OSINT automation for hackers.
Project description
BEE·bot
OSINT automation for hackers.
BBOT is a powerful and modular OSINT (Open Source Intelligence) framework designed to map the attack surface of an organization. With BBOT, you can execute the entire OSINT workflow with just a single command.
BBOT is inspired by Spiderfoot but takes it to the next level with features like multi-target scans, lightning-fast asyncio performance, and NLP-powered subdomain mutations. It offers a wide range of functionality, including subdomain enumeration, port scanning, web screenshots, vulnerability scanning, and much more. BBOT has over 80 modules and counting.
Whether you're a pentester, security researcher, or bug bounty hunter, BBOT simplifies and automates the OSINT process so you can focus on the fun part: hacking!
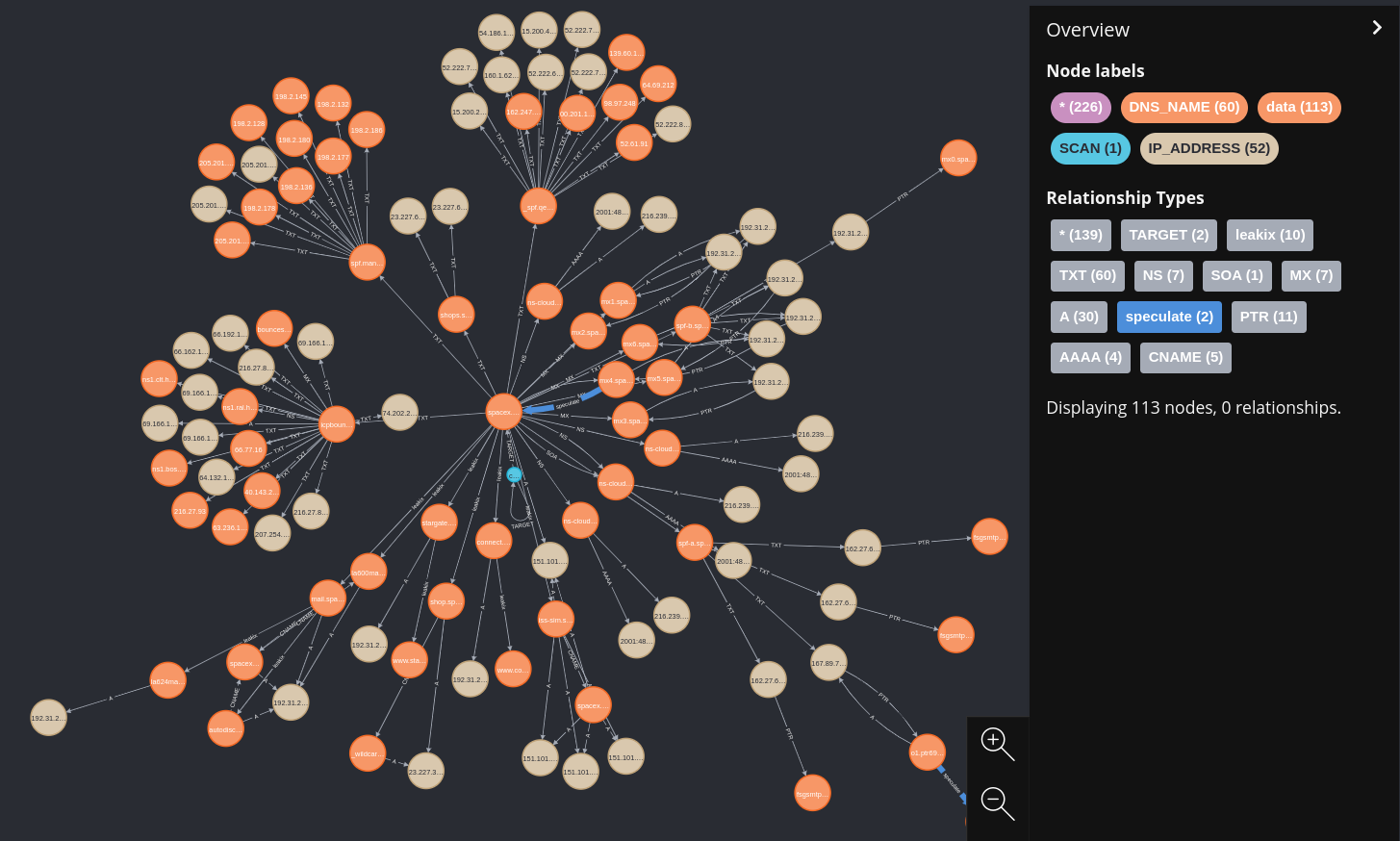
https://github.com/blacklanternsecurity/bbot/assets/20261699/ebf2a81e-7530-4a9e-922d-4e62eb949f35
Visualization courtesy of VivaGraphJS
Getting Started
Installation (pip)
Note: installing in a virtualenv (e.g. via pipx) is recommended. If you need help with installation, please refer to the wiki.
# Prerequisites:
# - Linux (Windows and macOS are *not* supported)
# - Python 3.9 or newer
# stable version
pip install bbot
# bleeding edge (dev branch)
pip install --pre bbot
bbot --help
Example Commands
Note: Scan output, logs, etc. are saved to ~/.bbot.
# subdomains
bbot -t evilcorp.com -f subdomain-enum
# subdomains (passive only)
bbot -t evilcorp.com -f subdomain-enum -rf passive
# subdomains + port scan + web screenshots
bbot -t evilcorp.com -f subdomain-enum -m naabu gowitness -n my_scan -o .
# subdomains + basic web scan (wappalyzer, robots.txt, iis shortnames, etc.)
bbot -t evilcorp.com -f subdomain-enum web-basic
# subdomains + web spider (search for emails, etc.)
bbot -t evilcorp.com -f subdomain-enum -c web_spider_distance=2 web_spider_depth=2
# everything at once because yes
# subdomains + emails + cloud + port scan + non-intrusive web + web screenshots + nuclei
bbot -t evilcorp.com -f subdomain-enum email-enum cloud-enum web-basic -m naabu gowitness nuclei --allow-deadly
# list modules
bbot -l
Using BBOT as a Python library
Synchronous
from bbot.scanner import Scanner
# any number of targets can be specified
scan = Scanner("example.com", "scanme.nmap.org", modules=["nmap", "sslcert"])
for event in scan.start():
print(event.json())
Asynchronous
from bbot.scanner import Scanner
async def main():
scan = Scanner("example.com", "scanme.nmap.org", modules=["nmap", "sslcert"])
async for event in scan.async_start():
print(event.json())
import asyncio
asyncio.run(main())
Targets
Targets seed a scan with initial data. You can specify an unlimited number of targets, either directly on the command line or in files (or both!). Targets can be any of the following:
- DNS_NAME (
evilcorp.com) - IP_ADDRESS (
1.2.3.4) - IP_RANGE (
1.2.3.0/24) - URL (
https://www.evilcorp.com) - EMAIL_ADDRESS (
bob@evilcorp.com)
For example, the following scan is totally valid:
# multiple targets
bbot -t evilcorp.com evilcorp.co.uk http://www.evilcorp.cn 1.2.3.0/24 other_targets.txt
Visit the wiki for more tips and tricks.
Docker
BBOT provides docker images, along with helper script bbot-docker.sh to persist your BBOT scan data.
# helper script
./bbot-docker.sh --help
# bleeding edge (dev)
docker run -it blacklanternsecurity/bbot --help
# stable
docker run -it blacklanternsecurity/bbot:stable --help
Usage
$ bbot --help
usage: bbot [-h] [--help-all] [-t TARGET [TARGET ...]] [-w WHITELIST [WHITELIST ...]] [-b BLACKLIST [BLACKLIST ...]] [--strict-scope] [-m MODULE [MODULE ...]] [-l]
[-em MODULE [MODULE ...]] [-f FLAG [FLAG ...]] [-rf FLAG [FLAG ...]] [-ef FLAG [FLAG ...]] [-om MODULE [MODULE ...]] [--allow-deadly] [-n SCAN_NAME] [-o DIR] [-c [CONFIG ...]]
[-v] [-d] [-s] [--force] [-y] [--dry-run] [--current-config] [--no-deps | --force-deps | --retry-deps | --ignore-failed-deps | --install-all-deps] [-a] [--version]
Bighuge BLS OSINT Tool
options:
-h, --help show this help message and exit
--help-all Display full help including module config options
Target:
-t TARGET [TARGET ...], --targets TARGET [TARGET ...]
Targets to seed the scan
-w WHITELIST [WHITELIST ...], --whitelist WHITELIST [WHITELIST ...]
What's considered in-scope (by default it's the same as --targets)
-b BLACKLIST [BLACKLIST ...], --blacklist BLACKLIST [BLACKLIST ...]
Don't touch these things
--strict-scope Don't consider subdomains of target/whitelist to be in-scope
Modules:
-m MODULE [MODULE ...], --modules MODULE [MODULE ...]
Modules to enable. Choices: affiliates,anubisdb,asn,azure_tenant,badsecrets,bevigil,binaryedge,bucket_aws,bucket_azure,bucket_digitalocean,bucket_firebase,bucket_gcp,builtwith,bypass403,c99,censys,certspotter,crobat,crt,dnscommonsrv,dnsdumpster,dnszonetransfer,emailformat,ffuf,ffuf_shortnames,fingerprintx,fullhunt,generic_ssrf,github,gowitness,hackertarget,host_header,httpx,hunt,hunterio,iis_shortnames,ipneighbor,ipstack,leakix,masscan,massdns,naabu,nmap,ntlm,nuclei,otx,paramminer_cookies,paramminer_getparams,paramminer_headers,passivetotal,pgp,rapiddns,riddler,robots,secretsdb,securitytrails,shodan_dns,skymem,smuggler,social,sslcert,subdomain_hijack,sublist3r,telerik,threatminer,url_manipulation,urlscan,vhost,viewdns,virustotal,wafw00f,wappalyzer,wayback,zoomeye
-l, --list-modules List available modules.
-em MODULE [MODULE ...], --exclude-modules MODULE [MODULE ...]
Exclude these modules.
-f FLAG [FLAG ...], --flags FLAG [FLAG ...]
Enable modules by flag. Choices: active,affiliates,aggressive,cloud-enum,deadly,email-enum,iis-shortnames,passive,portscan,report,safe,service-enum,slow,social-enum,subdomain-enum,subdomain-hijack,web-basic,web-paramminer,web-screenshots,web-thorough
-rf FLAG [FLAG ...], --require-flags FLAG [FLAG ...]
Only enable modules with these flags (e.g. -rf passive)
-ef FLAG [FLAG ...], --exclude-flags FLAG [FLAG ...]
Disable modules with these flags. (e.g. -ef aggressive)
-om MODULE [MODULE ...], --output-modules MODULE [MODULE ...]
Output module(s). Choices: asset_inventory,csv,http,human,json,neo4j,python,web_report,websocket
--allow-deadly Enable the use of highly aggressive modules
Scan:
-n SCAN_NAME, --name SCAN_NAME
Name of scan (default: random)
-o DIR, --output-dir DIR
-c [CONFIG ...], --config [CONFIG ...]
custom config file, or configuration options in key=value format: 'modules.shodan.api_key=1234'
-v, --verbose Be more verbose
-d, --debug Enable debugging
-s, --silent Be quiet
--force Run scan even if module setups fail
-y, --yes Skip scan confirmation prompt
--dry-run Abort before executing scan
--current-config Show current config in YAML format
Module dependencies:
Control how modules install their dependencies
--no-deps Don't install module dependencies
--force-deps Force install all module dependencies
--retry-deps Try again to install failed module dependencies
--ignore-failed-deps Run modules even if they have failed dependencies
--install-all-deps Install dependencies for all modules
Agent:
Report back to a central server
-a, --agent-mode Start in agent mode
Misc:
--version show BBOT version and exit
BBOT Config
Additional config options (such as API keys, rate limits, user-agent, etc.) can be passed to BBOT via its YAML config. BBOT loads its config beginning from ~/.config/bbot:
~/.config/bbot/bbot.yml<-- Use this one as your main config~/.config/bbot/secrets.yml<-- Use this one for sensitive stuff like API keys- command line (
--config) <-- Use this to specify a custom.ymlor override individual config options
These config files will be automatically created for you when you first run BBOT.
Command-line arguments take precedence over all others. You can give BBOT a custom config file with --config myconf.yml, or individual arguments like this: --config http_proxy=http://127.0.0.1:8080 modules.shodan_dns.api_key=1234. To display the full and current BBOT config, including any command-line arguments, use bbot --current-config.
Note that placing the following in bbot.yml:
modules:
shodan:
api_key: deadbeef
Is the same as:
bbot --config modules.shodan.api_key=deadbeef
For explanations of config options, see defaults.yml or the wiki
Output
By default, BBOT saves its output in TXT, JSON, and CSV formats. You can enable other output modules with --output-module.
# tee to a file
bbot -f subdomain-enum -t evilcorp.com | tee evilcorp.txt
# output to JSON
bbot --output-module json -f subdomain-enum -t evilcorp.com | jq
# output asset inventory in current directory
bbot -o . --output-module asset_inventory -f subdomain-enum -t evilcorp.com
For every scan, BBOT generates a unique and mildly-entertaining name like demonic_jimmy. Output for that scan, including scan stats and any gowitness screenshots, etc., are saved to a folder by that name in ~/.bbot/scans. The most recent 20 scans are kept, and older ones are removed. You can change the location of BBOT's output with --output, and you can also pick a custom scan name with --name.
If you reuse a scan name, it will append to its original output files and leverage the previous.
Neo4j
Neo4j is the funnest (and prettiest) way to view and interact with BBOT data.
- You can get Neo4j up and running with a single docker command:
docker run -p 7687:7687 -p 7474:7474 -v "$(pwd)/data/:/data/" -e NEO4J_AUTH=neo4j/bbotislife neo4j
- After that, run bbot with
--output-modules neo4j
bbot -f subdomain-enum -t evilcorp.com --output-modules neo4j
- Browse data at http://localhost:7474
Modules
Note: You can find more fun and interesting modules at the Module Playground. For instructions on how to install these other modules, see the wiki.
To see modules' options (how to change wordlists, thread count, etc.), use --help-all.
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| Module | Type | Needs | Description | Flags | Produced Events |
| | | API | | | |
| | | Key | | | |
+======================+==========+=========+==========================================+==========================================+==========================================+
| badsecrets | scan | | Library for detecting known or weak | active,safe,web-basic,web-thorough | FINDING,VULNERABILITY |
| | | | secrets across many web frameworks | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| bucket_aws | scan | | Check for S3 buckets related to target | active,cloud-enum,safe,web-basic,web- | FINDING,STORAGE_BUCKET |
| | | | | thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| bucket_azure | scan | | Check for Azure storage blobs related to | active,cloud-enum,safe,web-basic,web- | FINDING,STORAGE_BUCKET |
| | | | target | thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| bucket_digitalocean | scan | | Check for DigitalOcean spaces related to | active,cloud-enum,safe,slow,web-thorough | FINDING,STORAGE_BUCKET |
| | | | target | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| bucket_firebase | scan | | Check for open Firebase databases | active,cloud-enum,safe,web-basic,web- | FINDING,STORAGE_BUCKET |
| | | | related to target | thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| bucket_gcp | scan | | Check for Google object storage related | active,cloud-enum,safe,web-basic,web- | FINDING,STORAGE_BUCKET |
| | | | to target | thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| bypass403 | scan | | Check 403 pages for common bypasses | active,aggressive,web-thorough | FINDING |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| dnszonetransfer | scan | | Attempt DNS zone transfers | active,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| ffuf | scan | | A fast web fuzzer written in Go | active,aggressive,deadly | URL_UNVERIFIED |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| ffuf_shortnames | scan | | Use ffuf in combination IIS shortnames | active,aggressive,iis-shortnames,web- | URL_UNVERIFIED |
| | | | | thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| fingerprintx | scan | | Fingerprint exposed services like RDP, | active,safe,service-enum,slow | PROTOCOL |
| | | | SSH, MySQL, etc. | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| generic_ssrf | scan | | Check for generic SSRFs | active,aggressive,web-thorough | VULNERABILITY |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| gowitness | scan | | Take screenshots of webpages | active,safe,web-screenshots | TECHNOLOGY,URL,URL_UNVERIFIED,WEBSCREENS |
| | | | | | HOT |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| host_header | scan | | Try common HTTP Host header spoofing | active,aggressive,web-thorough | FINDING |
| | | | techniques | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| httpx | scan | | Visit webpages. Many other modules rely | active,cloud-enum,safe,social- | HTTP_RESPONSE,URL |
| | | | on httpx | enum,subdomain-enum,web-basic,web- | |
| | | | | thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| hunt | scan | | Watch for commonly-exploitable HTTP | active,safe,web-basic,web-thorough | FINDING |
| | | | parameters | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| iis_shortnames | scan | | Check for IIS shortname vulnerability | active,iis-shortnames,safe,web- | URL_HINT |
| | | | | basic,web-thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| masscan | scan | | Port scan IP subnets with masscan | active,aggressive,portscan | OPEN_TCP_PORT |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| naabu | scan | | Execute port scans with naabu | active,aggressive,portscan,web-thorough | OPEN_TCP_PORT |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| nmap | scan | | Execute port scans with nmap | active,aggressive,portscan,web-thorough | OPEN_TCP_PORT |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| ntlm | scan | | Watch for HTTP endpoints that support | active,safe,web-basic,web-thorough | DNS_NAME,FINDING |
| | | | NTLM authentication | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| nuclei | scan | | Fast and customisable vulnerability | active,aggressive,deadly | FINDING,VULNERABILITY |
| | | | scanner | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| paramminer_cookies | scan | | Smart brute-force to check for common | active,aggressive,slow,web-paramminer | FINDING |
| | | | HTTP cookie parameters | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| paramminer_getparams | scan | | Use smart brute-force to check for | active,aggressive,slow,web-paramminer | FINDING |
| | | | common HTTP GET parameters | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| paramminer_headers | scan | | Use smart brute-force to check for | active,aggressive,slow,web-paramminer | FINDING |
| | | | common HTTP header parameters | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| robots | scan | | Look for and parse robots.txt | active,safe,web-basic,web-thorough | URL_UNVERIFIED |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| secretsdb | scan | | Detect common secrets with secrets- | active,safe,web-basic,web-thorough | FINDING |
| | | | patterns-db | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| smuggler | scan | | Check for HTTP smuggling | active,aggressive,slow,web-thorough | FINDING |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| social | scan | | Look for social media links in webpages | active,safe,social-enum | SOCIAL |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| sslcert | scan | | Visit open ports and retrieve SSL | active,affiliates,email- | DNS_NAME,EMAIL_ADDRESS |
| | | | certificates | enum,safe,subdomain-enum,web-basic,web- | |
| | | | | thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| subdomain_hijack | scan | | Detect hijackable subdomains | active,cloud-enum,safe,subdomain- | FINDING |
| | | | | enum,subdomain-hijack,web-basic,web- | |
| | | | | thorough | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| telerik | scan | | Scan for critical Telerik | active,aggressive,slow,web-thorough | FINDING,VULNERABILITY |
| | | | vulnerabilities | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| url_manipulation | scan | | Attempt to identify URL parsing/routing | active,aggressive,web-thorough | FINDING |
| | | | based vulnerabilities | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| vhost | scan | | Fuzz for virtual hosts | active,aggressive,deadly,slow | DNS_NAME,VHOST |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| wafw00f | scan | | Web Application Firewall Fingerprinting | active,aggressive | WAF |
| | | | Tool | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| wappalyzer | scan | | Extract technologies from web responses | active,safe,web-basic,web-thorough | TECHNOLOGY |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| affiliates | scan | | Summarize affiliate domains at the end | affiliates,passive,report,safe | |
| | | | of a scan | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| anubisdb | scan | | Query jldc.me's database for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| asn | scan | | Query ripe and bgpview.io for ASNs | passive,report,safe,subdomain-enum | ASN |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| azure_tenant | scan | | Query Azure for tenant sister domains | affiliates,passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| bevigil | scan | X | Retrieve OSINT data from mobile | passive,safe,subdomain-enum | DNS_NAME,URL_UNVERIFIED |
| | | | applications using BeVigil | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| binaryedge | scan | X | Query the BinaryEdge API | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| builtwith | scan | X | Query Builtwith.com for subdomains | affiliates,passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| c99 | scan | X | Query the C99 API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| censys | scan | X | Query the Censys API | email-enum,passive,safe,subdomain-enum | DNS_NAME,EMAIL_ADDRESS,IP_ADDRESS,OPEN_P |
| | | | | | ORT,PROTOCOL |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| certspotter | scan | | Query Certspotter's API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| crobat | scan | | Query Project Crobat for subdomains | passive,safe | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| crt | scan | | Query crt.sh (certificate transparency) | passive,safe,subdomain-enum | DNS_NAME |
| | | | for subdomains | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| dnscommonsrv | scan | | Check for common SRV records | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| dnsdumpster | scan | | Query dnsdumpster for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| emailformat | scan | | Query email-format.com for email | email-enum,passive,safe | EMAIL_ADDRESS |
| | | | addresses | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| fullhunt | scan | X | Query the fullhunt.io API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| github | scan | X | Query Github's API for related | passive,safe,subdomain-enum | URL_UNVERIFIED |
| | | | repositories | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| hackertarget | scan | | Query the hackertarget.com API for | passive,safe,subdomain-enum | DNS_NAME |
| | | | subdomains | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| hunterio | scan | X | Query hunter.io for emails | email-enum,passive,safe,subdomain-enum | DNS_NAME,EMAIL_ADDRESS,URL_UNVERIFIED |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| ipneighbor | scan | | Look beside IPs in their surrounding | aggressive,passive,subdomain-enum | IP_ADDRESS |
| | | | subnet | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| ipstack | scan | X | Query IPStack's API for GeoIP | passive,safe | GEOLOCATION |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| leakix | scan | | Query leakix.net for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| massdns | scan | | Brute-force subdomains with massdns | aggressive,passive,slow,subdomain-enum | DNS_NAME |
| | | | (highly effective) | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| otx | scan | | Query otx.alienvault.com for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| passivetotal | scan | X | Query the PassiveTotal API for | passive,safe,subdomain-enum | DNS_NAME |
| | | | subdomains | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| pgp | scan | | Query common PGP servers for email | email-enum,passive,safe | EMAIL_ADDRESS |
| | | | addresses | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| rapiddns | scan | | Query rapiddns.io for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| riddler | scan | | Query riddler.io for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| securitytrails | scan | X | Query the SecurityTrails API for | passive,safe,subdomain-enum | DNS_NAME |
| | | | subdomains | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| shodan_dns | scan | X | Query Shodan for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| skymem | scan | | Query skymem.info for email addresses | email-enum,passive,safe | EMAIL_ADDRESS |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| sublist3r | scan | | Query sublist3r's API for subdomains | passive,safe | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| threatminer | scan | | Query threatminer's API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| urlscan | scan | | Query urlscan.io for subdomains | passive,safe,subdomain-enum | DNS_NAME,URL_UNVERIFIED |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| viewdns | scan | | Query viewdns.info's reverse whois for | affiliates,passive,safe | DNS_NAME |
| | | | related domains | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| virustotal | scan | X | Query VirusTotal's API for subdomains | passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| wayback | scan | | Query archive.org's API for subdomains | passive,safe,subdomain-enum | DNS_NAME,URL_UNVERIFIED |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| zoomeye | scan | X | Query ZoomEye's API for subdomains | affiliates,passive,safe,subdomain-enum | DNS_NAME |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| asset_inventory | output | | Output to an asset inventory style | | IP_ADDRESS,OPEN_TCP_PORT |
| | | | flattened CSV file | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| csv | output | | Output to CSV | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| http | output | | Send every event to a custom URL via a | | |
| | | | web request | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| human | output | | Output to text | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| json | output | | Output to JSON | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| neo4j | output | | Output to Neo4j | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| python | output | | Output via Python API | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| web_report | output | | Create a markdown report with web assets | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| websocket | output | | Output to websockets | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| aggregate | internal | | Summarize statistics at the end of a | passive,safe | |
| | | | scan | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| excavate | internal | | Passively extract juicy tidbits from | passive | URL_UNVERIFIED |
| | | | scan data | | |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
| speculate | internal | | Derive certain event types from others | passive | DNS_NAME,FINDING,IP_ADDRESS,OPEN_TCP_POR |
| | | | by common sense | | T |
+----------------------+----------+---------+------------------------------------------+------------------------------------------+------------------------------------------+
Acknowledgements
Thanks to all these amazing people for contributing to BBOT! :heart:
If you have an idea for a feature or run into bugs of any kind, please submit an issue or a PR. We welcome contributions!
Special thanks to the following people who made BBOT possible:
- @TheTechromancer for creating BBOT
- @liquidsec for his extensive work on BBOT's web hacking features
- Steve Micallef (@smicallef) for creating Spiderfoot
- @kerrymilan for his Neo4j and Ansible expertise
- Aleksei Kornev (@alekseiko) for allowing us ownership of the bbot Pypi repository <3
See also: Release History
Project details
Release history Release notifications | RSS feed
Download files
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Source Distribution
Built Distribution
Hashes for bbot-1.0.5.1815rc0-py3-none-any.whl
| Algorithm | Hash digest | |
|---|---|---|
| SHA256 | fdec4fb0af9772cbe46d9baaa023a8635ce20a6b3bbd40f446fc109860021e33 |
|
| MD5 | 5e423d854528af15fd691f227aa2a58d |
|
| BLAKE2b-256 | aa68820b5dfc62c6e21f6245fe11b07145528aa908a3911c6e4e8e1ace8acbe4 |