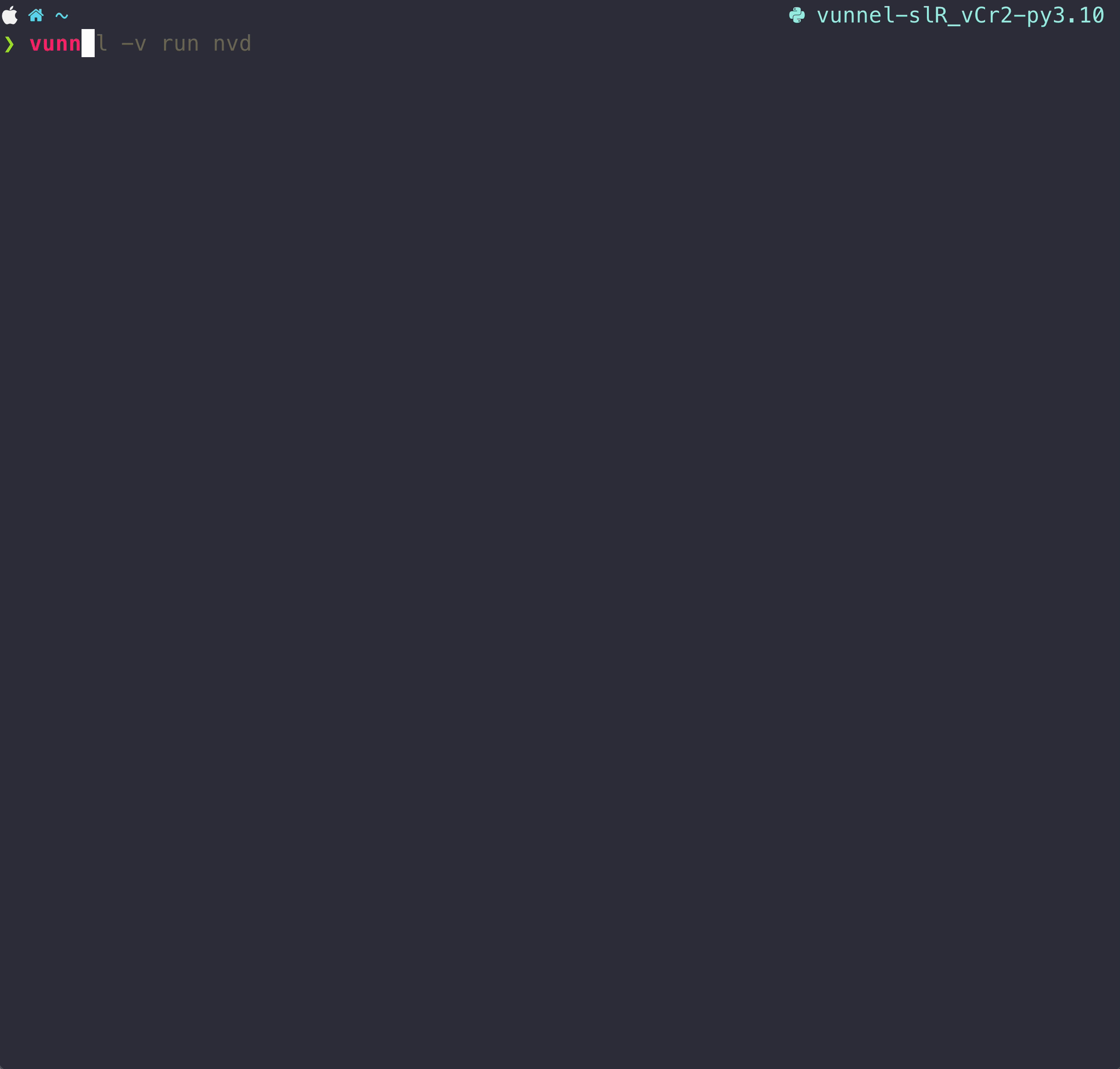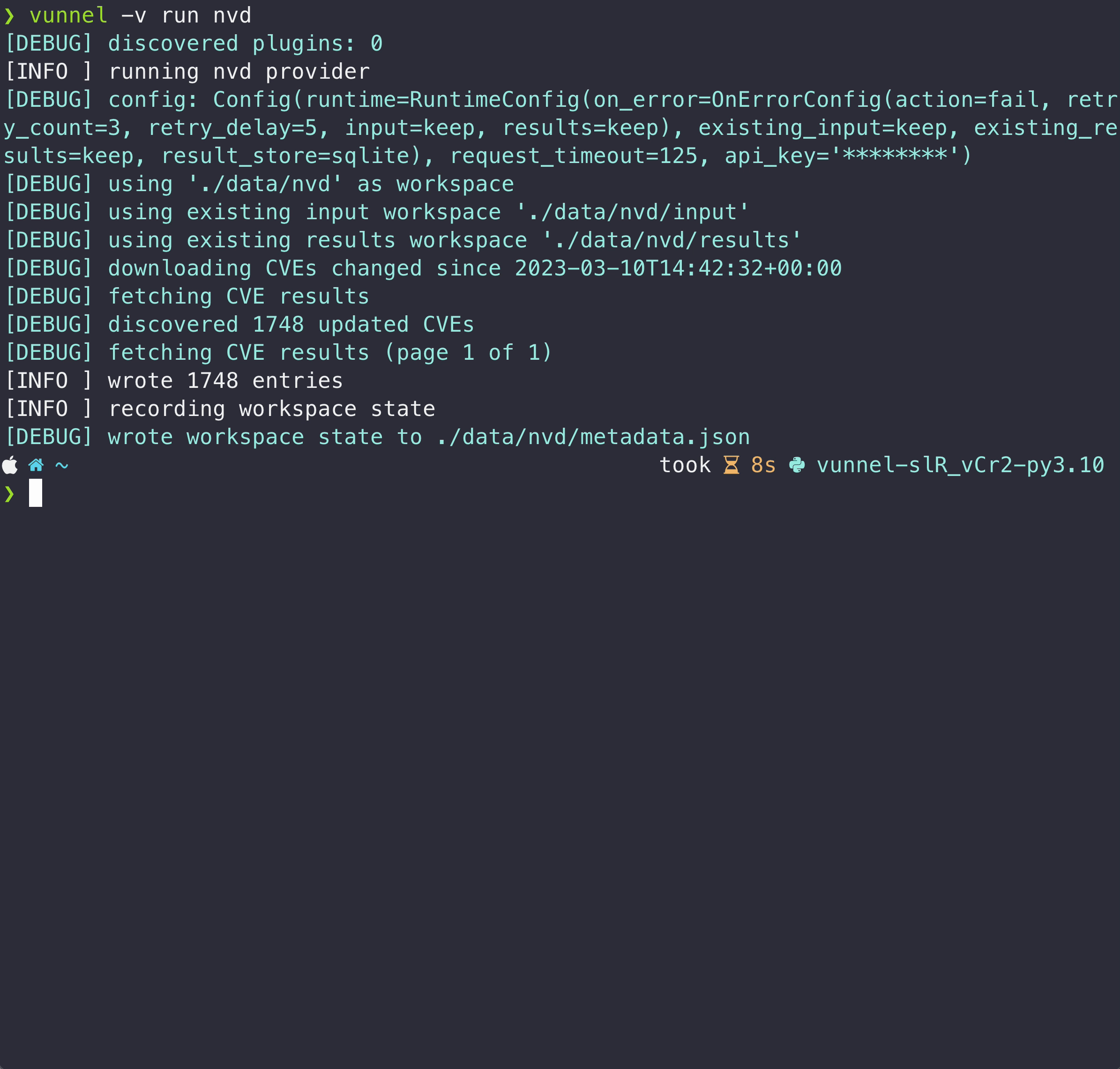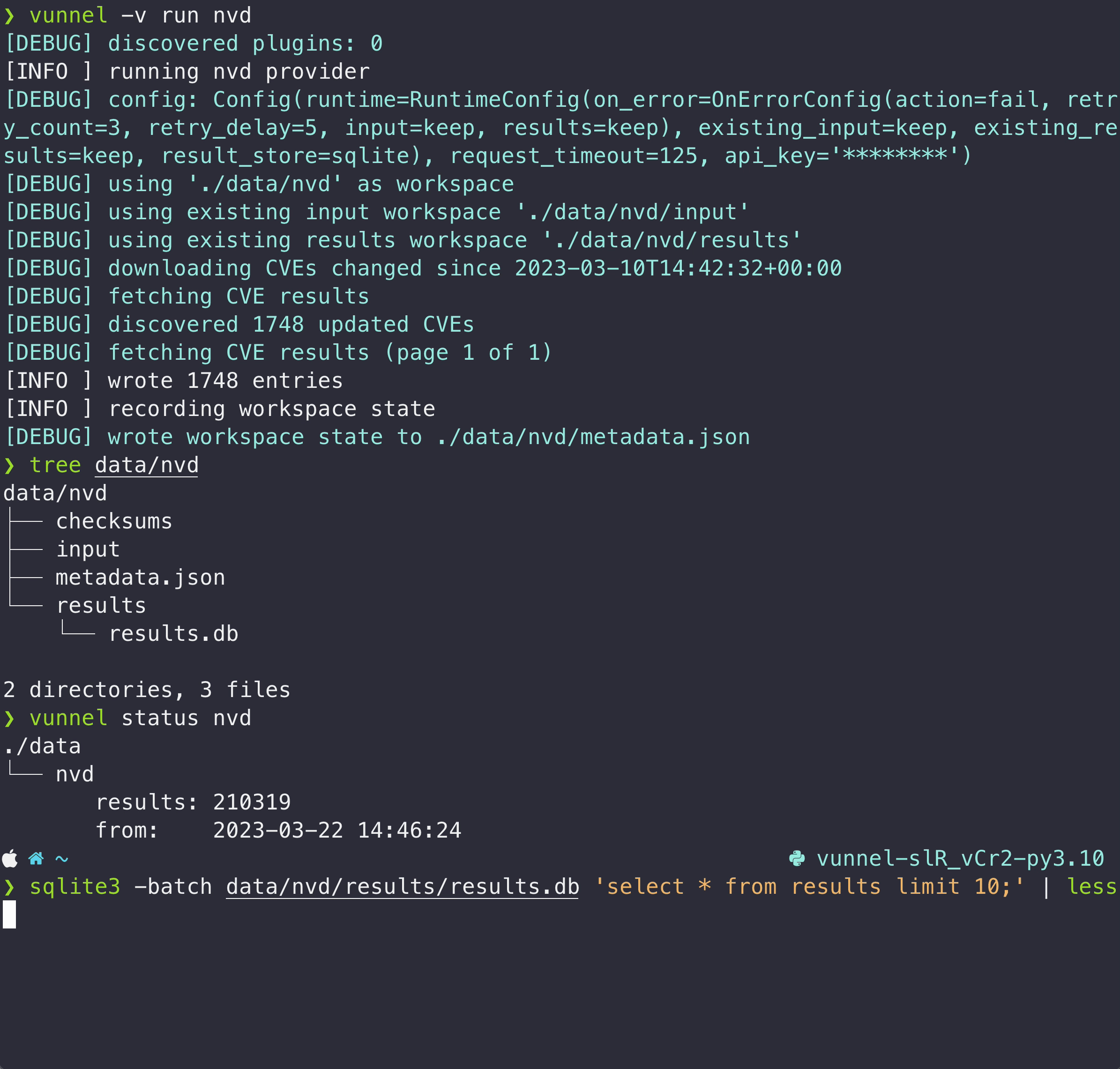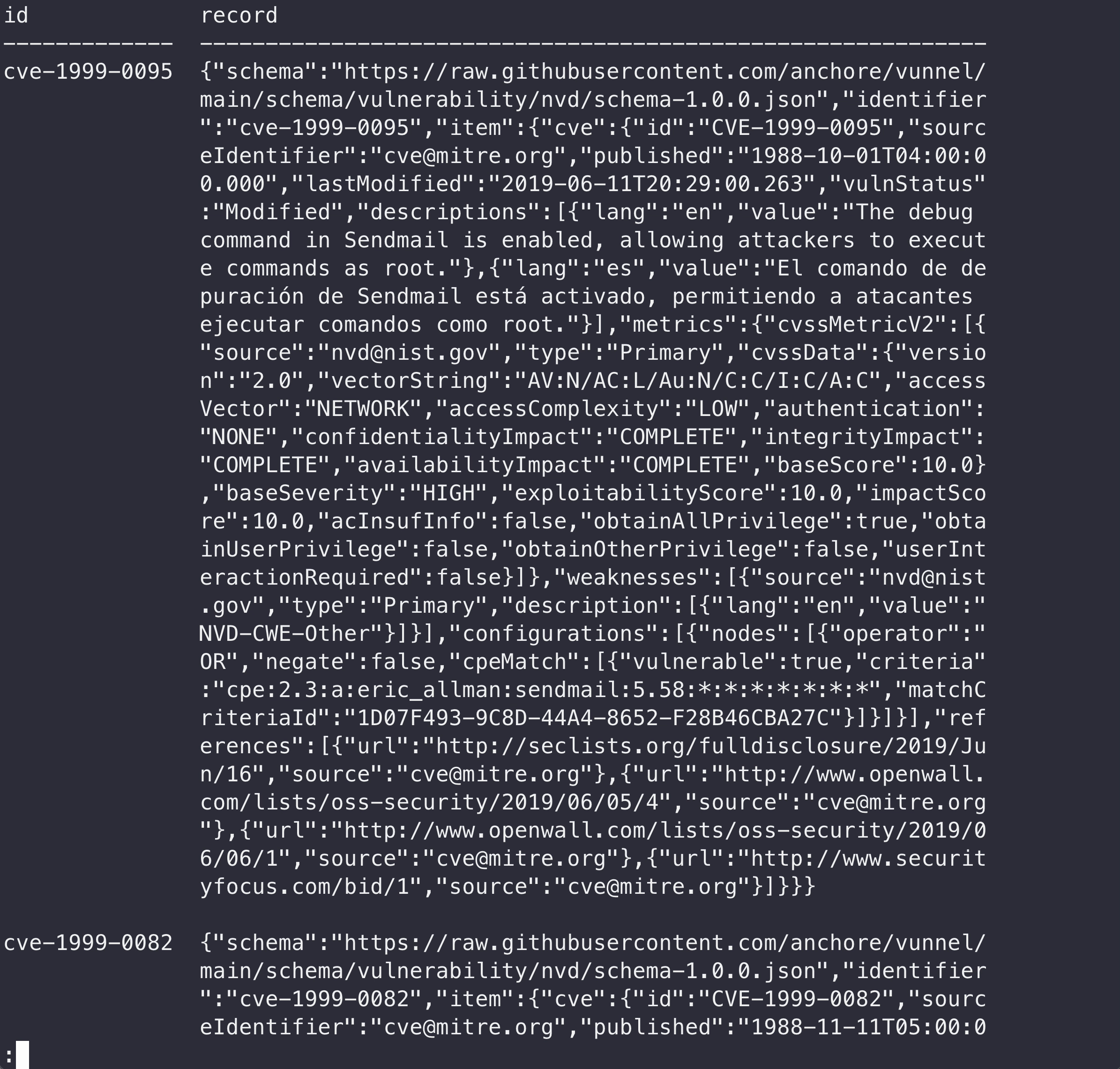
Download and process a provider:
$ vunnel run wolfi
2023-01-04 13:42:58 root [INFO] running wolfi provider
2023-01-04 13:42:58 wolfi [INFO] downloading Wolfi secdb https://packages.wolfi.dev/os/security.json
2023-01-04 13:42:59 wolfi [INFO] wrote 56 entries
2023-01-04 13:42:59 wolfi [INFO] recording workspace state
You will see the processed vulnerability data in the local ./data directory
$ tree data
data
└── wolfi
├── checksums
├── metadata.json
├── input
│ └── secdb
│ └── os
│ └── security.json
└── results
└── wolfi:rolling
├── CVE-2016-2781.json
├── CVE-2017-8806.json
├── CVE-2018-1000156.json
└── ...
Note: to get more verbose output, use -v, -vv, or -vvv (e.g. vunnel -vv run wolfi)
Delete existing input and result data for one or more providers:
$ vunnel clear wolfi
2023-01-04 13:48:31 root [INFO] clearing wolfi provider state
Example config file for changing application behavior:
# .vunnel.yaml
root: ./processed-data
log:
level: trace
providers:
wolfi:
request_timeout: 125
runtime:
existing_input: keep
existing_results: delete-before-write
on_error:
action: fail
input: keep
results: keep
retry_count: 3
retry_delay: 10
Use vunnel config to get a better idea of all of the possible configuration options.
FAQ
Can I implement a new provider?
Yes you can! See the provider docs for more information.
Why is it called "vunnel"?
This tool "funnels" vulnerability data into a single spot for easy processing... say "vulnerability data funnel" 100x fast enough and eventually it'll slur to "vunnel" :).
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Filter files by name, interpreter, ABI, and platform.
If you're not sure about the file name format, learn more about wheel file names.
Copy a direct link to the current filters
File details
Details for the file vunnel-0.55.2.tar.gz.
File metadata
- Download URL: vunnel-0.55.2.tar.gz
- Upload date:
- Size: 659.1 kB
- Tags: Source
- Uploaded using Trusted Publishing? Yes
- Uploaded via: uv/0.10.8 {"installer":{"name":"uv","version":"0.10.8","subcommand":["publish"]},"python":null,"implementation":{"name":null,"version":null},"distro":{"name":"Ubuntu","version":"24.04","id":"noble","libc":null},"system":{"name":null,"release":null},"cpu":null,"openssl_version":null,"setuptools_version":null,"rustc_version":null,"ci":true}
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
135dfcb12852e7b884581a87f2e45ed12d2b063e58ee55ab81b5ba3bdc5cee45
|
|
| MD5 |
a81b62fb8ff6ac7b3a2232ec692e4e91
|
|
| BLAKE2b-256 |
714bf620daa9c0f2addf909992351102f5abb5f0e2a5ef84925cca65808907f4
|
File details
Details for the file vunnel-0.55.2-py3-none-any.whl.
File metadata
- Download URL: vunnel-0.55.2-py3-none-any.whl
- Upload date:
- Size: 230.4 kB
- Tags: Python 3
- Uploaded using Trusted Publishing? Yes
- Uploaded via: uv/0.10.8 {"installer":{"name":"uv","version":"0.10.8","subcommand":["publish"]},"python":null,"implementation":{"name":null,"version":null},"distro":{"name":"Ubuntu","version":"24.04","id":"noble","libc":null},"system":{"name":null,"release":null},"cpu":null,"openssl_version":null,"setuptools_version":null,"rustc_version":null,"ci":true}
File hashes
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 |
5da07b5afde37b5309de411acf1ea854f79de9c0cc85db3cf12d48d0908c67a3
|
|
| MD5 |
1bfb7cea8f991dfdd83f18f2947459db
|
|
| BLAKE2b-256 |
10aef3c87349e4c0868ef6864ddfbf05a1a7cc4fbea5ce8b5c6f72dba17d82d7
|